Secure software development insights from The Linux Foundation
Monday, February 5, 2024

|
Richard Harris |
The Linux Foundation's recent survey-based insights report 'Maintainer Perspectives on Open Source Software Security' is available now. It was based on a survey of OSS maintainers and core contributors, to understand perspectives on OSS security and the uptake and adoption of security best practices.
The Linux Foundation published a new report, Maintainer Perspectives on Open Source Software Security, based on a survey of OSS maintainers and core contributors, to understand perspectives on OSS security and the uptake and adoption of security best practices by maintainers, core contributors, end users, and other members of the OSS ecosystem.
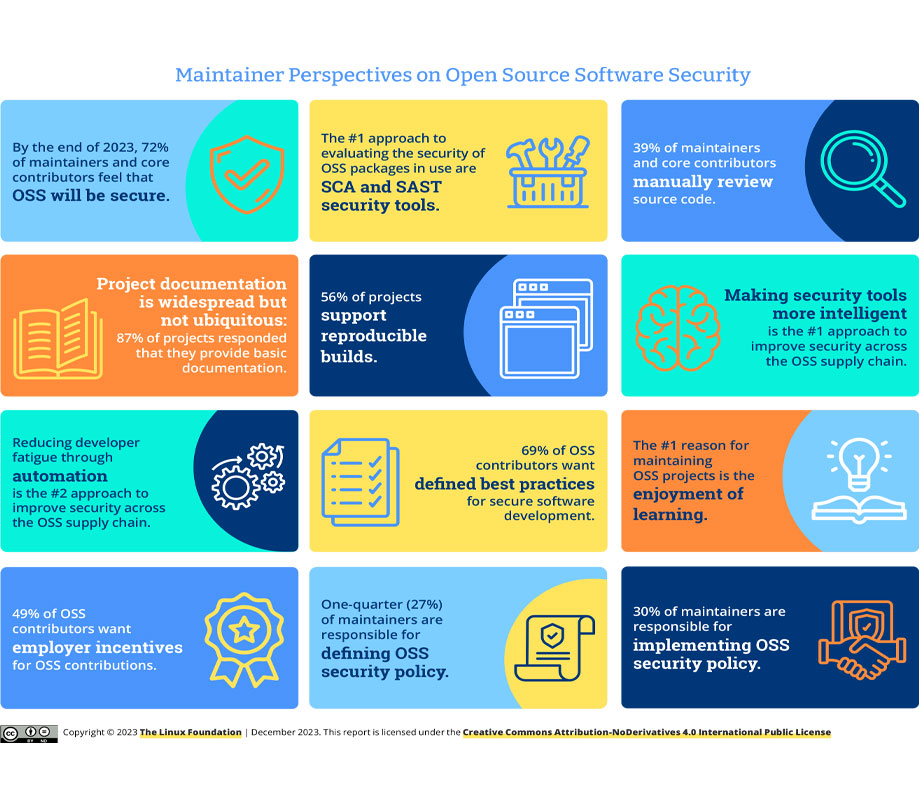
Maintainer Perspectives on Open Source Software Security report findings:
- The top approach for evaluating the security of OSS packages is the use of software composition analysis (SCA) and static application security testing (SAST) tools
- 39% of maintainers and core contributors still engage in manual code review
- Making security tools more intelligent emerges as the primary approach to improving security across the OSS supply chain. This includes leveraging advanced technologies like machine learning to enhance threat detection and response mechanisms
- The second most favored approach to improving security is reducing developer fatigue through automation
On using software composition analysis (SCA) and static application security testing (SAST) tools to evaluate the security of OSS packages, Varun Badhwar, CEO and co-founder of Endor Labs said: "SCA tools are insufficient because they only focus on two challenges - license and vulnerability compliance. And the way they address one of those two risks, vulnerability management, can actually make developers less productive because there’s no context into which vulnerabilities are reachable in the enterprise, causing developers to waste time patching components that can be deprioritized as they don’t impact the application."

Survey-based Insights from maintainers regarding how they address best practices for Secure Software Development
"SCA tools also suffer from three main shortcomings:
- They do not help developers select secure and high-quality dependencies. Without this, organizations quickly stack up their technical and security debt, which is hard to address later.
- They only track a single and lagging risk vector - known vulnerabilities. Known vulnerabilities are typically bugs in well-meaning developers’ code, and miss multiple categories of attacks from malicious developers that are rapidly increasing in scale and sophistication.
- They often lack context into transitive dependencies (where 95% of vulnerabilities are) and into how code is actually being used. Typically SCA tools will only filter security alerts based on severity, which leads to developers chasing a vulnerability because of its critical status, despite it not being an actual threat, because it’s unreachable or in test scope.
They also do not consider operational risk
This helps explain why, according to the log4j report released by the Department of Homeland Security Cyber Safety Review Board, at least one government agency spent 33,000 hours responding to the log4j vulnerability. As the authors noted, security teams simply can’t identify where the errant software exists within the environment.
Newer program analysis and code and pipeline governance technologies can help enterprises understand how code is actually being used in their organization, and which vulnerabilities within their code are actually dangerous and reachable. They can help developers prioritize fixes into what needs attention now, what needs a fix tomorrow, and which vulnerabilities you don’t need to address at all, and why. The technologies can scan both source code and the OSS ecosystem to provide a holistic risk score encompassing quality, activity, popularity, and security.
They can also develop detailed dependency graphs without requiring any agents or proxies in runtime. This makes implementation much easier, and allows organizations to quickly understand how developers are using these dependencies; which are being called from their code; which are unused; and more. This means that the next time an organization faces a log4j-like incident, it can find the problem in minutes rather than weeks."
Reducing developer fatigue and improving productivity
"As we enter a new stage in the maturity of OSS consumption, organizations need to find ways to maintain the speed and productivity OSS enables, without compromising security. The first steps are to examine the process of selecting OSS dependencies, and understanding how to select more sustainable ones that will reduce long-term risk," said Henrik Plate, CISSP security researcher at Endor Labs about reducing developer fatigue and improving productivity.
"Developers waste over 50% of their time dealing with noisy application security alerts. Code and pipeline governance technologies let them prioritize only the risks that truly affect their environment, reducing false positives by 80% compared to software composition analysis tools," added Varun Badhwar.

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here










