secure app
secure app news search results
Developer news items we found relating to secure app
35 results
Why your ChatGPT app will need a no-code rescue
Wednesday, December 18, 2024 by Josh Haas
Josh Haas explains how generative AI falls short in app development, leaving founders to face challenges like iteration, security, and usability. He highlights how pairing AI with no-code platforms enables faster, scalable, and secure app creation. Why your ChatGPT app will need a no-code rescue Every day, we see YouTube videos of people using AI to turn plain English...

Detect hard coded secrets with new capabilities from Cycode
Thursday, August 10, 2023 by Freeman Lightner
Cycode announced the expansion of its hard-coded secrets detection in cloud-based workplaces, as well as a collaboration with Azure DevOps pipelines to ensure end-to-end supply chain integrity and a new IDE plug-in for seamless integration with VS Code. Building upon its existing code-to-cloud coverage, Cycode now extends its secrets scanning capabilities to encompas...

CI and CD Can Make the Difference for Your Business
Thursday, November 19, 2020 by Freeman Lightner
Corporate leaders expect development teams to produce innovative, high-quality, highly secure, agile applications that are instantly available on multiple platforms with a seamless user experience. In this software-centric era, DevOps, continuous integration (CI) and continuous delivery (CD) — three milestones on the path to organizational improvement — h...

Docker and Snyk partner to deliver container vulnerability scanning
Wednesday, May 20, 2020 by Brittany Hainzinger
Docker has partnered with Snyk to deliver native vulnerability scanning of container images in Docker. Together, Docker and Snyk will provide a streamlined workflow that makes the application development process more secure for millions of developers, allowing them to more quickly and confidently build secure applications as an automated part of their toolchain. ...

Zero Trust platform from Pulse Secure is enhanced
Tuesday, October 29, 2019 by Richard Harris
Pulse Secure announced that it has introduced new Secure Access management and threat mitigation capabilities within its Zero Trust Network Access platform. Through these enhancements, Pulse Secure enables enterprise and service provider organizations to progress Zero Trust security and mitigate hybrid IT risks while simplifying access to multi-cloud and data center res...
Perforce to acquire Rogue Wave
Monday, January 28, 2019 by Austin Harris
Perforce Software backed by Clearlake Capital Group, L.P., announced it has reached a definitive agreement to acquire Rogue Wave Software, an independent provider of cross-platform software developer tools and embedded components. The combination of Perforce and Rogue Wave delivers a full suite of solutions that measurably improves developer productivity while fuelin...

Kubernetes as a Service lands from DigitalOcean
Monday, December 17, 2018 by Richard Harris
DigitalOcean announced that its managed Kubernetes service is now available with production-ready functionality and full customer support. Since launching its early access release in May of this year, 30,000 developers and teams have already signed up for access. Starting today, the service is available to all developers worldwide. With the May early access release, ...

5 app development tips to help you avoid disaster
Wednesday, November 28, 2018 by Joe Hanson
Mobile app development: it’s easy and straightforward in the lab, but once your app is deployed to the wild, all bets are off. You need to deliver seamless, fast experiences for users on low-powered devices, in any number of network environments. When it comes to building mobile apps, uncontrollable user behavior can lead you down the path to death by 1000 pape...

The differences between web apps and native apps
Thursday, October 18, 2018 by Richard Harris
Even in 2018, years past the origional question, the debate rages on across the land, in office spaces and conference rooms every day - should we build a full-blown native mobile app, or is distributing over the web good enough? By now everyone knows the “mobile-first” mentality because statistics like 50% of web searches being done from a mobile dev...

Code security gamification company nabs $3.5M in funding
Friday, September 14, 2018 by Austin Harris
Secure application development platform provider Secure Code Warrior announced that it has gained US $3.5 million in funding from two strategic venture capital firms. The financing was led by Washington DC-based Paladin Capital Group, with participation from Sydney-based AirTree Ventures. The initial funding round will allow the company to further expand its rapidly gro...

VMworld 2018 developer highlights
Wednesday, August 29, 2018 by Austin Harris
VMworld 2018 has launched from the dock, debuting a ton of new cloud technology that ranges from multi-cloud operations to relational database services. To celebrate the company’s 20th year anniversary, Pat Gelsinger, VMware CEO, and Ray O’Farrell, VMware CTO acquaint the audience with what superpowers it takes to make it in the world of technology. The d...

Multicloud app network platform update launched by MuleSoft
Tuesday, May 15, 2018 by Austin Harris
Making a multi-cloud app just got a little easier thanks to MuleSoft's latest release of their Anypoint Platform. It features new capabilities that aim to give developers the ability to easily deploy, secure and monitor composite applications across cloud environments. Anypoint Platform unlocks the power of API-led connectivity, allowing organizations to connect apps, d...

Why developers run away from security updates
Monday, April 16, 2018 by Richard Harris
Veracode, Inc. has released new data that shines a light on the discrepancy between component security and hygiene. According to the research conducted with Vanson Bourne, only 52 percent of developers using commercial or open source components in their applications update those components when a new security vulnerability is announced. This highlights organizations’ la...

Pulse Secure expands to support hybrid IT with secure access
Monday, April 16, 2018 by Richard Harris
Pulse Secure has announced new cloud and virtual appliances to protect access and support applications in hybrid IT environments. Enterprises are quickly moving to deploy hybrid IT, leveraging the cloud to introduce new user services and gain disaster recovery resiliency, as well as continuing to use the data center when they must have total control of the application. ...

DevSecOps is important and here is why
Friday, October 20, 2017 by Richard Harris
In the digital age, securing your development projects against malicious hackers can be quite the challenge. And when you take security and try to scale security to an enterprise, the challenge seems insurmountable. Evident by the frequent hacking incidents we see come through the news.Enter DevSecOps. DevSecOps is a methodology that interweaves the aspects of DevOps an...

Checkmarx acquired Codebashing
Tuesday, July 25, 2017 by Austin Harris
Checkmarx has acquired Codebashing, an application security education company that delivers Game-like AppSec Training for Developers.Traditional secure coding education is ineffective and cannot scale to deliver continuous and across the board secure coding knowledge. Long training courses disrupt the developer’s daily routine and don't address the specific challenge as...

VASCO launches overlay detection in DIGIPASS
Thursday, June 22, 2017 by Richard Harris
VASCO Data Security International, Inc., a provider of identity, security and business productivity solutions, has announced its ability to help organizations detect and mitigate mobile application overlay attacks through added functionality in the DIGIPASS for Apps Runtime Application Self-Protection (RASP) module.Overlay attacks are increasingly being deployed to stea...

Why runtime application selfprotection is critical for app security
Tuesday, June 20, 2017 by David Strom
Today most of us go about implementing security from the outside in. The common practice is to start by defining a perimeter and trying to defend it with various security tools. Even though perimeters have been porous for more than a decade, we still can’t give up this notion that if we build a better wall we can keep our enterprises safer.Certainly that is where most e...

A DevOps framework for federal customers
Wednesday, May 17, 2017 by Austin Harris
Last Thursday, President Trump signed an executive order designed to strengthen the cybersecurity of federal networks including moving all federal IT systems to the cloud. The executive order also calls for effective risk management, which includes requiring planning so that maintenance, improvements and modernization occur in a coordinated way and with appropriate regu...
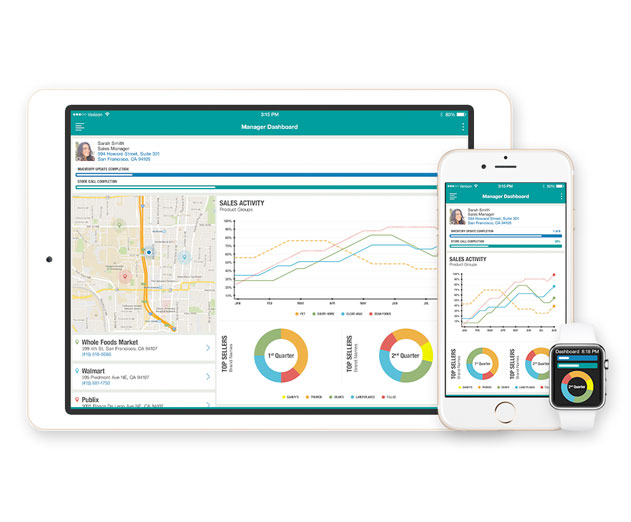
SmartUX 5.0 released so you can make lowcode apps even faster
Thursday, March 23, 2017 by Austin Harris
PowWow Mobile, the enterprise mobility platform that lets you create apps, has announced the latest release of its SmartUX Platform version 5.0. The new enhancements will simplify collaboration between IT and business teams through new levels of speed, visibility, and controls. SmartUX 5.0 is the most powerful platform for the rapid design and deployment of enterprise m...
Mobile and IoT security gets a boost from new PN80T chipset
Tuesday, February 28, 2017 by Richard Harris
NXP Semiconductors N.V. has unveiled its new PN80T embedded Secure Element (SE) and NFC solution. It is the Industry’s first 40nm SE and is designed to ease development and implementation of an extended range of secure applications for any platform including smartphones, wearables, and the Internet of Things (IoT).A user experience built around NFC use casesThe new PN80...

New Cloudflare Apps platform to deliver accessibility for customers and developers
Thursday, December 15, 2016 by Richard Harris
Cloudflare, an internet performance and security company, has announced the acquiring of Eager Platform Co., an app platform for web property owners. The acquisition joins Cloudflare’s global network with Eager’s platform to create a next-generation app platform experience that is secure, seamless, and easy to use for customers of all technical backgrounds.The platform ...
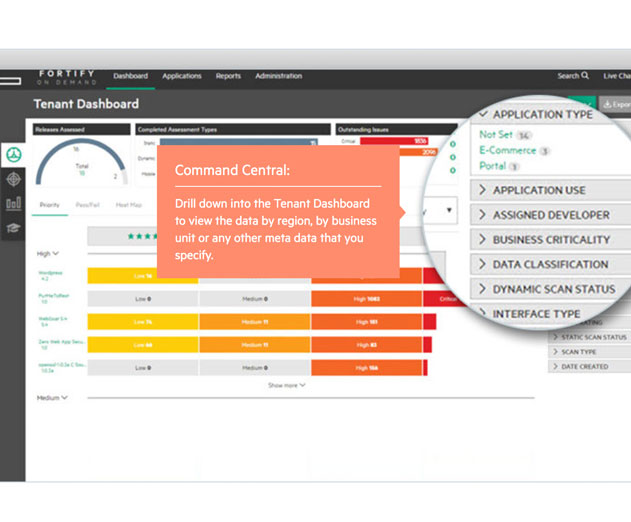
Hewlett Packard Enterprise Introduces New Application Security Solutions
Monday, September 19, 2016 by Richard Harris
Hewlett Packard Enterprise (HPE) has introduced the HPE Fortify Ecosystem and Fortify on Demand (FoD) continuous application monitoring service. The online marketplace and service are designed to help organizations create secure applications by naturally integrating security testing processes and resources throughout the fast-paced software development lifecycle (SDLC)....
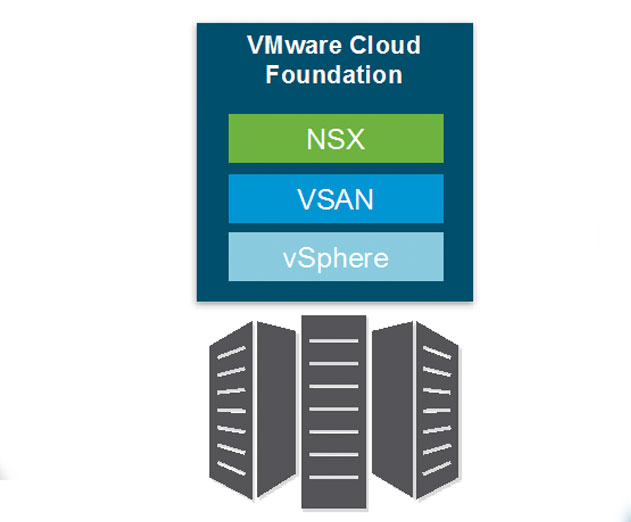
Hybrid Cloud Strategy New With VMware CrossCloud Architecture
Tuesday, August 30, 2016 by Stuart Parkerson
VMware has announced a new aspect of its hybrid cloud strategy with the new VMware Cross-Cloud Architecture which provides the ability to run, manage, connect, and secure applications across clouds and devices in a common operating environment.In support of the company's cloud strategy, VMware also announced the following:- VMware Cloud Foundation is a unified...

Checkmarx Tells Us Why App Developers Should Care About App Security
Thursday, August 18, 2016 by Richard Harris
We recently had a conversation with Emmanuel Benzaquen at Checkmarx to talk about how they are able to scrutinize code with a fine-toothed comb and find vulnerabilities early and why other developers need to be doing the same. With clients such as Coca-Cola, SAP, and Salesforce, they seem to be carving out a niche for application security in the crowded tech-s...

Don't Expect Apple and Google to Do App Security for You
Tuesday, May 24, 2016 by Sinan Eren
The appetite for mobile apps with an appealing user experience shows no signs of slowing – even in closely regulated industries such as financial services and healthcare. In fact, according to Gartner, by the end of 2017, IT organizations will be hard-pressed to meet market demand for mobile app development services as it grows at least five times faster than IT’s abili...
Five Common Mobile App Security Vulnerabilities And How to Fix Them
Saturday, April 30, 2016 by Seth Jaslow
Mobile app security leaves much to be desired. That was the conclusion of a 2016 Hewlett Packard Enterprise (HPE) study which found that a staggering 96 percent of 36,000 mobile apps failed at least one of 10 privacy checks. Three years ago, a similar HPE study found that 97 percent of 2,000 apps reviewed held insecure private information. As mobile app usage conti...

Delphix 5.0 Release Offers Fully Integrated Data Masking
Thursday, April 7, 2016 by Stuart Parkerson
Delphix had announced technology enhancements to it data operations platform designed to accelerate and simplify secure application development in the data center and in the cloud. Delphix 5.0 introduces a new data-masking capability, Selective Data Distribution, support for IBM DB2 and expanded support for Oracle E-Business Suite. The Delphix platform is offered a...

Real World Insight Into Docker's New Datacenter Platform
Wednesday, March 9, 2016 by Richard Harris
We visited with Sven Dummer, senior director of product marketing at Loggly, to discuss Docker’s recent announcement of the Docker Datacenter (DDC), an integrated, end-to-end platform for agile application development and management that companies can use to deploy an on-premises (on in a virtual private cloud) Containers-as-a Service (CaaS) solution (CaaS is ...

New Docker Datacenter Offers an End to End Platform for Agile Application Development
Wednesday, February 24, 2016 by Stuart Parkerson
Docker has released the new Docker Datacenter (DDC), an integrated, end-to-end platform for agile application development and management. Docker Datacenter addresses the requirements for companies that want to manage the application lifecycle of Dockerized applications from development through production.The platform includes the Docker Universal Control Plane (now gene...
VMware AirWatch 8.3 Release Includes Enhanced Security Functionality
Sunday, February 21, 2016 by Richard Harris
The latest rendition of the VMware AirWatch Enterprise Mobility Management (EMM) platform, AirWatch 8.3, has been released now providing support for the VMwareWorkspace ONE app to help organize app access and eliminate the need for passwords. It also expands the AirWatch Privacy First program with a user-facing website and visual privacy notice to mitigate concerns thro...

New Security Report Reveals Increased Threat for Mobile Applications
Sunday, February 21, 2016 by Stuart Parkerson
According to a new cyber security report, mobile applications increasingly have become top security threats plaguing enterprises over the past year. The details are outlined in the recently published Hewlett Packard Enterprise (HPE) Cyber Risk Report 2016.As the company points out in the report, traditional network perimeters are disappearing allowing attack surfaces to...
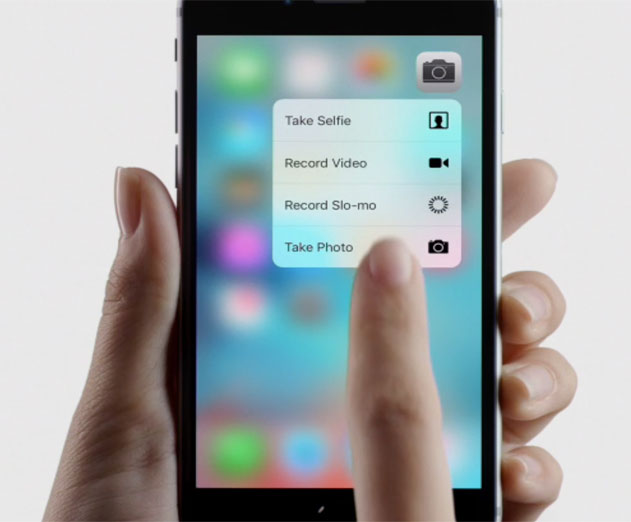
Why 3D Touch is Going to Change the Way We Interact with Mobile
Wednesday, December 30, 2015 by Richard Harris
We recently visited with Michael Wass of Shinobicontrols to discuss the impact of 3D Touch on mobile app development. Shinobicontrols creates interactive UI controls for iOS and Android developers.ADM: Why is 3D touch going to change the way we interact with mobile?Wass: 3D Touch solves a lot of problems with mobile, and a lot of the inherent problems with iOS. Much of ...

New Report Shows Companies Are Increasingly Adopting Custom Apps
Tuesday, December 1, 2015 by Richard Harris
Good Powered by BlackBerry (formally Good Technology, which was purchased by BlackBerry in November) has released its thirteenth Good Mobility Index Report, showing that organizations are increasingly building custom secure apps. The Q3 report offers a snapshot of the activities of Good customers. In addition to an increase towards custom apps, the report showed a ...

Appmobi Provides Enterprise Security to Hybrid HTML5 and Cordova Mobile Apps
Tuesday, November 10, 2015 by Richard Harris
Appmobi has released the new Appmobi Secure Mobile Platform providing enterprise-grade security to hybrid HTML5 and Cordova mobile apps. The Appmobi Secure Mobile Platform integrates and works with a developer’s existing development tools, providing the services required to build secure hybrid apps in an easy-to-install package that can be hosted on an enterprise’s priv...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|