security report
security report news search results
Developer news items we found relating to security report
34 results
API Security Perspectives 2025 report from Kong Inc
Monday, December 30, 2024 by Richard Harris
Kong Inc. released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report which highlights today’s API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern a...

Generative AI in Application Security report from Checkmarx
Monday, August 12, 2024 by Richard Harris
Checkmarx, the in-cloud-native application security provider, has published its Seven Steps to Safely Use Generative AI in Application Security report, which analyzes key concerns, usage patterns, and buying behaviors relating to the use of AI in enterprise application development. The global study exposed the tension between the need to empower both...

Secure software development insights from The Linux Foundation
Monday, February 5, 2024 by Richard Harris
The Linux Foundation published a new report, Maintainer Perspectives on Open Source Software Security, based on a survey of OSS maintainers and core contributors, to understand perspectives on OSS security and the uptake and adoption of security best practices by maintainers, core contributors, end users, and other members of the OSS ecosystem. Maintainer Perspective...

App security threat report results from Digital Ai
Thursday, October 19, 2023 by Richard Harris
Digital.ai announced the results of its 1st annual Application Security Threat Report, illuminating and quantifying the risks to applications in the wild. The results reveal that 57% of all monitored apps are under attack, with gaming (63%) and FinServ (62%) the most likely to be attacked. The study found no correlation between an app’s popularity and likelihood o...

One Identity Safeguard now supports Microsoft SQL Server
Friday, May 1, 2020 by Brittany Hainzinger
One Identity announced that its One Identity Safeguard solution now supports Microsoft SQL Server 2017 and SQL Server 2019 database environments. Microsoft was positioned as a Leader in the 2019 Gartner Magic Quadrant for Operational Database Management Systems*. With One Identity Safeguard, organizations can for the first time securely manage, monitor, record and audit...

Cloud computing security report 2019 is out from CSA
Thursday, August 8, 2019 by Richard Harris
The Cloud Security Alliance (CSA) defines standards, certifications, and best practices to help ensure a secure cloud computing environment. The CSA has released "Top Threats to Cloud Computing: The Egregious Eleven", a report which re-examines the risks inherent with cloud security and takes a new approach, examining the problems inherent in configu...

This DDoS report could help you avoid a security disaster
Thursday, January 10, 2019 by Austin Harris
MazeBolt Technologies, the company offering DDoS threat assessment, has released ”The State of DDoS Protection Report,” the first global independent report about DDoS mitigation effectiveness. ”Since DDoS mitigation started in the late 1990s, enterprises have had little to no visibility on how effective their DDoS mitigation actually is,” said...

PCE Supercluster now offered by Illumio
Tuesday, January 8, 2019 by Austin Harris
Illumio, a cybersecurity company delivering micro-segmentation, announced full availability of PCE Supercluster designed for enterprise-scale real-time application dependency mapping and micro-segmentation deployments. PCE Supercluster, which is currently in use by some of the largest organizations in the world, makes Illumio the first company to offer a micro-segmentat...

Privacy for Android boosted with decentralized VPN
Sunday, January 6, 2019 by Austin Harris
Mysterium Network, an open-source, not-for-profit foundation reinventing internet privacy, security, and freedom, has announced the release of the Mysterium VPN app for Android, which is now available on the Google Play store. The app, which was released today and is also available for Windows and macOS, will allow users to participate in the world’s first dece...

Gamification can transform your software security program
Tuesday, December 18, 2018 by Pieter Danhieux
No matter the organization, or indeed their individual circumstances, there is one problem I have identified time and time again over the course of my career: AppSec managers, CISOs, CIOs and cybersecurity experts all over the world are rarely able to positively engage their dev teams on security best practice and training. It’s a source of conflict between teams,...

AI for cybersecurity
Tuesday, November 27, 2018 by Richard Harris
As organizations struggle to deal with the growing sophistication of hackers and the influx in data breaches, it's becoming clear that AI could be a critical tool for automatically defending applications from cyber attacks - but there are challenges to overcome. Ivan Novikov, the CEO of AI security company Wallarm, offers some insight below on how AI can be utilized...

Container security considerations for developers
Monday, October 29, 2018 by Richard Harris
On the path to a secure digital business, secure service containers bring the best of agility and security to development teams – a growing concern for companies from startups to the Fortune 500. By moving the security concern out of the application layer into an encompassing container platform, one provides a very elegant solution to significantly reduced attack ...

Data warehousing company Snowflake garners $450M in funding
Tuesday, October 16, 2018 by Austin Harris
Snowflake Computing says it has closed $450 million in additional growth funding led by Sequoia Capital. The remainder of Snowflake’s existing investors also participated: Altimeter Capital, Capital One Growth Ventures, ICONIQ Capital, Madrona Venture Group, Redpoint Ventures, Sutter Hill Ventures and Wing Ventures. New investor Meritech Capital also joined t...

NGINX gets new capabilities to help app teams develop and scale
Monday, October 15, 2018 by Richard Harris
NGINX has released new enhancements to the NGINX Application Platform - including new releases of NGINX Plus, NGINX Controller, and NGINX Unit. These new releases aim to improve NGINX’s solution in the application delivery controller (ADC) market, as well as introduce new solutions in the API management and service mesh markets. NGINX provides a single platfo...

Enterprise security report says mobile workers put data at risk
Wednesday, October 10, 2018 by Austin Harris
According to a new study titled Greatest Mobile Security Threats in the Enterprise, a significant lack of visibility into devices and networks is putting businesses at risk for data leakage and phishing attacks. The study, conducted by Enterprise Mobility Exchange and commissioned by NetMotion Software, showed that nearly 50 percent of mobile workers spend the majority ...

Why developers run away from security updates
Monday, April 16, 2018 by Richard Harris
Veracode, Inc. has released new data that shines a light on the discrepancy between component security and hygiene. According to the research conducted with Vanson Bourne, only 52 percent of developers using commercial or open source components in their applications update those components when a new security vulnerability is announced. This highlights organizations’ la...
Dataguise recognized in MarketsandMarkets datacentric security report
Thursday, January 25, 2018 by Austin Harris
Dataguise was cited a new report titled Data-Centric Security Market Global Forecast to 2022 published by IT research firm MarketsandMarkets. In the report, analysts forecast the global data-centric security market to grow from USD $1.79 Billion in 2016 to USD $5.83 Billion by 2022, at a compound annual growth rate (CAGR) of 23.1%. The report indicates that sensitive da...
IoT Cybersecurity is top concern says BlackBerry report
Friday, October 20, 2017 by Richard Harris
BlackBerry Limited has announced findings from a new global research whitepaper, which surveyed IT decision makers on corporate IoT deployments. Conducted by 451 Research, the whitepaper titled, “Securing the Enterprise of Things: Opportunity for securing IoT with a unified platform emerging as IoT popularity grows,” reveals that huge opportunities are balanced against ...

DevSecOps will help security and developers play nice
Thursday, June 15, 2017 by Richard Harris
Veracode, a security software company acquired by CA Technologies, has announced the results of a study examining the relationships between application developers and security teams.The study, conducted in conjunction with Enterprise Strategy Group (ESG), shows that despite the pervasive belief that security and development teams have conflicting priorities, initiatives...

Scanning JavaScript for vulnerabilities: How the impossible is now possible
Friday, January 13, 2017 by Matt Howard
Javascript is everywhere, and it's awesome! But the world most popular language can be riddled with problems if you aren't a careful programmer.There is a saying that speaks to the incredible popularity of JavaScript as a programming language and it goes like this: “any application that can be written in JavaScript, will eventually be written in JavaScript.” The we...

Cyberbit's SOC 3D automation updates and what you should know
Tuesday, December 20, 2016 by Richard Harris
Cyberbit just announced a new version of its SOC 3D automation and orchestration platform that increases productivity and effectiveness of the SOC and substantially reduces incident response times. The new platform integrates with all major SIEM and security solutions, automates SOC runbooks and workflows, and prioritizes incidents according to their business impact. It...

Tufin extends Check Point R80 security management
Monday, December 19, 2016 by Richard Harris
Tufin, a network security policy orchestration solutions, has announced support for Check Point R80 Security Management, delivering end-to-end change automation and continuous policy compliance for joint customers across hybrid networks. With Tufin, Check Point users who are currently deploying or plan to deploy R80 Security Management can extend the benefits of consoli...

Humans are still the biggest threat to cyber security report shows
Saturday, December 17, 2016 by Austin Harris
Global technology company Nuix have released the findings from its third annual survey of corporate information security practitioners who almost universally agreed that human behavior was their largest security threat. While businesses were investing to develop broad and mature cybersecurity capabilities, many survey respondents were uncertain about the most effective ...

Veris Group steps up it's advanced security game with Endgame
Friday, December 16, 2016 by Austin Harris
Endgame has announced that Veris Group's Adaptive Threat Division (ATD), a provider in adversary simulation and detection services, will utilize Endgame's endpoint detection and response platform to enhance detection, response, and threat hunting capabilities to eliminate security threats faster and with greater accuracy for customers.This partnership leverages Endgame'...
New Security Report 2016 shows 64 percent of millennials experienced a comprised account hack
Thursday, November 17, 2016 by Richard Harris
TeleSign has released its Consumer Account Security Report 2016, providing insight into consumer sentiments on online security and the value they place on their digital lives. Of the 1,300 U.S. consumers surveyed, nearly a third report the value of their online life at $100,000 to priceless. Further, more than half of the respondents surveyed (55 percent) place the onus...

Paving the way to smarter phone security
Wednesday, October 19, 2016 by Robert Capps
75 million Smartphone users admit that while they are afraid of cyber attacks, they have not set a password for their smartphones according to the latest TransUnion’s Cyber Security Survey. While at first glance, this seems completely alarming and the ramifications could result in identity theft, it is also not surprising as consumers are not technologists and they just...

The use of vulnerable open source components putting more software at risk
Tuesday, October 18, 2016 by Richard Harris
Veracode has released the findings in its annual State of Software Security Report (SoSS). The seventh edition of the report presents metrics drawn from code-level analysis of billions of lines of code across 300,000 assessments performed over the last 18 months. The report revealed that the continued and persistent use of components in software development is creating ...

New Security Report Reveals Increased Threat for Mobile Applications
Sunday, February 21, 2016 by Stuart Parkerson
According to a new cyber security report, mobile applications increasingly have become top security threats plaguing enterprises over the past year. The details are outlined in the recently published Hewlett Packard Enterprise (HPE) Cyber Risk Report 2016.As the company points out in the report, traditional network perimeters are disappearing allowing attack surfaces to...
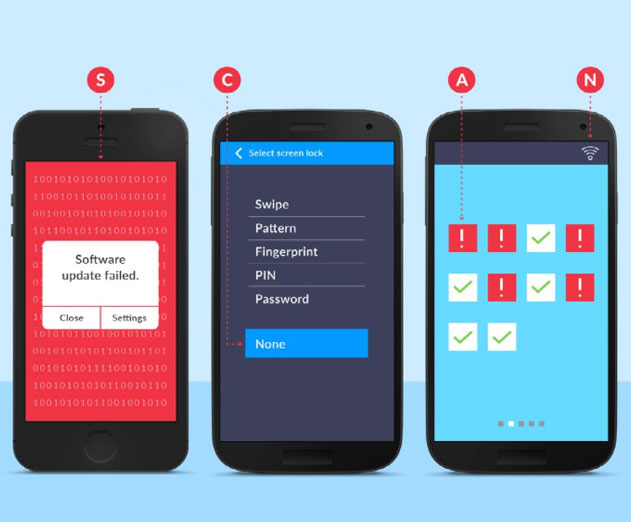
One in Four Android Apps Have High Risk Security Flaws
Friday, February 12, 2016 by Stuart Parkerson
Mobile developers continue to battle security issues with their apps according to a new report by NowSecure. The annual report, 2016 NowSecure Mobile Security Report, provides insight into the current state of mobile security. According to the report a quarter of Android apps have at least one high risk security flaw, 35 percent of communications sent by mobile dev...

New Mobile Security Report Shows Most Apps Have Critical Vulnerabilities
Tuesday, November 10, 2015 by Richard Harris
Checkmarx and AppSec Labs have released a new mobile app security titled “The State of Mobile Application Security 2014-2015”. Among the findings of the report is that the typical app is exposed to an average of 9 different vulnerabilities. The report also indicates in situations where vulnerabilities are built into the code or application logic, the vulnerability of iO...

New Report Highlights Wide Ranging Cybersecurity Challenges
Wednesday, September 2, 2015 by Richard Harris
Cybersecurity Ventures has released its Cybersecurity Market Report for Q3 2015 which provides an overview of software development and application security trends, statistics, best practices, and resources. Highlights of the report include:- “The SANS Institute 2015 State of Application Security Report” states that many information security engineers don’t understa...

Why DDoS Attacks Have Doubled in the past Year
Saturday, August 22, 2015 by Stuart Parkerson
Akamai Technologies has released its Q2 2015 State of the Internet – Security Report. This quarter’s report, which provides analysis and insight into the global cloud security threat landscape. Most notably, the data show the threat posed by distributed denial of service (DDoS) and web application attacks continues to grow each quarter.John Summers, vice president, Clou...
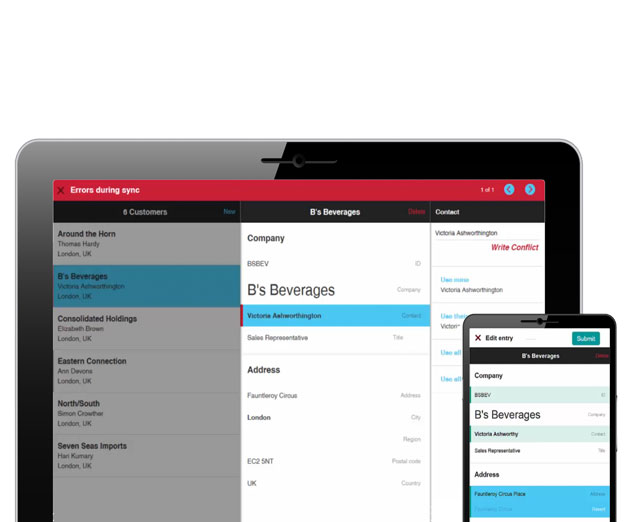
New Alpha Anywhere Version 3.0 Offers Cross Platform Offline Mobile Business Applications
Monday, October 6, 2014 by Stuart Parkerson
Alpha Software Corporation has announced its application development and deployment environment now offers built-in offline support, without added time or cost. This built-in capability in Alpha Anywhere 3.0 allows a transactional business app to operate effectively while disconnected from a network.With full featured mobile off-line availability, users can work anywher...

Sophos Security Report for 2013
Wednesday, December 5, 2012 by Richard Harris
Along with all of the other challenges in the mobile market coming in 2013, I think security will be up front and center for a lot of marketplaces, manufacturers, and developers.Sophos just released their security report for 2013 and reports on many vulnerabilities across the entire computing platform, with android being one of the largest concerns due to its growing nu...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|