security app
security app news search results
Developer news items we found relating to security app
35 results
Cybersecurity in 2025
Tuesday, February 4, 2025 by Richard Harris
Timothy Hollebeek shares his insights on the key cybersecurity trends shaping 2025, focusing on the evolving landscape of digital trust and identity. As quantum computing and AI continue to advance, they bring both groundbreaking innovations and new cybersecurity risks. The introduction of Google’s Willow chip signals a new era of quantum technology, accelerating ...

Generative AI in Application Security report from Checkmarx
Monday, August 12, 2024 by Richard Harris
Checkmarx, the in-cloud-native application security provider, has published its Seven Steps to Safely Use Generative AI in Application Security report, which analyzes key concerns, usage patterns, and buying behaviors relating to the use of AI in enterprise application development. The global study exposed the tension between the need to empower both...

Apps Americans trust the least
Thursday, February 23, 2023 by Brittany Hainzinger
Pull out your phone…it’s time to see if you have any of America’s least trusted apps. As easy as it is to download an app, it’s also easy for providers to collect & possibly distribute your data. So, Secure Data Recovery conducted a study to find out which apps Americans trust, and which collect the most data. A survey from Secure Data...

Intelligent IoT Network lands from Aeris
Tuesday, February 15, 2022 by Richard Harris
Aeris, the Internet of Things (IoT) solutions provider has announced the next generation of its Intelligent IoT Network, a unique suite of Machine Learning and Artificial Intelligence (AI)-based capabilities that enable superior global IoT connectivity and network performance, increased security performance, and best-in-class IoT network support. The Aeris Intelligent I...

Low code platform Zenity lands $5M in funding
Wednesday, December 8, 2021 by Austin Harris
Zenity exited stealth mode with a $5 million seed funding round, led by Vertex Ventures and UpWest, and backed by top executives such as the former CISO of Google, Gerhard Eschelbeck, and former CIO of SuccessFactors, Tom Fisher. With Zenity, businesses can promote citizen development and adopt Low-Code/No-Code platforms while avoiding critical data exfiltration or disr...

Gitlab 12.0 released
Friday, June 28, 2019 by Austin Harris
GitLab is releasing 12.0 to help enterprises transform and accelerate DevOps adoption by bringing developers, operations professionals, and the security team together in the first single application for the entire DevSecOps lifecycle. With the 12.0 release, GitLab is building upon security features recently released - such as security dashboards, auto remediation and se...

Crowdsourced security and bug bounty adoption is spreading
Monday, May 20, 2019 by Richard Harris
There continues to be a fundamental imbalance in cybersecurity. Attackers are finding new ways to penetrate cyber defenses as targets proliferate to the cloud, mobile, and connected devices. Defenders need to take a proactive security approach. The evolving threat landscape and the ever-widening security skills gap are giving rise to new approaches such as crowdsourc...
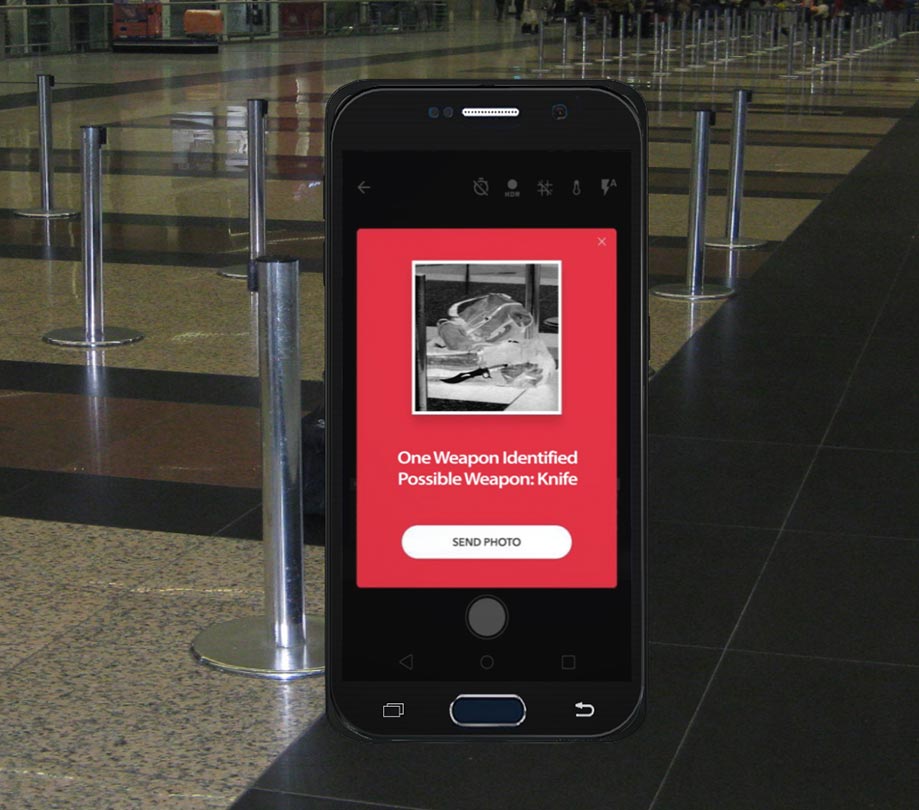
SWORD attached smartphone device can detect weapons and explosives
Thursday, June 7, 2018 by Richard Harris
The urgent challenge for security personnel to noninvasively scan people in real time and in public to detect and “see” if they are carrying weapons or explosives without physically searching them could soon be solved with the launch of SWORD by Royal Holdings Technologies Corporation (Royal Holdings). SWORD attaches to a Google Pixel 2 XL smartphone and ...

Why developers run away from security updates
Monday, April 16, 2018 by Richard Harris
Veracode, Inc. has released new data that shines a light on the discrepancy between component security and hygiene. According to the research conducted with Vanson Bourne, only 52 percent of developers using commercial or open source components in their applications update those components when a new security vulnerability is announced. This highlights organizations’ la...
What the Section 702 bill means to your digital privacy
Wednesday, January 24, 2018 by Austin Harris
Recently, President Trump signed the Section 702 bill “to reauthorize foreign intelligence collection.” The NSA warrantless surveillance program is still a sweeping up Americans’ online communications, even though Trump has tweeted:“This is NOT the same FISA law that was so wrongly abused during the election. I will always do the right thing for our country and put the ...

TapSafe warranty app launches at CES
Monday, January 15, 2018 by Richard Harris
TapSafe, a new warranty app and platform, will help consumers find, identify and protect all of their connected devices. The new product, developed by AmTrust Innovation, the products and services innovation arm of AmTrust Financial, allows users to buy warranty protection and technical support for any connected devices. Nearly three-quarters (74%) of US households have...

Cisco releases security connector app for iOS devices
Tuesday, January 2, 2018 by Austin Harris
Cisco announced the availability of Cisco Security Connector, a security app designed to give enterprises the deepest visibility and control over network activity on iOS devices, now in the App Store.Apple has designed iOS to be secure from the ground up and to be simple, intuitive, and powerful for users. By using iPhones and iPads with iOS 11 and Cisco Security Connec...

The battle of biometric security coming in 2018
Friday, November 3, 2017 by Kevin Tussy
Fingerprint sensors first appeared in smart devices in 2007 and then gained momentum as a 4-digit PIN code replacement in 2013's Apple iPhone 5S. Hailed as the future of authentication by some, fingerprint's security weaknesses were quickly exposed by the children of sleepy dads, cats' paws and gummy bears. Still, the lure of convenience today and the promise of securit...

Sending out an S.O.S. for SMS
Wednesday, October 4, 2017 by Will LaSala
What a difference a year makes. Just one year after the National Institute of Standards and Technology issued guidance that found SMS is insecure and no longer suitable as a strong authentication mechanism, it has walked all of that back.At the time the original draft was published, it was highly unusual for any US government agency to get out in front of the security i...
Cloud security platform Capsule8 raises $6M
Thursday, September 28, 2017 by Austin Harris
Capsule8 has announced it has completed a $6 million round of funding. This round brings total funding to more than $8.5 million for the security provider, which recently announced the beta version of Capsule8 Protect that is being deployed by some of the biggest companies on Wall Street and in Silicon Valley. Capsule8 will use its latest round of funding to further dev...

Behavioral and biometric mobile authentication will end passwords
Friday, September 15, 2017 by David Vergara
You can say this about passwords: they're incredibly resilient. Not in a bulletproof kind of way but, more precisely, in terms of how long they've been around. According to Robert Svensson in his book "From Hacking to Report Writing: An Introduction to Security and Penetration," the first computer system to use passwords was built by researchers at the Massachusetts Ins...

Improve mobile app security by turning it into code
Monday, May 8, 2017 by Jeff Williams
Why is application security such a pain? One of the hard problems with application security is that there are a zillion different ways that things can go wrong. Far more than any one person can be expert in. It's unfair to think that a software developer, who is already supposed to be expert in all the latest software languages, frameworks and best practices, should als...

Intentbased mobile app security: It's harder than you think
Thursday, March 23, 2017 by John Morello
Recently, intent-based security has become a buzzword and a commonly used phrase in the developer community. However, this new wave of security is much more than just a catchphrase. The concept of intent-based security adds a new level of protection to applications in containerized environments, specifically by understanding what the app is intended to do and looking fo...
Mobile and IoT security gets a boost from new PN80T chipset
Tuesday, February 28, 2017 by Richard Harris
NXP Semiconductors N.V. has unveiled its new PN80T embedded Secure Element (SE) and NFC solution. It is the Industry’s first 40nm SE and is designed to ease development and implementation of an extended range of secure applications for any platform including smartphones, wearables, and the Internet of Things (IoT).A user experience built around NFC use casesThe new PN80...

80 percent of web apps have security flaws
Tuesday, February 14, 2017 by Richard Harris
Data collected by Contrast Labs has revealed that sensitive data exposures, which include missing and weak encryption, are the top vulnerability plaguing 69 percent of web applications and accounting for 26 percent of all vulnerabilities. Their research has also found that 80 percent of tested software applications had at least one vulnerability, with an average of 45 v...

How do we simplify eastwest security The imperative path is upon us
Monday, December 5, 2016 by Keshav Kamble
Ahhh, the endless saga of streamlining hazards around application security: let’s talk about the East-West component of the conundrum. But first, it’s important to clarify the variances of ‘East-West’ vs. ‘North-South’ traffic in a typical data center environment. By definition: North-South traffic is the communication that occurs between server applications deploy...

How Apple's mandatory iOS App Transport Security (ATS) change will affect you
Wednesday, November 30, 2016 by Dominic Tancredi
Major changes are ahead for the mobile industry and as per the usual, Apple holds the keys to all major requirements and changes. In 2015 Apple released iOS 9 and introduced the App Transport Security (ATS) security feature which requires an app to connect to web services over a secure HTTPS connection rather than an HTTP connection. When this feature was released it wa...

All you ever wanted to know about The Cisco Business Cloud Advisor
Monday, November 28, 2016 by Richard Harris
It’s no secret - business cloud utilization is exploding today. In fact, Gartner recently predicted that by 2020, a corporate “No-Cloud” policy will be as rare as a “No-Internet” policy is today. A new Cisco-sponsored global cloud adoption study just released found further thought-provoking trends in cloud adoption. The research, spanning more than 6,100 organ...

Intel Security Enhances Unified Defense Architecture
Thursday, November 3, 2016 by Richard Harris
Intel Security has announced an enhanced unified defense architecture designed to empower organizations to more effectively protect a new digital economy of trust, time and money. No longer is our economy a physical one, but one of connected networks and systems where cybercriminals have put us on the defensive. This new second economy, has put us in a world where ...

The JS Foundation forms to help javascript and servers play nicer together
Monday, October 17, 2016 by Richard Harris
StackPath just announced an official partnership with the Linux Foundation, to form the JS Foundation - an effort put in place to support technologies that complement JavaScript projects. StackPath’s involvement in this foundation results from its mission to integrate top security offerings into development practices. The JS Foundation is committed to helping ...

Aqua Security Announces $9M in Series A Funding Led by Microsoft
Tuesday, September 27, 2016 by Austin Harris
Aqua Security announces it has secured US$9 million in Series A funding, led by Microsoft Ventures. Cybersecurity luminary and investor Shlomo Kramer will be joining Aqua’s Board of Directors. Aqua’s seed investors TLV Partners and Mr. Kramer also participated in this round of funding, bringing Aqua’s total investment to date to US$13.5 million.Aqua was founded in ...

IBM Security Channels Its Inner XMen with Launch of IBM XForce Red Security Division
Friday, August 5, 2016 by Stuart Parkerson
Someone in charge of naming divisions at IBM must have been a big Sci-Fi fan as is evidenced with IBM Security’s name for the a news security task force - IBM X-Force Red. Yep, that’s the name for a new group of IBM security professionals and ethical hackers whose goal is to help businesses discover vulnerabilities in their computer networks, hardware, and software...

A Developer's Perspective on Mobile Security in the Age of BYOD
Thursday, March 31, 2016 by Joe Schulz
With the cost savings of BYOD continuing to lure organizations to adopt this approach, the number of companies allowing employee-owned devices is still on the rise, as well. In early 2015, Tech Pro Research announced that 74 percent of organizations either already allow or were planning to allow employees to bring their own devices to work. At the time of this writing, ...
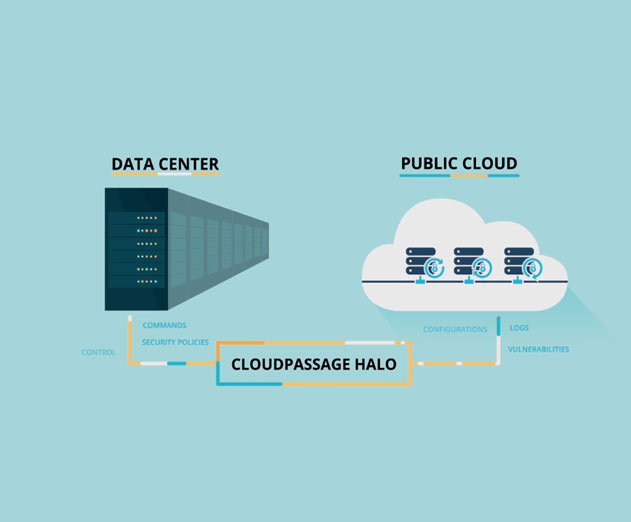
Security Cannot Keep Up with Application Release Cycles
Tuesday, March 8, 2016 by Stuart Parkerson
A recent survey conducted by CloudPassage indicates that a lack of resources may be hindering the ability for companies to embed security in application release cycles stymieing their efforts to implement DevOps.According to the survey:- When asked the stage at which security is brought into software or product development release cycles, more than half of respondents (...
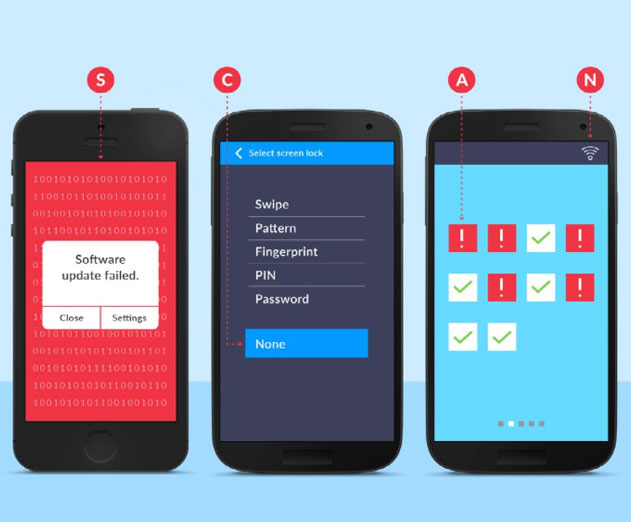
One in Four Android Apps Have High Risk Security Flaws
Friday, February 12, 2016 by Stuart Parkerson
Mobile developers continue to battle security issues with their apps according to a new report by NowSecure. The annual report, 2016 NowSecure Mobile Security Report, provides insight into the current state of mobile security. According to the report a quarter of Android apps have at least one high risk security flaw, 35 percent of communications sent by mobile dev...
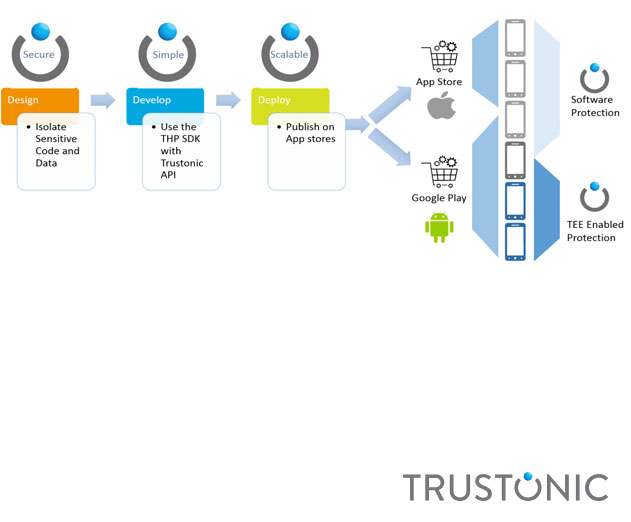
New Trustonic Platform Provides Mobile and IoT Developers with Device Security
Tuesday, February 9, 2016 by Richard Harris
Trustonic has released its "Trustonic Hybrid Protection" (THP) which offers built-in device security providing mobile and IoT developers with an adaptable security solution bringing together software and hardware secured solutions into one hybrid product. Trustonic combines advanced hardware enabled security solutions found in over 500 million devices with software...

Checkmarx Creates Campaign to Help Companies With Security Awareness
Tuesday, October 13, 2015 by Richard Harris
Checkmarx has release a new microsite to help companies raise awareness within their development teams for secure development practices. The campaign provides a kit that includes physical and online tools to promote safe application development within their organization.The physical kit offers a package to help raise awareness within a development organization for appli...
Ravello’s Smart Labs Provides Networking and Security on AWS and Google Cloud
Monday, May 18, 2015 by Stuart Parkerson
Ravello Systems has launched the Smart Labs networking and security platform that combines the functionality of data center labs with the elasticity of AWS and Google Cloud. Ravello’s Smart Labs are powered by a virtual overlay cloud with software-defined networking, with support for running existing VMware and KVM virtual appliances, in a fully fenced environment,...

How to Tap into the Native Advertising Jackpot
Thursday, April 30, 2015 by Mark Rosner
Native ads have already taken over billions of dollars in ad spend, and as one of the fastest growing areas in advertising, they’ve only just gotten started. Publishers like Yahoo and Facebook are bullish on native ads, and for good reason. Yahoo found that native ads get a 3.6x lift in attention over their standard counterparts, and most of Facebook’s $7.9B in ad ...

HP Internet of Things Study Shows Majority of IoT Devices Contain Serious Vulnerabilities
Monday, August 4, 2014 by Stuart Parkerson
HP has released new research, The Internet of Things State of the Union Study, which reveals that 70 percent of the most commonly used Internet of Things (IoT) devices contain serious vulnerabilities. The study is an outgrowth of HP’s OWASP Internet of Things Top 10 Project. The projects goal is to educate the IT community on the main facets of Internet of Things s...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|