security analytics
security analytics news search results
Developer news items we found relating to security analytics
18 results
ezeep JavaScript library lands from ThinPrint
Tuesday, March 29, 2022 by Richard Harris
ezeep by ThinPrint announced the release of ezeep.js, a new JavaScript library that makes it possible for web developers to easily add printing capabilities into any web application in just a few steps. "Desktop applications are being replaced by cloud-based web applications, and users are accessing them from all kinds of devices, smartphones...

SRE hiring trends
Thursday, January 6, 2022 by Richard Harris
Ashley Stirrup, COO at Shoreline.io shares his 2022 predictions about the death of the Runbook, the rising cost of outages and SRE hiring trends. Prediction #1: The death of the Runbook In the coming year, we will see runbooks fuse out. Our team has been surprised in the last few months with how infrequently people have had true Runbooks. Runbooks are a great plac...

Security analytics platform selects Pulumi Cloud
Monday, January 3, 2022 by Freeman Lightner
Pulumi announced Panther Labs, a security analytics platform company that helps teams detect and respond to breaches at cloud scale, has selected the Pulumi Cloud Engineering Platform to manage and scale its cloud infrastructure. With Pulumi, Panther has been able to speed its deployments by up to 10X, reduce the size of its legacy infrastructure codebase by more than 5...

DevSecOps showcase by Sumo Logic unravels all their new changes
Monday, September 17, 2018 by Richard Harris
Sumo Logic announced a number of new solutions and enhancements to its platform to empower enterprises to "win in the analytics economy." These innovations, as well as those from DevSecOps ecosystem partners, will be showcased this week at Sumo Logic’s user conference, Illuminate, in Burlingame, Calif. Illuminate will gather over 600 experts in machine d...

National Coding Week is here
Monday, September 17, 2018 by Richard Harris
National Coding Week is upon us. That's why we thought it would be great to compile some quotes from industry experts to talk about what they think is most important about learning how to coding - a question seen through many different lenses. “Today, software drives business. So, if an organization wants to excel, it needs to become a software-powered jugg...

DevSecOps is important and here is why
Friday, October 20, 2017 by Richard Harris
In the digital age, securing your development projects against malicious hackers can be quite the challenge. And when you take security and try to scale security to an enterprise, the challenge seems insurmountable. Evident by the frequent hacking incidents we see come through the news.Enter DevSecOps. DevSecOps is a methodology that interweaves the aspects of DevOps an...

Biometric authentication for your apps from Appdome and BehavioSec
Wednesday, April 26, 2017 by Richard Harris
Appdome, a cloud service that automates mobile integration by fusing new services to mobile apps, is partnering up with biometric authentication technology company, BehavioSec. Appdome for BehavioSec now enables mobile developers and mobility professionals (such as mobile fraud, IT, or Security groups) to rapidly integrate advanced biometric and behavior based authentic...

Capsule8 comes out of stealth to help protect Linux from attacks
Wednesday, February 15, 2017 by Austin Harris
Capsule8 has emerged from stealth mode to unveil its plans for the industry’s first container-aware, real-time threat protection platform designed to protect legacy and next-generation Linux infrastructures from both known and unknown attacks. Founded by experienced hackers John Viega, Dino Dai Zovi and Brandon Edwards, Capsule8 is being built on the real-world experien...

Automatically generate network security intelligence with new tool
Monday, December 19, 2016 by Richard Harris
Logtrust, a real-time big data-in-motion firm for big data analytics, and Panda Security, a cloud-based security solution, announced the availability of the Advanced Reporting Tool (ART), which automatically generates security intelligence that allows organizations to pinpoint attacks and unusual behaviors, and detect internal misuse of systems and networks. ART's uniqu...

How do we simplify eastwest security The imperative path is upon us
Monday, December 5, 2016 by Keshav Kamble
Ahhh, the endless saga of streamlining hazards around application security: let’s talk about the East-West component of the conundrum. But first, it’s important to clarify the variances of ‘East-West’ vs. ‘North-South’ traffic in a typical data center environment. By definition: North-South traffic is the communication that occurs between server applications deploy...
Splunk Harnesses Machine Learning for New Innovations
Tuesday, September 27, 2016 by Richard Harris
Splunk Inc. has released new versions of Splunk Enterprise, Splunk IT Service Intelligence (ITSI), Splunk Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Available on-premises or in the cloud, the newest versions of Splunk solutions leverage machine learning to make it faster and easier to maximize the value machine data can deliver to organizations.A...

Rackspace Grants Early Access to Its Managed Security for Azure
Sunday, August 14, 2016 by Stuart Parkerson
Rackspace has announced early access to its Rackspace Managed Security for Microsoft Azure allowing those using Microsoft Azure, Amazon Web Services (AWS), Rackspace Dedicated Hosting and Rackspace Managed VMware Cloud to receive additional security protections provided by Rackspace Managed Security to detect and respond to security threats across cloud platforms.The pl...
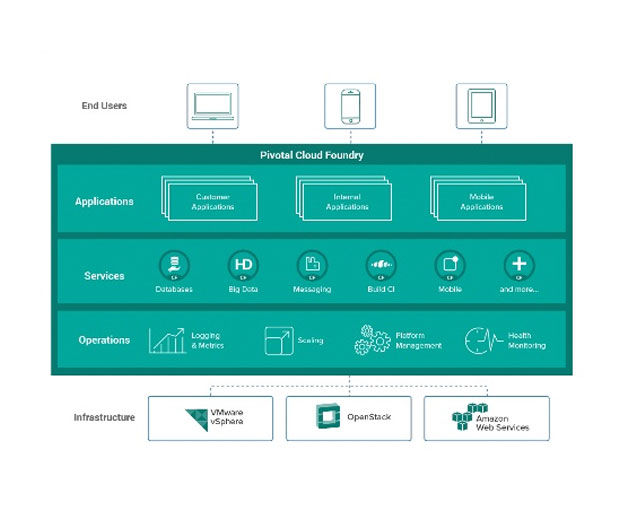
Apigee's API Management Platform Now Available on Pivotal's Cloud Foundry
Friday, May 20, 2016 by Stuart Parkerson
Apigee and Pivotal have announced the availability of Apigee’s API management software for Pivotal's Cloud Foundry. Pivotal users can now select Apigee Edge software from the Pivotal Network marketplace to get Apigee’s API management capabilities integrated into their web applications built with Pivotal Cloud Foundry.The Apigee-Pivotal Cloud Foundry integration provides...

New Report Highlights Wide Ranging Cybersecurity Challenges
Wednesday, September 2, 2015 by Richard Harris
Cybersecurity Ventures has released its Cybersecurity Market Report for Q3 2015 which provides an overview of software development and application security trends, statistics, best practices, and resources. Highlights of the report include:- “The SANS Institute 2015 State of Application Security Report” states that many information security engineers don’t understa...
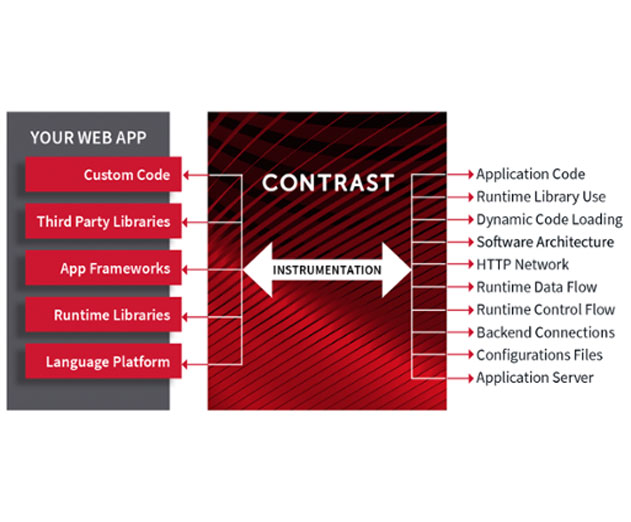
Contrast Security Release New Enterprise Application Security Platform
Tuesday, June 9, 2015 by Stuart Parkerson
Contrast Security has release Contrast Enterprise, a new application security product to integrate defenses across development and operations, offering vulnerability assessment, security visibility and attack protection throughout the application lifecycle. Contrast Enterprise offers Runtime Application Self-Protection (RASP), which provides deep security instrumen...

IBM to Offer iOS Enterprise Solutions Plus They Will Sell Enterprise Enabled iPhones and iPads
Wednesday, July 16, 2014 by Richard Harris
My, my how the world has changed. Remember the 80’s when IBM led the PC charge and Apple’s Mac was the little engine that could. General sentiment was that PC’s were for serious work and Macs for the more artistically slanted.Not anymore as the iPhone and iPad reign supreme and PC sales continue to plunge like a flaming meteor. And now IBM and Apple are teaming up in a ...

Should Mobile App Developers Create Analytics to Track the NSA
Monday, March 3, 2014 by Adam Grant
Before you read on, do not think that this article is political in nature or advocates anything remotely approaching what the title suggests. Contrary to the “hook” contained in the title, the purpose of the article is to educate Mobile App Developers on what is reportedly done to the information obtained by the apps they develop. During this past year, the news ...

ESG Defines the Market for Big Data Security Analytics
Friday, May 31, 2013 by Richard Harris
Leading analyst firm publishes report on information security analytics toolsMilford, Mass - May 21, 2013 - A new report examining the supply side of big data security analytics has been published by Enterprise Strategy Group (ESG), a leading IT research, analysis, and strategy firm. The report defines the market for big data security analytics and gauges existing solut...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|