byod
byod magazine search results
App Developer Magazine issues we found relating to byod
Sept13 Issue: Mobile Security In the Age of BYODInside this issue we have the Top Global Apps report from Distimo you won't want to miss! NTIA's code of conduct for app developers and how it's going to affect your app development efforts, why push notifications should be a part of most apps, what to consider with COPPA compliancy when developing apps, everything you need to know about app store optimization, and loads more! |
byod news search results
Developer news items we found relating to byod
35 results
Software-defined perimeter market is set to grow
Friday, August 5, 2022 by Brittany Hainzinger
The software-defined perimeter market is expected to increase at a CAGR of 14.3% from USD 7.4 billion in 2022 to USD 28.2 billion through 2032. The increased need for policy-based security architecture to decrease network complexity and the growing demand for cloud-based applications are other factors expected to influence the software-defined perimeter market trends...

Automated testing in 2022
Friday, January 14, 2022 by Richard Harris
Ajay Dawar, Alok Kulkarni, James Isaacs, and Linda Chen from Cyara discuss their 2022 predictions about real-time quality assurance, adopting automated testing, balancing employee experience and innovation, how to deliver innovative customer experiences, why AI won't displace humans for customer support, how enterprises can achieve digital transformation success, an...

Cyvatar raises 9 million for cybersecurity as a service model
Monday, June 21, 2021 by Brittany Hainzinger
Cyvatar announced that it has raised $9 million as part of its Series A financing to help scale and serve its rapidly growing customer base and continue to drive the adoption of its innovative cybersecurity-as-a-service (CSaaS) model. Cyvatar raises 9 million for cybersecurity as a service model Escalating cybersecurity breaches and the need to addr...

Using any app or device to do your job is a growing trend
Tuesday, June 11, 2019 by Richard Harris
The majority of global workers are going rogue with work devices, software and applications despite being aware of the potential business risks involved, according to new research released by Snow Software. The study, which polled 3,000 professionals in the United States, Europe, and Asia Pacific, finds stark contrasts between the mindset of today’s workers and th...

Mobile app testing market to be valued at $13.3B by 2026 report says
Monday, May 13, 2019 by Richard Harris
The mobile application testing solution market is anticipated to witness significant revenue growth during the forecast period, owing to rising demand across commercial and corporate sectors. Requirements for regression testing, the need to tackle issues caused due to device diversity, and increasing mobile applications such as m-commerce are the major drivers for the r...

Cell carrier quality and performance is getting better says J.D. Power
Monday, July 23, 2018 by Austin Harris
Unlimited data plans are the magic elixir for wireless network quality, while “bring your own device” promotions are having the opposite effect, according to the J.D. Power 2018 U.S. Wireless Network Quality Performance StudySM - Volume 1. The study finds that customers with unlimited data plans experience a lower incidence of overall network problems, data ...

Rethinking your mobile app testing tools
Friday, February 9, 2018 by Richard Harris
Using mobile app testing tools, or software QA tools usually tells developers something they don't want to hear - their software is broken somewhere. Over the years, testing apps and software has become more laborious than is should be, but a necessary evil when targeting multiple platforms and devices in today's dizzying world of mobile hardware.Rainforest is on a miss...
App developers find Holiday campaigns challenging
Thursday, October 19, 2017 by Richard Harris
YouAppi has announced the results of a comprehensive survey that evaluated U.S. consumers on their personal holiday shopping habits and preferred mobile holiday experience. The survey also questioned global digital marketers, advertisers and app developers on their 2017 mobile holiday preparation and campaign plans. While 95 percent of businesses see the holiday season ...

Get mobile printing up and running: What CIOs need to know
Wednesday, May 24, 2017 by Brent Richtsmeier
Enterprise workplace infrastructure is changing. Gartner found that total mobile sales into the enterprise globally are greater than 200,000 per year, while PCs are half that. The PC installed base has been on a steady decline since 2014, while the mobile installed base is on the rise - meaning mobile is set to surpass the PC installed base in 2017.However, even as more...

Demand for mobile print solutions are on the rise
Thursday, May 11, 2017 by Christoph Schell
Understanding the opportunity for mobile printing in the workplace first requires rejecting the notion that the enterprise has abandoned much of its need for printing and paper records. Digital forms and workflows may be reducing the amount of paperwork, yet many organizations still rely on hard-copy contracts, government forms and reports to support business processes ...

How companies can keep their remote teams safe
Monday, April 3, 2017 by Gene Richardson
If you hate bringing your work home with you, spare a thought for the 3.7 million Americans for whom home is the workplace.The telecommuter population is growing faster than the overall employee base, according to Global Workplace Analytics, and with half of all jobs deemed suitable for performing from home, it is a trend that is set to go on growing. Already, around a ...

Why MicroApps are an emerging development trend to watch in 2017
Monday, January 30, 2017 by Paul Swaddle
With SMEs(Small and Medium-sized Enterprises) emerging every day, the apps world has seen a swift growth in the enterprise apps category. MicroApps help users restructure, streamline, and in turn manage a crucial business processes. MicroApps provide a highly focused, task-based functionality that let users access the app, interact and then close the app all with maximu...

Prevent disasters with risk management and being a grown up!
Friday, January 27, 2017 by Gordon McKeown
We live in an era of dramatic, improbable events that adversely affect the economy, the environment, the fate of household name companies and people’s welfare and health. Or at least they seem improbable until they hurl themselves violently upon us from the shadows of our agreeable ignorance. Strangely, with hindsight they often appear inevitable. Bloated, failed banks ...
Enterprise BYOD post holiday woes
Tuesday, January 24, 2017 by Mitch Black
Bring Your Own Device (BYOD) programs are a constant enterprise challenge. For unprepared organizations, the holidays can be especially difficult.Christmas to New Year’s Day is typically a peak time to purchase and/or download apps, so how can your enterprise effectively enroll an influx of new users and devices without compromising program security? While the recent ho...

Predictions from Red Hat for 2017
Saturday, December 24, 2016 by Richard Harris
Catching up with Red Hat’s mobile team on what they’re expecting to see in mobile and IT in 2017.1. Prediction: Mobile goes mainstream as part of enterprise application strategy that hinges on containers, DevOps, and microservices. There are more mobile devices in circulation than the global population and mobile searches now outstrip those from PCs; mobile can no ...
What's so tricky about Android security anyway
Monday, December 12, 2016 by Don Duncan
Android authentication can be a tricky business because it can help identify the user, but it can also open the door to hackers at the same time. It all comes down to the device administrator access which comes with a lot of benefits like. Device administrator access provides complete device management access rights that include creating and managing poli...

Virtual Desktop Infrastructure: The way forward in government mobility
Monday, November 28, 2016 by Edris Amiryar
Advances in technology are rapid and can be hard to keep up with, especially for large organizations. The federal government relies heavily on IT to accomplish its tasks and there is increasing demand for access to information from any location, in any geography, meaning that for federal agencies, improved mobility and mobile data security are imperative for m...

The growing gap between the speed of business and the pace of software development
Monday, October 17, 2016 by Richard Harris
The rapid pace of business today is only increasing, which means companies need quick access to effective, flexible and scalable technology in order to succeed. IT organizations are simply struggling to keep up with this growing demand for business applications, which can’t be developed fast enough, updated often enough, or maintained well enough. It’s a com...

SOTI MobiControl 13.2 Ships to help enterprises manage devices
Monday, October 17, 2016 by Richard Harris
SOTI Inc. announced the availability of SOTI MobiControl 13.2. MobiControl provides mobility management across all endpoints, seamlessly managing mobile devices, connected peripherals, applications, content, and security from within a single management console.Version 13.2 of SOTI’s flagship product, is now improved with a variety of powerful new features, includin...

What the mobile AR phenomenon has taught us about security
Thursday, October 13, 2016 by Aaron Lint
The extraordinary success of Pokémon Go has been surprising, even in the rapidly changing paradigm of the mobile application space. The game, which allows users to hunt down and capture virtual monsters, uses Augmented Reality (AR) technology to display the creatures in real world locations such as parks, homes, and offices.Pokémon Go has already broken five Guinness Wo...

Apple developer patents, hacks, and iOS 10 oh my! October issue lands
Saturday, October 1, 2016 by Richard Harris
It’s hard to believe - but fall is upon us and 2017 is right around the corner. October always ushers in the feeling of campfires, fall-festivals, and what the flip and I going to do with my apps for the holiday season coming up! Not to worry everyone - our October issue is here, and it’s over 90 pages of industry news, tips, and articles ...

BYOD nightmare: Pokemon Go
Wednesday, September 7, 2016 by Mike Cobb
Pokémon Go, the smartphone game that became an overnight worldwide sensation, may be more than the latest technology must-have. The cute augmented reality app could actually provide cybercriminals an entry point to your business and personal files.Company security directors were already wringing their hands over employees who mix their work and private information on th...

Beware: Zombie Apps Are on the Rise
Monday, August 22, 2016 by Richard Harris
Zombie apps appear to be a quite recent and infectious discovery. Once installed, they drain your phone of life. But what are they, and where do they come from? Zombie apps are the applications that, at first glance, appear harmless. Developers usually create zombie apps as an app that is rarely used – like a flashlight app – but the app’s software constantly ...

The Impact of BYOD on Developers
Friday, July 1, 2016 by Mitch Black
From Security Research Labs breaking into a phone within seconds on 60 Minutes earlier this year to the Apple/FBI debacle, it’s increasingly clear that enterprises have varying levels of device security protocols in place. Surprisingly, the responsibility of ensuring vital data remains secure, especially as BYOD policies and a mobile-first workforce become the norm...
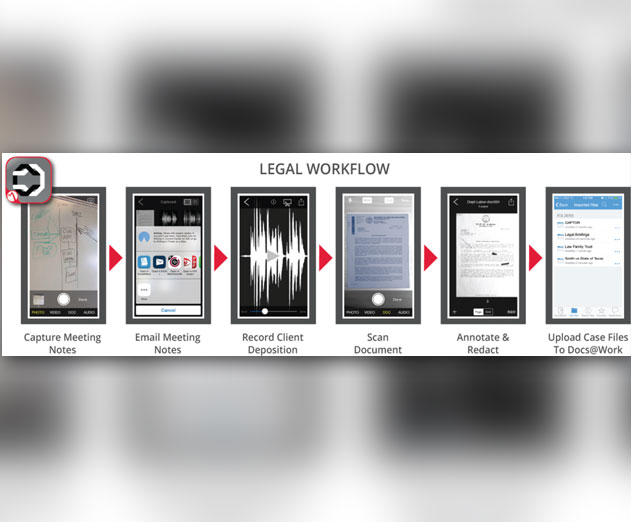
IT Governance of Sensitive Files on Corporate and BYOD Mobile Devices
Monday, June 20, 2016 by Jeff Steuart
Mobile content has brought new agility and efficiency to just about every enterprise. "Mobile communication and collaboration is accelerating and improving enterprise productivity and growth like no other universal technology since the dawn of the Web 25 years ago,” says Josh Bohls, Founder, Inkscreen. But these advantages come at a cost.Says Bohls, “Ask any o...
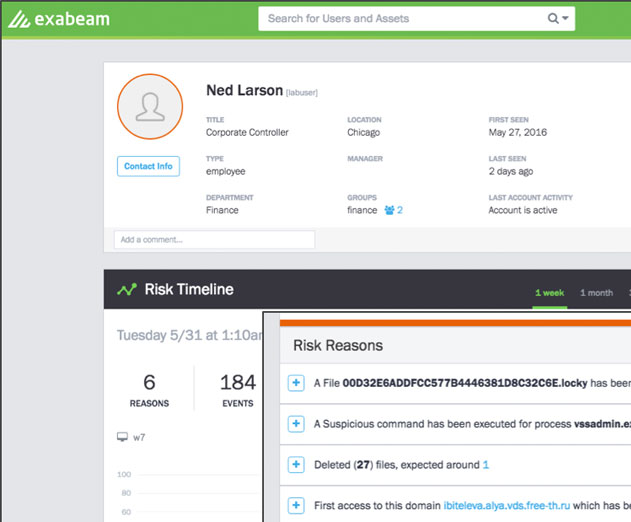
Exabeam Releases Security Intelligence Platform for Early Detection of Ransomware
Thursday, June 16, 2016 by Richard Harris
Exabeam has released Exabeam Analytics for Ransomware, a new behavior-based security intelligence platform designed for early detection of ransomware across a corporate network. Exabeam can detect ransomware movement and activity in the network, the servers, workstations, BYOD devices, and cloud services.Exabeam detects ransomware as it first enters the network and begi...

Application Security Market to Triple in the Next 5 Years
Wednesday, May 11, 2016 by Stuart Parkerson
A new market research report has been published by MarketsandMarkets which predicts that the global application security market size is expected to triple, growing from $2.24 Billion in 2016 to $6.77 Billion by 2021. The report is titled “Application Security Market by Component (Solutions, Services), Solutions (Web Application Security, Mobile Application Security), Te...
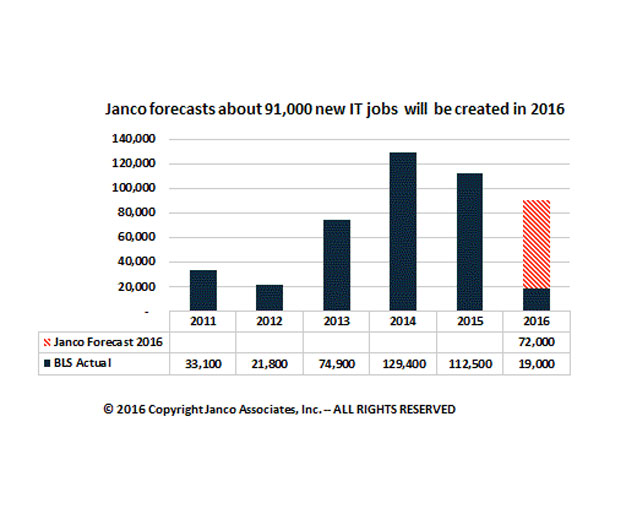
The Current State of IT Hiring and Employment in the United States
Thursday, April 21, 2016 by Richard Harris
According to a recent report, compensation for all IT professionals has increased by 1.39% between January 2015 and January 2016. The data was made available through the 2016 IT Salary Survey which is produced by Janco and eJobDescription.com.The report shows that the total mean compensation for all IT professionals increased from $81,583 to $82,483. In large enterprise...

How March Madness Impacts Enterprise Mobile Data Usage and BYOD Security
Tuesday, April 5, 2016 by Richard Harris
Oversized events like March Madness and the Olympics not only can cause decreased productivity from employees, but also may increase security risks for companies whose employees are using devices that access corporate data. We visited with Michael Covington, VP Product for Wandera, to discuss research the company conducted during the NCAA basketball tournament to learn ...

MDM Policies Could Make You Feel Like a 5th Grader on iOS
Tuesday, April 5, 2016 by Chris Hazelton
Apple recently released its iOS 9.3 update which will add new features for enterprise mobility management (EMM) vendors to control the look and feel of Apple iOS devices with mobile device management (MDM) profiles. The primary purpose of these capabilities are for the education vertical where shared devices can focus students on classroom materials. That said, wit...

A Developer's Perspective on Mobile Security in the Age of BYOD
Thursday, March 31, 2016 by Joe Schulz
With the cost savings of BYOD continuing to lure organizations to adopt this approach, the number of companies allowing employee-owned devices is still on the rise, as well. In early 2015, Tech Pro Research announced that 74 percent of organizations either already allow or were planning to allow employees to bring their own devices to work. At the time of this writing, ...

March Madness Apps May Be Accessing Your Data
Tuesday, March 15, 2016 by Stuart Parkerson
In its mobile app risk assessment report “March Madness or April Foods” Flexera Software highlighted BYOD security issues by analyzing the annual March Madness craze as employees are using apps on their corporate and BYOD devices to stream content, complete brackets and track March Madness activities.The report focused on what data these apps access, what device feature...

Using Virtual Mobile Infrastructure to Protect Corporate Data
Saturday, March 5, 2016 by Stuart Parkerson
We chatted with Avast Vice President Sinan Eren to talk BYOD mobile security and how the Avast VMP solution provides companies with the ability to create a virtual mobile infrastructure (VMI) that streams mobile apps to any device. Sinan is a cybersecurity expert, who has extensive knowledge in both the engineering and business aspects of security. ADM: What is the...

Secure Mobile Access for BYOD
Friday, March 4, 2016 by Paul Andersen
If you are an IT manager responsible for defining your organization’s approach to BYOD, there are hundreds, if not thousands, of articles and guides available on the topic. Unfortunately, most BYOD articles overlook a technology that has been the workhorse for secure remote access for more than a decade: SSL VPN.Originally designed for secure remote PC and laptop access...
VMware AirWatch 8.3 Release Includes Enhanced Security Functionality
Sunday, February 21, 2016 by Richard Harris
The latest rendition of the VMware AirWatch Enterprise Mobility Management (EMM) platform, AirWatch 8.3, has been released now providing support for the VMwareWorkspace ONE app to help organize app access and eliminate the need for passwords. It also expands the AirWatch Privacy First program with a user-facing website and visual privacy notice to mitigate concerns thro...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|