android security
android security news search results
Developer news items we found relating to android security
15 results
Not all security vulnerabilities are created equal
Tuesday, May 25, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function, value and, unfortunately, they also provide one of the easiest openings for cybercriminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the concept o...

Six areas of focus for continuous security
Friday, April 16, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function and value and, unfortunately, they also provide one of the easiest openings for cyber criminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the conce...

Stop the menace of Android rooting malware attacks with RASP
Monday, September 25, 2017 by Frederik Mennes
One of the key security issues facing organizations that support Android devices is the risk of rooting malware. A number of malware families on the Android mobile OS attempt to obtain root access once installed because the elevated privileges gained come in handy to perform malicious activities. What you need to know about Tordow v2.0 and Pegasus The To...

Big Nerd Ranch developers to talk at Georgia World Congress Center
Wednesday, February 22, 2017 by Richard Harris
Big Nerd Ranch, an immersive application development bootcamp and app development learning service announced today that four of their training staff will be featured speakers at DevNexus, The Professional Developer Conference, being held February 22 and 23, 2017, at the Georgia World Congress Center in Atlanta, Georgia."We are very pleased that Big Nerd Ranch is well re...

Ransomware facts and the steps to prevent it on your device
Friday, December 30, 2016 by Richard Harris
As technology advances forward, so does its unintended consequences and evolution of bad people being able to exploit its weaknesses. Reports of one these exploits is sweeping across Europe, its name is ransomware. Ransomware is malware that allows hackers to take control of your computer and all its data, and then hold it hostage via encryption until a certain sum of m...

Pegasus Network Inc launches WeShare WiFi SDK
Wednesday, December 21, 2016 by Richard Harris
As advertising space becomes more and more saturated with content, a glaring problem emerges from the success. User's are becoming more and more inundated with streams of traditional advertising causing them to become increasingly desensitized to the messages being conveyed. This drop in interactivity can cause a drag on user acquisition costs and retention rates in the...

Powered by Epoxy is working!
Thursday, December 15, 2016 by Richard Harris
Epoxy, Inc. is the developer of the Epoxy App, an application for iPhone iOS and Android operating systems. It is a smartphone application designed to connect business owners and consumers to ease marketing frustrations.They have seen good results with its response to the "Powered by Epoxy" addition to their business model. The new addition is allowing their compan...
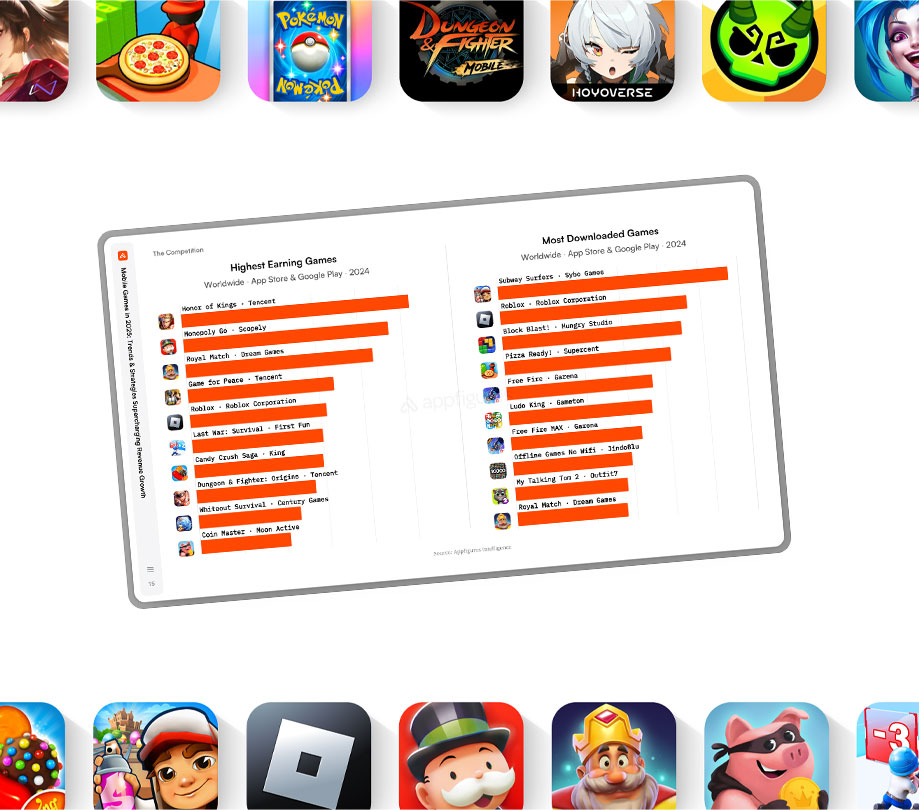
Mobbo released a new report on the state of mobile SDK's
Thursday, December 15, 2016 by Austin Harris
Mobbo just released its Power Index, which offers app publishers and marketers robust benchmarks of mobile app SDK components, helping them to make informed decisions about the best technology stacks. The report sheds light on the scale and performance of popular SDK components and tracks the movers and shakers in the mobile industry. Key Findings in the report:- 80% of...

What an advanced threat approach for cloud security must address
Wednesday, December 14, 2016 by Austin Harris
Headlines about hacking and malware prove that traditional security methods are not up to the task of protecting organizational infrastructures and data from theft and ransomware. As more organizations embrace cloud-first platforms for everything from customer relationship management (CRM) to enterprise resource planning (ERP) platforms and beyond, they place themselves...
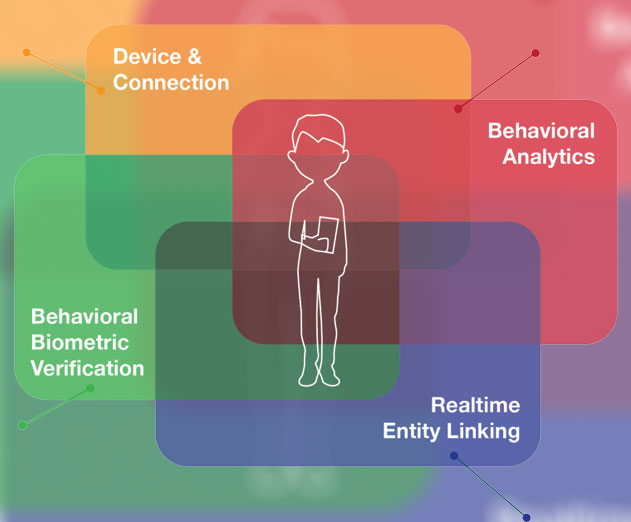
What's so tricky about Android security anyway
Monday, December 12, 2016 by Don Duncan
Android authentication can be a tricky business because it can help identify the user, but it can also open the door to hackers at the same time. It all comes down to the device administrator access which comes with a lot of benefits like. Device administrator access provides complete device management access rights that include creating and managing poli...

Using Virtual Mobile Infrastructure to Protect Corporate Data
Saturday, March 5, 2016 by Stuart Parkerson
We chatted with Avast Vice President Sinan Eren to talk BYOD mobile security and how the Avast VMP solution provides companies with the ability to create a virtual mobile infrastructure (VMI) that streams mobile apps to any device. Sinan is a cybersecurity expert, who has extensive knowledge in both the engineering and business aspects of security. ADM: What is the...
Choosing Your Next Industrial Mobility OS
Tuesday, September 1, 2015 by Mark Kirstein
With Windows Mobile and CE About to Sunset, Android and Windows 10 are Tomorrow’s Top OptionsToday’s mobile operating system landscape presents choices for industrial enterprises when it comes to selecting the platform upon which their applications should be built. When you think about a global enterprise distributing internal mobile solutions, you’re talking about...

Google Offers Up to $30k Bounties for Discovering Android Vulnerabilities
Friday, June 19, 2015 by Richard Harris
Google has announced a new Android Security Rewards program to encourage the Android developer community to discover vulnerabilities and disclose them to the Android Security Team. The reward level is based on the bug severity and payments are elevated for high quality reports that include reproduction code, test cases, and patches.The program covers security vulnerabil...

Diamond Fortress Technologies Provides Biometric Identity SDK for Android App Developers
Tuesday, May 6, 2014 by Richard Harris
Diamond Fortress Technologies is now offering Android developers ICE Unlock, a platform that unlocks an Android device via the user’s fingerprint. A touchless biometric solution, ICE Unlock utilizes the device’s camera and complex mathematics to create a high quality map of a fingerprint and to verify identity. ICE Unlock works with existing hardware on more t...

Google Confirms Security Compromise in Android Apps Using Java Cryptography Architecture (JCA)
Wednesday, August 14, 2013 by Richard Harris
Today on Google's Developer blog, Alex Klyubin, Android Security Engineer confirms they have found a serious security compromise in Android apps that use JCA for certain functions such as key generation and signing, or random number generation.Alex says, "We have now determined that applications which use the Java Cryptography Architecture (JCA) for key generation, sign...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|