security intelligence
security intelligence news search results
Developer news items we found relating to security intelligence
23 results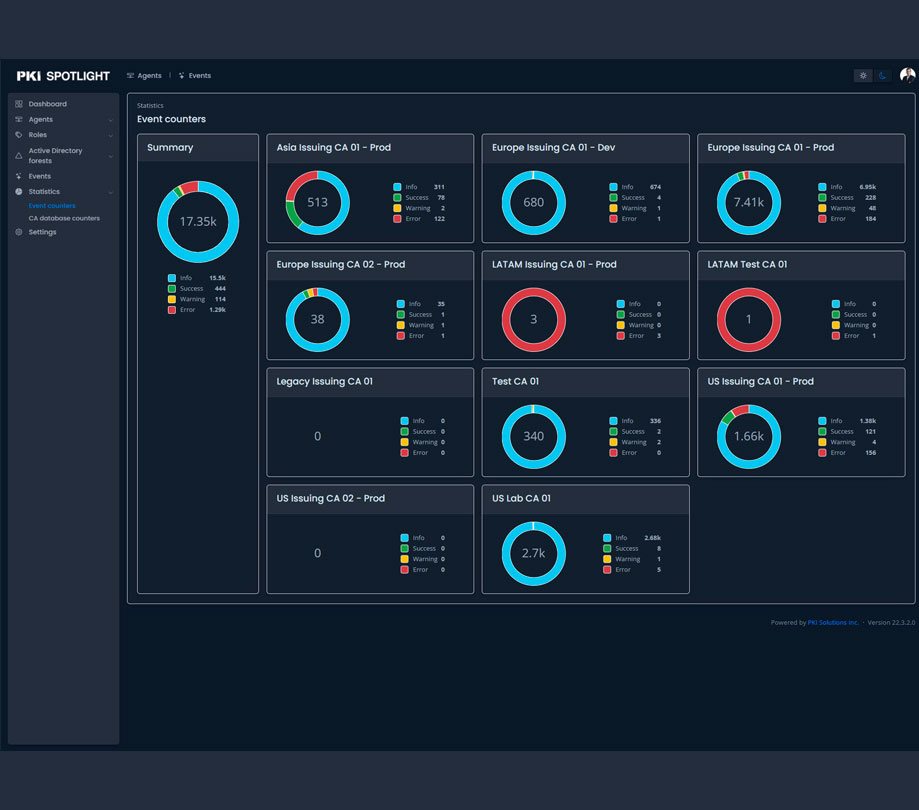
PKI Spotlight security solution launches
Wednesday, April 6, 2022 by Freeman Lightner
PKI Solutions announced the introduction of PKI Spotlight, an industry solution that provides real-time monitoring and alerting of the availability, configuration, and security of all organizations' PKI environments, all consolidated into one easy-to-use dashboard. PKI is a foundational technology for almost every identity and data encryption solution...
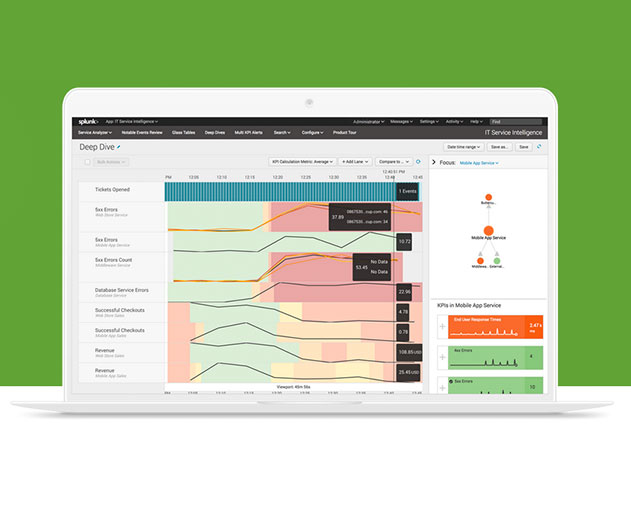
Splunk expands machine learning capabilities
Monday, October 2, 2017 by Richard Harris
Splunk Inc. has announced expanded machine learning capabilities across its product portfolio with the release of their Enterprise 7.0, IT Service Intelligence (ITSI) 3.0, User Behavior Analytics (UBA) 4.0 and updates to their Cloud platform. Splunk also introduced an updated suite of solutions that apply analytics and machine learning to fraud and cloud monitoring use ...

Dataguise released DgSecure for Google Cloud Storage
Tuesday, March 14, 2017 by Richard Harris
Dataguise has said that DgSecure Detect now supports sensitive data discovery on Google Cloud Storage (GCS). Integration with GCS extends the range of platforms supported by DgSecure and helps data-driven enterprises move to the cloud with confidence by providing precise sensitive data discovery across the enterprise and in the cloud. With their platform, organizations ...

App customer loyalty: 3 things to look for in a loyalty API
Tuesday, February 14, 2017 by Christopher Barnard
For the modern consumer, rewards are an essential part of their shopping experience; just last year the number of loyalty program memberships in the United States topped three billion - a 26 percent increase from 2013. With a growing demand for loyalty programs, there is no better time for developers to incorporate loyalty into their products, apps, point of sale softwa...

IBM Watson for cyber security has cognitive skills
Monday, February 13, 2017 by Richard Harris
According to IBM research, security teams sift through more than 200,000 security events per day on average, leading to over 20,000 hours per year wasted chasing false positives. The need to introduce cognitive technologies into security operations centers will be critical to keep up with the anticipated doubling of security incidents over the next five years and increa...

Introducing a web security ACL to block based on device fingerprints
Friday, February 3, 2017 by Richard Harris
Distil Networks, Inc., a bot detection and mitigation company, has announced a web application security Access Control List (ACL) platformA to block based on device fingerprints, providing a more effective way for website defenders to manage and apply whitelists and blacklists across their online applications."A key piece of feedback we got from our Bot Defense Council ...

New release of Aqua security platform includes secrets management
Friday, February 3, 2017 by Austin Harris
Aqua Security, a platform provider for securing containerized applications, has announced the release of version 2.0 of its Container Security Platform (CSP). A major requirement for securing containerized applications is ensuring that containers can only communicate within their permitted network segment, limiting the “blast radius” in case of an attack. The challenge ...

Optimizing your app server performance really matters
Friday, February 3, 2017 by Richard Harris
As people are becoming more and more likely to turn to software as a means for entertainment, computer utility solutions, and everything in between, the load on a healthy business's servers can quickly max out. This can cause some major issues, i.e. leaving your customers suffering from horrible load times or even completely dead in the water. That's why a intuitiv...

Security Intelligence Platform from Exabeam launched
Thursday, February 2, 2017 by Richard Harris
Exabeam has announced its new Security Intelligence Platform, designed to decrease the risk of cyber threats for organizations of any size.Recent data breaches continue to demonstrate that security management is broken; attacks using stolen or misused passwords keep rising, and companies cannot detect or respond to them effectively. Breaches now have national and intern...

Checkmarx opens beta support for Scala programming language
Wednesday, February 1, 2017 by Richard Harris
Checkmarx, an application security testing company, has announced open beta support of the Scala programming language. The new capability adds the ability to analyze and remediate security risks and vulnerabilities exposed in projects written using Scala code.The added capability not only allows the detection of vulnerabilities within Scala code, but also the ability to...

The data security money pit
Wednesday, January 25, 2017 by Richard Harris
93% of organizations suffer technical challenges to protect data despite heavy investment in security tools.While data breaches destroy customer confidence, impact revenues, attract large regulatory fines and cost C-levels their jobs, 76% of data security professionals believe in the maturity of their data security strategy, according to a new study. Despite heavy inves...

Ransomware facts and the steps to prevent it on your device
Friday, December 30, 2016 by Richard Harris
As technology advances forward, so does its unintended consequences and evolution of bad people being able to exploit its weaknesses. Reports of one these exploits is sweeping across Europe, its name is ransomware. Ransomware is malware that allows hackers to take control of your computer and all its data, and then hold it hostage via encryption until a certain sum of m...

8 cyber security predictions for what's to come in AsiaPacific
Thursday, December 29, 2016 by Austin Harris
Cyber security received heightened interest in 2016 due to a spate of cyber attacks in the region. These included cyber attacks on the database of 55 million voters at the Philippines Commission on Elections (COMELEC), the National Payment Corporation of India (NPCI), US$81 million cyber heist at the Bangladesh Central Bank and the massive data leaks as shown by the Yah...

How to secure your online accounts from cyber attacks in 2017
Wednesday, December 21, 2016 by Richard Harris
In addition to ball drops and bubbly, the New Year offers an occasion to reflect and contemplate what's ahead in 2017. When Dec. 31 rolls around, many of us think about getting fit, saving more money and promising to take time to enjoy life. As the world becomes more and more connected – and our digital and offline lives become indistinguishable – we should also commit ...
Why you should ditch traditional business software analysis
Tuesday, December 20, 2016 by Richard Harris
Competition between software companies is a fierce battle waged not with weapons, but with scalable, intuitive, and efficient solutions that can most effect their customer’s lives. The importance of a well coordinated and strategic approach to how you choose to execute your solution is perhaps one of the most fundamental necessities required to succeed in markets.That’s...

Cyberbit's SOC 3D automation updates and what you should know
Tuesday, December 20, 2016 by Richard Harris
Cyberbit just announced a new version of its SOC 3D automation and orchestration platform that increases productivity and effectiveness of the SOC and substantially reduces incident response times. The new platform integrates with all major SIEM and security solutions, automates SOC runbooks and workflows, and prioritizes incidents according to their business impact. It...

Automatically generate network security intelligence with new tool
Monday, December 19, 2016 by Richard Harris
Logtrust, a real-time big data-in-motion firm for big data analytics, and Panda Security, a cloud-based security solution, announced the availability of the Advanced Reporting Tool (ART), which automatically generates security intelligence that allows organizations to pinpoint attacks and unusual behaviors, and detect internal misuse of systems and networks. ART's uniqu...
What's so tricky about Android security anyway
Monday, December 12, 2016 by Don Duncan
Android authentication can be a tricky business because it can help identify the user, but it can also open the door to hackers at the same time. It all comes down to the device administrator access which comes with a lot of benefits like. Device administrator access provides complete device management access rights that include creating and managing poli...

Intel Security Enhances Unified Defense Architecture
Thursday, November 3, 2016 by Richard Harris
Intel Security has announced an enhanced unified defense architecture designed to empower organizations to more effectively protect a new digital economy of trust, time and money. No longer is our economy a physical one, but one of connected networks and systems where cybercriminals have put us on the defensive. This new second economy, has put us in a world where ...

IBM Security Channels Its Inner XMen with Launch of IBM XForce Red Security Division
Friday, August 5, 2016 by Stuart Parkerson
Someone in charge of naming divisions at IBM must have been a big Sci-Fi fan as is evidenced with IBM Security’s name for the a news security task force - IBM X-Force Red. Yep, that’s the name for a new group of IBM security professionals and ethical hackers whose goal is to help businesses discover vulnerabilities in their computer networks, hardware, and software...
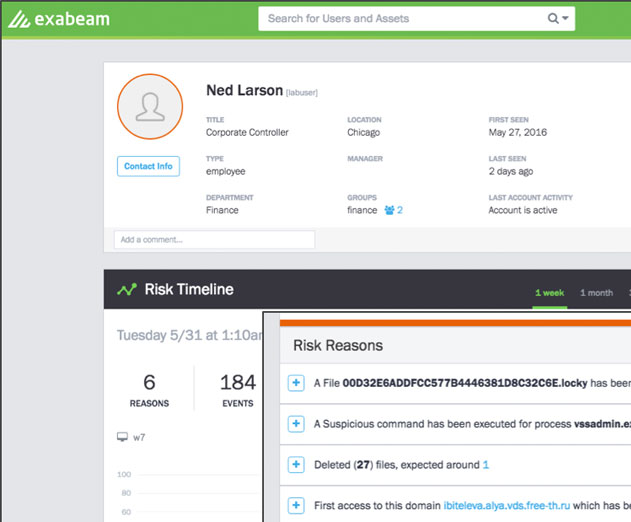
Exabeam Releases Security Intelligence Platform for Early Detection of Ransomware
Thursday, June 16, 2016 by Richard Harris
Exabeam has released Exabeam Analytics for Ransomware, a new behavior-based security intelligence platform designed for early detection of ransomware across a corporate network. Exabeam can detect ransomware movement and activity in the network, the servers, workstations, BYOD devices, and cloud services.Exabeam detects ransomware as it first enters the network and begi...

Metalogix ControlPoint 7.0 Offers Security Monitoring for Suspicious SharePoint Activity
Thursday, November 5, 2015 by Stuart Parkerson
Metalogix has released ControlPoint 7.0, offering new, embedded security intelligence, and real-time situational awareness into suspicious SharePoint user activity to help prevent data breaches and leakages. With the combination of Metalogix Sensitive Content Manager and ControlPoint 7.0, the platform offers unified management to optimize the availability, performance, ...
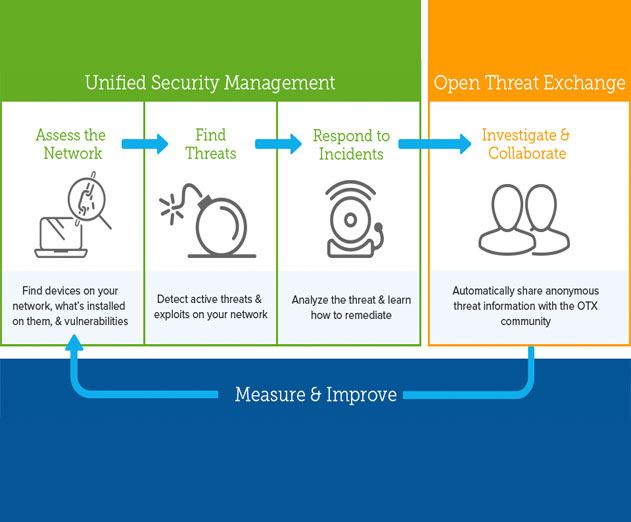
AlienVault Releases Native Solution for AWS Cloud Security and Threat Intelligence
Saturday, April 11, 2015 by Richard Harris
AlienVault has announced the general availability of AlienVault Unified Security Management (USM) for Amazon Web Services (AWS). AlienVault USM for AWS is an AWS-native solution that delivers built-in security controls and threat intelligence for IT and security teams to accelerate and simplify threat detection and incident response. USM for AWS is available on AWS Mark...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp