threat detection
threat detection news search results
Developer news items we found relating to threat detection
31 results
Universities fighting cybercrime with students
Thursday, April 24, 2025 by Richard Harris
Universities, one of the most popular targets for cybercriminals, are employing a new tool in the fight against cybercrime, their own students. Over the past few years, universities and colleges around the U.S. have been increasingly hiring students and training them to become analysts in their security operations centers, known as SOCs. Students work alongside...

API Security Perspectives 2025 report from Kong Inc
Monday, December 30, 2024 by Richard Harris
Kong Inc. released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report which highlights today’s API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern a...

Faster cyberthreat detection updates from Progress
Tuesday, October 29, 2024 by Austin Harris
Progress announced the latest release of Progress Flowmon, the network observability platform with AI-powered detection for cyberthreats, anomalies and fast access to actionable insights for greater network and application performance across hybrid cloud ecosystems. With today’s release, the Flowmon platform enhances IP search efficiency up to tenfold with in...

Off-the-shelf intelligent automation beats custom ECM monitoring
Monday, October 14, 2024 by Austin Harris
The accumulation of digital information is overwhelming, and the reliance on increasing access must be recognized. The danger in this climate is that storage capacity can be quickly consumed if structured and unstructured data are not adequately managed. More storage can lead to more costs and complexity - especially regarding compliance mandates. On top of that, more t...

GenAI cybersecurity assistant lands from IBM
Friday, August 16, 2024 by Freeman Lightner
IBM recently announced the introduction of generative AI capabilities to its managed Threat Detection and Response Services utilized by IBM Consulting analysts to advance and streamline security operations for clients. Built on IBM's watsonx data and AI platform, the new IBM Consulting Cybersecurity Assistant is designed to accelerate and improve the identification,...

AWS introduces Mithra advanced threat intelligence neural network
Thursday, August 15, 2024 by Freeman Lightner
In a recent blog post from AWS, Amazon Chief Information Security Officer CJ Moses detailed the robust threat intelligence capabilities that safeguard AWS customers. Through tools like Mithra and MadPot, AWS collects and analyzes vast data, identifying and neutralizing threats with unparalleled accuracy and speed. AWS's proactive approach to sharing high-fidelity th...

Secure software development insights from The Linux Foundation
Monday, February 5, 2024 by Richard Harris
The Linux Foundation published a new report, Maintainer Perspectives on Open Source Software Security, based on a survey of OSS maintainers and core contributors, to understand perspectives on OSS security and the uptake and adoption of security best practices by maintainers, core contributors, end users, and other members of the OSS ecosystem. Maintainer Perspective...

Cybersecurity performance optimization updates from Logpoint
Friday, February 2, 2024 by Freeman Lightner
Logpoint is releasing new capabilities to its Converged SIEM platform, enhancing threat detection and security operations and streamlining case management. Organizations can focus on essential security matters with the new capabilities by reducing workload, simplifying automation, and freeing up resources. The new release delivers increased system stability and ...

Standards based operator cloud demonstration at Network X
Friday, October 27, 2023 by Freeman Lightner
The CloudCO demonstration to be led by the Broadband Forum at this year’s Network X will show how network operators can unlock network efficiencies and new service delivery from a disaggregated and virtualized software-defined broadband network. CloudCO’s service delivery automation focus is fundamental for operators to help reduce their operational costs...

Network-based cybersecurity threat detection SDK launches
Monday, October 16, 2023 by Freeman Lightner
Enea has launched the Enea Qosmos Threat Detection SDK. This revolutionary threat detection system has the potential to double performance in network-based cybersecurity solutions. The Qosmos Threat Detection SDK enables the integration of Enea's flagship deep packet inspection (DPI) engine, Qosmos ixEngine, with core IDS capabilities drawn from Suricata, the wid...
Q CTRL names Dave Kielpinski as Principal Quantum Control Scientist
Tuesday, May 16, 2023 by Brittany Hainzinger
Q-CTRL recently announced the addition of industry trailblazer Dave Kielpinski as Principal Quantum Control Scientist. Kielpinski has spent the last 25 years contributing to and leading research projects in uncharted territories of science. In 2002, he authored a foundational paper for quantum computing, which laid out the framework for the architecture of large-scale i...
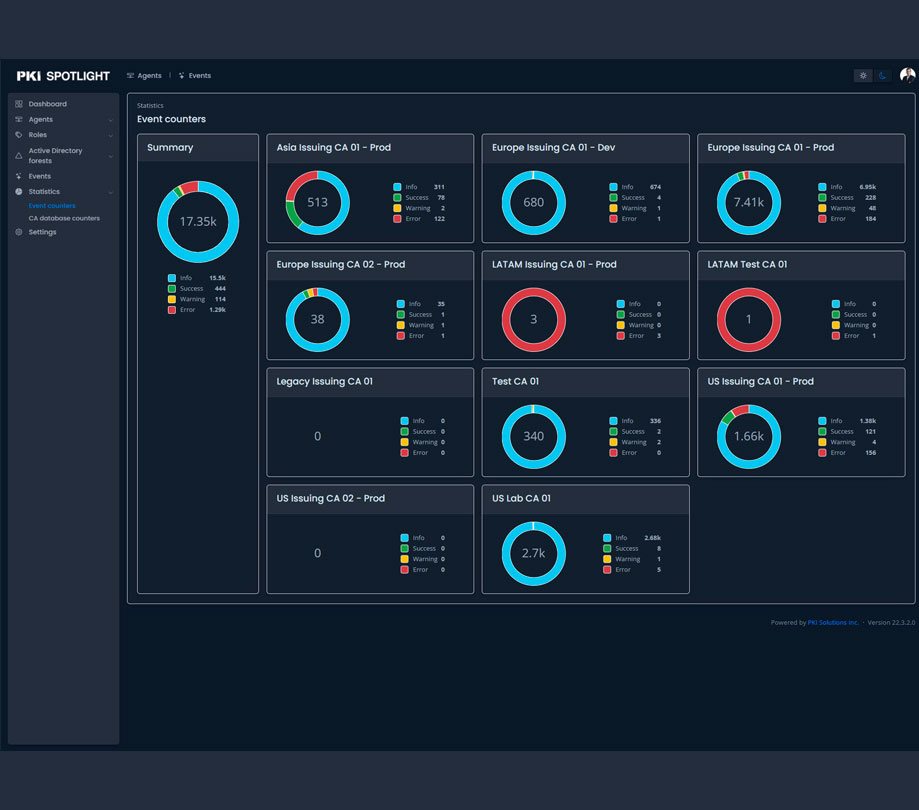
PKI Spotlight security solution launches
Wednesday, April 6, 2022 by Freeman Lightner
PKI Solutions announced the introduction of PKI Spotlight, an industry solution that provides real-time monitoring and alerting of the availability, configuration, and security of all organizations' PKI environments, all consolidated into one easy-to-use dashboard. PKI is a foundational technology for almost every identity and data encryption solution...
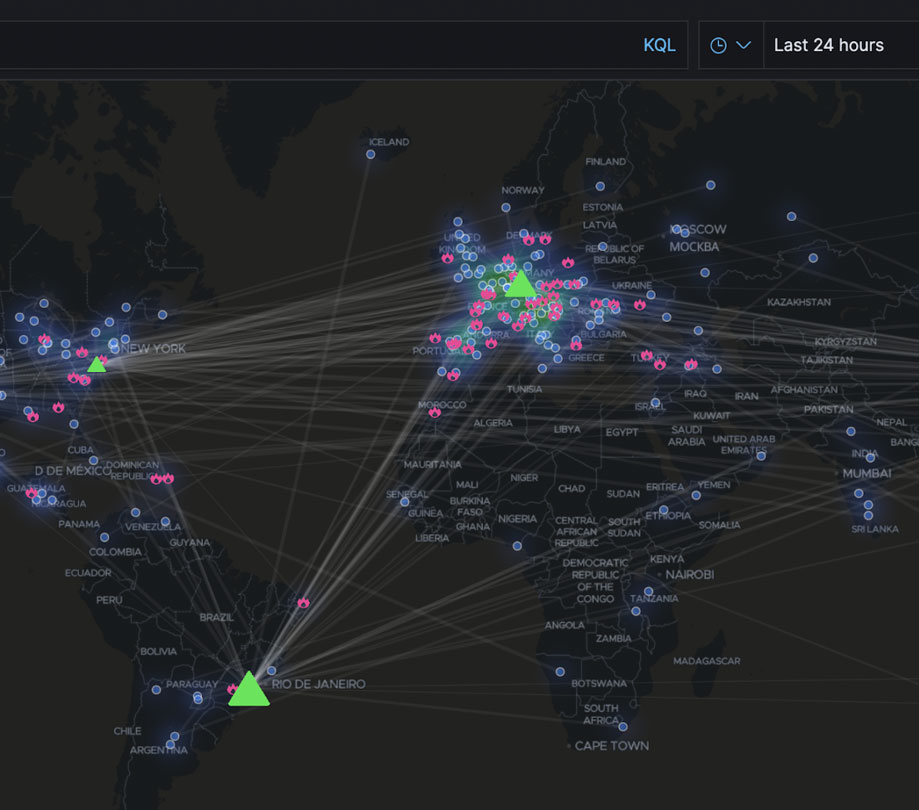
Elastic Stack 7.3 brings maps and more
Monday, August 5, 2019 by Austin Harris
Elastic has delivered Elastic Stack 7.3, which includes some very cool new features such as data frames, anomaly detection, elastic maps, and more. Check out all the highlights of the latest release below. Elastic Stack 7.3 highlights Data frames: a new feature that allows users to pivot their Elasticsearch data on the fly to create live entity-centric in...

Anomaly detection by Instaclustr processes 19 billion events per day
Wednesday, June 19, 2019 by Brittany Hainzinger
Instaclustr announced it has successfully created an anomaly detection application capable of processing and vetting real-time events at a uniquely massive scale – 19 billion events per day – by leveraging open source Apache Cassandra and Apache Kafka and Kubernetes container orchestration. Get the source code on github. Anomaly detection is the identific...

First multiTEE security platform for mobile app developers emerges
Tuesday, March 5, 2019 by Austin Harris
Trustonic says it will expand support to include Huawei’s Trusted Execution Environment (TEE) on its mobile application security platform, Trustonic Application Protection (TAP). Until now, TAP has enabled app developers to build apps secured by both strong application shielding for iOS and Android, and hardware-based protection for the 1.7 billion Android devices...

Mesh networking security from NeuVector at IBM Think 2019
Thursday, February 14, 2019 by Richard Harris
NeuVector announced a new platform integration with the Istio and Linkerd2 service meshes that expands NeuVector’s security capabilities for production Kubernetes deployments. The integration - developed in coordination with IBM Cloud and the Istio open source development team - delivers new capabilities for network visibility and threat detection, even for connec...
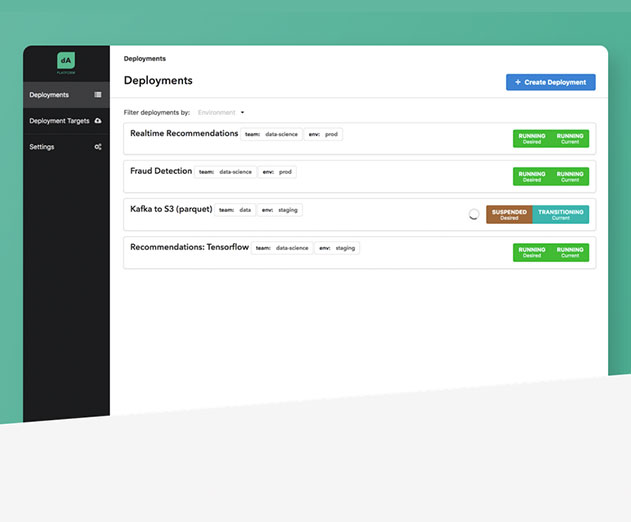
Stateful data stream processing launches to GA
Monday, April 2, 2018 by Austin Harris
data Artisans announced the general availability of dA Platform - a stream processing platform that enables enterprises to get insights from data in milliseconds and power next-generation service-centric applications and business models. The new release productionizes stream processing and enables companies to provide live data applications as a centralized enterprise s...

Shared data machine learning PaaS kicks off from Cloudera
Tuesday, March 13, 2018 by Richard Harris
Cloudera, Inc. announced Cloudera Altus with SDX, a machine learning and analytics Platform-as-a-Service (PaaS), built with a shared data catalog providing the business context of that data. Altus supports a variety of high-value business use cases that require applying multiple data analysis capabilities and approaches together. SDX makes it possible for those analytic...

SlashNext launches AI internet threat protection system
Thursday, November 9, 2017 by Austin Harris
SlashNext announced the company’s broad market release of the SlashNext Internet Access Protection System to protect organizations from cross platform social engineering and phishing, malware, exploits and callback attacks. The system goes beyond first generation signature-based and second generation sandbox-based technologies and deploys artificial intelligence and cog...
Automated Security as a Service platform by ShiftLeft launches
Monday, October 16, 2017 by Austin Harris
ShiftLeft Inc. has introduced an automated Security as a service (SECaaS) for cloud software that creates custom security and threat detection for each application it supports. With ShiftLeft, organizations can now secure their cloud applications as part of their continuous integration pipeline, rather than merely reacting to threats discovered in production. ShiftLeft ...

Tips for securing container deployments
Friday, September 1, 2017 by Richard Harris
Container deployments are still susceptible to the regular threats that other types of deployments are - including DDoS and cross-site scripting attacks. In fact, hackers often take advantage of compromised containers to scan sensitive data, download malware, or privilegeunauthorized access to any of your containers, hosts or data centers.Fei Huang is the CEO of NeuVect...

Security Intelligence Platform from Exabeam launched
Thursday, February 2, 2017 by Richard Harris
Exabeam has announced its new Security Intelligence Platform, designed to decrease the risk of cyber threats for organizations of any size.Recent data breaches continue to demonstrate that security management is broken; attacks using stolen or misused passwords keep rising, and companies cannot detect or respond to them effectively. Breaches now have national and intern...

NeuVector has a new approach to securing Docker containers
Wednesday, February 1, 2017 by Richard Harris
NeuVector has announced the launch and availability of a new approach to securing Docker containers. With constant behavioral learning automatically applied to security policies for containers, the platform secures containers where they have been most vulnerable: in production environments where they are constantly being deployed, updated, moved, and scaled across hosts...

Veris Group steps up it's advanced security game with Endgame
Friday, December 16, 2016 by Austin Harris
Endgame has announced that Veris Group's Adaptive Threat Division (ATD), a provider in adversary simulation and detection services, will utilize Endgame's endpoint detection and response platform to enhance detection, response, and threat hunting capabilities to eliminate security threats faster and with greater accuracy for customers.This partnership leverages Endgame'...

Intel Security Enhances Unified Defense Architecture
Thursday, November 3, 2016 by Richard Harris
Intel Security has announced an enhanced unified defense architecture designed to empower organizations to more effectively protect a new digital economy of trust, time and money. No longer is our economy a physical one, but one of connected networks and systems where cybercriminals have put us on the defensive. This new second economy, has put us in a world where ...
Splunk Harnesses Machine Learning for New Innovations
Tuesday, September 27, 2016 by Richard Harris
Splunk Inc. has released new versions of Splunk Enterprise, Splunk IT Service Intelligence (ITSI), Splunk Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Available on-premises or in the cloud, the newest versions of Splunk solutions leverage machine learning to make it faster and easier to maximize the value machine data can deliver to organizations.A...

AdaptiveMobile Adds SS7 Cat 3 Detection Capabilities to Mobile Threat Intelligence Platform
Wednesday, June 29, 2016 by Richard Harris
AdaptiveMobile has announced advanced SS7 “Cat 3” Signalling Protection detection capabilities to its Mobile Threat Intelligence Platform including Network Memory, Location Plausibility, and Remote Intercept. The Company’s advanced threat detection is based on continuous data and analysis with all rules validated with information from across five continents. Adapt...

Twistlock Releases New Security Platform for Container Environments
Thursday, May 12, 2016 by Richard Harris
Twistlock has announced the release of Twistlock Runtime, a set of automated capabilities that defend against active threats targeting container environments. The platform is designed specifically to detect and stop sophisticated runtime attacks – including APTs and zero-day exploits – against containerized applications. Twistlock Runtime is a component within the ...
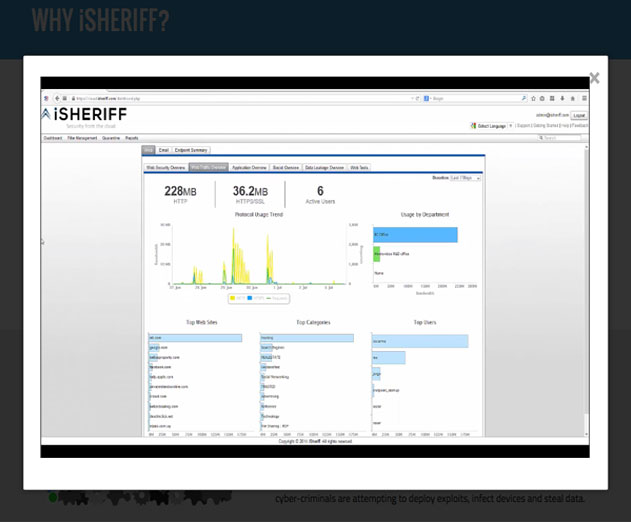
New iSheriff Complete Platform Offers a Cloud Based Cyber Security Platform
Tuesday, February 2, 2016 by Stuart Parkerson
Cloud security provider iSheriff has released iSheriff Complete, a cyber security platform designed to provide 360-degree protection of an organization’s devices and communication channels. iSheriff Complete is a cloud based platform that provides fully-integrated endpoint, Web and email security, delivered through a single Web-based management console with a single set...
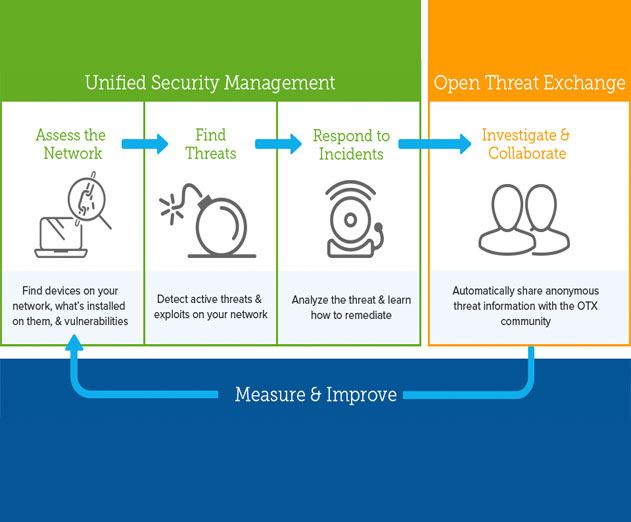
AlienVault Releases Native Solution for AWS Cloud Security and Threat Intelligence
Saturday, April 11, 2015 by Richard Harris
AlienVault has announced the general availability of AlienVault Unified Security Management (USM) for Amazon Web Services (AWS). AlienVault USM for AWS is an AWS-native solution that delivers built-in security controls and threat intelligence for IT and security teams to accelerate and simplify threat detection and incident response. USM for AWS is available on AWS Mark...

Perforce Software Launches New Helix SCM and Content Collaboration Platform
Thursday, March 12, 2015 by Richard Harris
Perforce Software has released Perforce Helix, a new supply chain management (SCM) and content collaboration platform that brings distributed workflows, Git management, advanced threat detection and new deployment options for applications, Internet of Things devices and digital media. The Helix collaboration platform serves as a single source for all the contributo...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|