Social engineering takeover attacks are on the rise
Thursday, April 18, 2024 by Brittany Hainzinger
OpenSSF and the OpenJS Foundation (home to JavaScript projects used by billions of websites worldwide) are alerting open-source project maintainers of social engineering takeover attacks, following new attack attempts they’ve witnessed similar to the XZ Utils incident.
The OpenJS Cross Project Council received suspicious emails, imploring OpenJS to update one o...
API security risks report exposes Netflix and Wordpress
Monday, November 27, 2023 by Richard Harris
Wallarm, the end-to-end API and app security company, announced the release of its Q3-2023 Wallarm API ThreatStats report. The quarterly report details the surge in threats centered around APIs and uncovers critical vulnerabilities, like injections and API data leaks, that have recently impacted leading firms, including Netflix, VMware, and SAP.
The new report i...
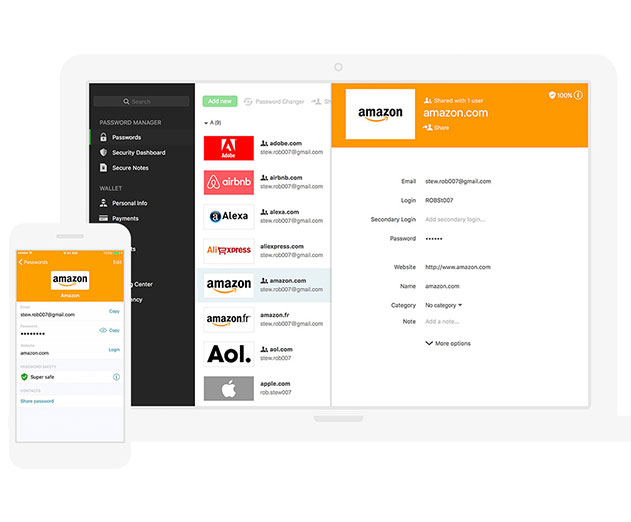
Dashlane enterprise password manage platform launches
Wednesday, September 20, 2017 by Austin Harris
Dashlane announces Dashlane Business 2.0, an enterprise password solution backed by a U.S. patented security architecture. Business 2.0 is a password management solution that strengthens organizational password security and reduces unsecure password sharing. The platform provides visibility into whether employees are reusing passwords across personal and work accounts. ...
Carriers team up to provide better mobile authentication
Thursday, September 14, 2017 by Austin Harris
Mobile users are faced with the challenge of managing dozens of difficult-to-remember passwords for many applications. Even with the best user practices, hackers can social engineer passwords from users, leaving consumers and enterprises vulnerable to identity theft, bank fraud, fraudulent purchases and data theft.To help tackle this issue, AT&T, Sprint, T-Mobile an...
Dashlane to utilize Android's new support for password managers
Monday, May 29, 2017 by Austin Harris
Google announced native support for password managers in Android O and an early preview of Autofill with Google, which in the absence of a password manager, allows the user to use information from Chrome Sync and Google Payments to autofill apps. By offering basic functionality out-of-the-box and making it much easier for users to adopt and use a password management app...
Core Security is making the password reset process selfservice, faster and simpler
Wednesday, November 30, 2016 by Richard Harris
Core Security announced the release of Core Mobile Reset 1.0 and Core Access Insight 9.2. With the introduction of these solution updates, enterprise security teams will now be able to resolve immediate threats with prognostic analytics applied to the big identity and access data, while also enhancing organizational efficiency.Ineffective password management i...
New research shows that using advanced security drives new business growth
Wednesday, October 12, 2016 by Austin Harris
A global study from CA Technologies revealed that organizations are measuring the success of IT security beyond just breaches and compliance; they now are including business performance indicators that contribute directly to revenue growth. The study, The Security Imperative: Driving Business Growth in the App Economy, polled 1,770 senior business and IT executives, inc...
Why Privileged Identity Management is Critical for Secure IT Outsourcing
Thursday, January 21, 2016 by Richard Harris
We visited with David McNeely, VP of Product Strategy at Centrify, to talk about why secure privileged identity management is critical as more of today’s businesses are outsourcing IT functions and relying on vendors to troubleshoot systems and applications. Centrify recently released a new privileged identity management solution supporting federated privileg...
Bomgar Platform Updates Secures Cloud Users Against Cyberattacks
Monday, September 14, 2015 by Richard Harris
Bomgar has released the latest version of its Privileged Access Management solution, which provides security professionals with the ability to control, monitor, and manage access to critical systems by privileged users and third-party vendors. Bomgar’s approach allows companies to enable controlled system access and defend against cyberattacks without requiring com...
Chupamobile Announces Winners of 2013 Developer Competition
Saturday, February 15, 2014 by Richard Harris
Chupamobile has announced the winners of its 2013 Developer Competition. The winners were chosen from a number of submissions to Chupamobile’s online marketplace where developers buy and sell app source code packages and components for a variety of mobile development languages and frameworks.Winning the top prize of $20,000 was PWD – Password Manager. An iOS projec...




_r2f0ox12.jpg&width=800)