zero trust
zero trust news search results
Developer news items we found relating to zero trust
27 results
Cybersecurity supply chain risk management predictions for 2025
Thursday, January 16, 2025 by Austin Harris
DTS CEO and President Edward Tuorinsky shares his cybersecurity prediction for shaping the 2025 business landscape. Cybersecurity in 2025 is like that party game where you whisper a phrase to the person next to you. One mistake is passed along to others, with funny outcomes. The stakes are higher, and the results are less amusing when data breaches or hacks travel al...

API Security Perspectives 2025 report from Kong Inc
Monday, December 30, 2024 by Richard Harris
Kong Inc. released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report which highlights today’s API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern a...

Confidential computing will emerge as a leading force says Talentica
Wednesday, December 13, 2023 by Richard Harris
In 2024, the rise of the zero-trust paradigm will drive a significant shift in security models, with confidential computing emerging as a leading force in implementing this transformative approach. Confidential computing will emerge as a leading force In the coming year, we can expect an increase in the integration of hardware-based confidential computing as cloud...

Network-based cybersecurity threat detection SDK launches
Monday, October 16, 2023 by Freeman Lightner
Enea has launched the Enea Qosmos Threat Detection SDK. This revolutionary threat detection system has the potential to double performance in network-based cybersecurity solutions. The Qosmos Threat Detection SDK enables the integration of Enea's flagship deep packet inspection (DPI) engine, Qosmos ixEngine, with core IDS capabilities drawn from Suricata, the wid...

SQL server modernization solution from SUSE and DH2i
Friday, June 23, 2023 by Freeman Lightner
DH2i is partnering with SUSE to offer the simplest route to Microsoft SQL Server container modernization. By combining DH2i's DxEnterprise Smart High Availability Clustering software with Rancher by SUSE, organizations can seamlessly migrate both physical and virtual SQL Server databases to availability groups in Kubernetes within minutes. This collaboration em...

How people respond to ransomware attacks
Monday, April 10, 2023 by David Carvalho
Ransomware attackers extorted $456.8 million from victims in 2022, 40% down from the $765.6 million in the previous year. However, before we clink glasses to celebrate victory, there are some significant caveats to consider. The recent hack of Euler Finance where $135 million in staked Ether tokens (stETH), was drained from the protocol, is a case in point. How organiza...

SBOM mandate to improve cybersecurity in the US
Friday, March 17, 2023 by Freeman Lightner
The number of cyberattacks waged against government sectors worldwide increased by 95% in the second half of 2022 compared to the same time period in 2021. (1) The global cost of cyberattacks is expected to grow exponentially from $8.44 trillion in 2022 to $23.84 trillion by 2027. (2) To support the nation’s critical infrastructure and Federal Government networks,...

Why SonarSource is growing so much
Thursday, December 22, 2022 by Freeman Lightner
SonarSource announced record growth in developer and enterprise customer adoption. With a 43% growth in its user base, SonarSource supports more than 400,000 organizations and seven million users. The Sonar solution leads the industry with total analyzed code, which now tops more than half a trillion lines of code for organizations across the world. By adding 5,000...

EuroSTAR Software Testing Conference 2023 speaker lineup
Monday, December 19, 2022 by Brittany Hainzinger
The EuroSTAR Software Testing Conference, created in 1993, has grown to be Europe's largest gathering of software testers. Thirty editions of the EuroSTAR conference have been hosted in 16 different cities. In 2023 it will be held at Flanders Convention Center, Antwerp Zoo in Belgium, 13-16 June 2023. Software Development is a Social Activity is the theme for Eur...

Zero trust policies for software releases could be key
Thursday, December 8, 2022 by Gopinath Rebala
Today’s integrated DevOps methodology offers businesses the promise of accelerating innovation by providing customers and employees with new application capabilities faster. However, this approach can also increase risks associated with cybercrime and the failure to comply with rapidly evolving privacy regulations. As a result, minimizing security risk during the ...
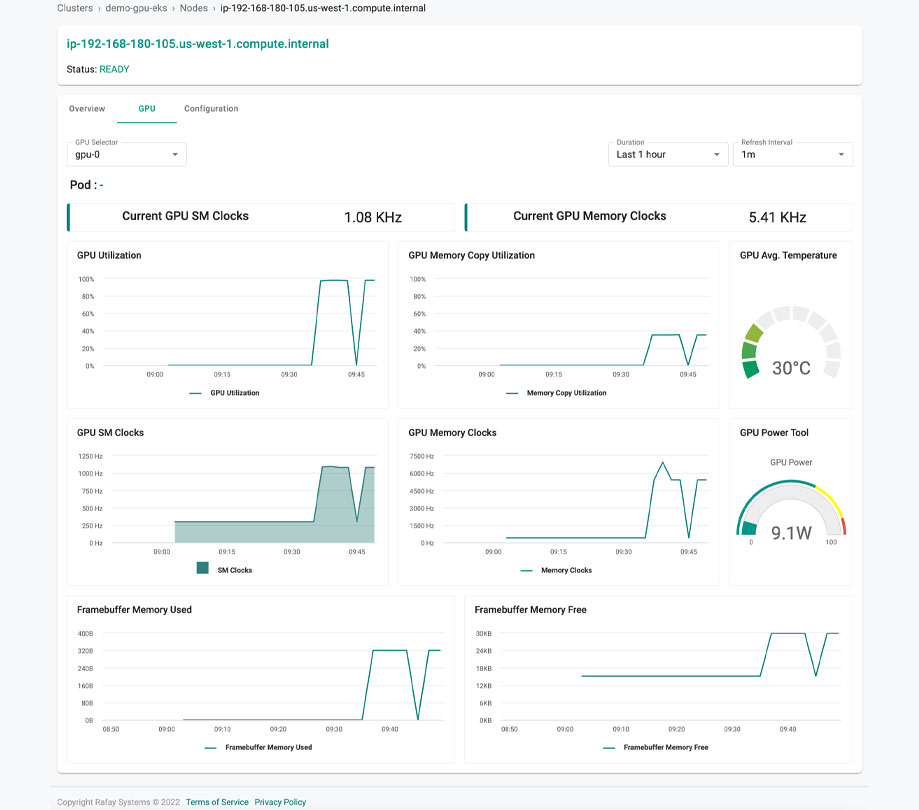
Kubernetes clusters for AI ML apps
Tuesday, March 29, 2022 by Brittany Hainzinger
Quickly launch and easily manage production-grade Kubernetes clusters for AI and machine learning applications at scale with Rafay. Rafay Systems, the platform provider for Kubernetes Operations, announced the expansion of the industry's only turnkey solution for operating Kubernetes clusters with GPU support at scale by adding powerful new metrics and dashboards...

Cloud and cyber asset management trends for 2022
Thursday, January 6, 2022 by Richard Harris
Companies have been racing to mature their technologies and pursue digital transformations in the last few years, as a way to gain or maintain competitive advantage and resilience. This has led to an emerging area of focus: cyber asset management. Organizations are now taking inventory of their IT infrastructure and prioritizing more agile cyber asset management process...

Mitigating API attacks in 2022
Wednesday, January 5, 2022 by Richard Harris
Nathanael Coffing, co-founder and CSO of Cloudentity, is also a board member. Nathanael has over 20 years of management and architecture experience across identity, security, microservices, and IT domains. Prior to founding Cloudentity, he founded OrchIS.io and helped build numerous technology startups leveraging his experience at Sun, Oracle, Imperva, Washington Mutual...
Open source services from Rafay Systems
Tuesday, October 19, 2021 by Austin Harris
Rafay Systems announced its plans to open-source its Zero-Trust Access and GitOps services. Developers will be able to take advantage of and contribute to, these battle-tested services that significantly reduce the complexities associated with securing access to and automating the ongoing operations of Kubernetes infrastructure and modern applications. These two service...

Label recognizing software updates from Dynamsoft
Monday, October 18, 2021 by Richard Harris
Dynamsoft updated its software development kit used to scan and extract content digitally from physical labels, like price and inventory tags to passports, to add automatic dictionary-based spelling correction and new image processing modes. The SDK is ideal for application developers to expand data capture capabilities of printed labels and tags in industries like auto...
Kubernetes operations platform gets more funding
Thursday, September 2, 2021 by Brittany Hainzinger
Rafay helps platform teams move beyond traditional Kubernetes cluster management to streamlined Kubernetes operations for modern applications. Rafay Systems Kubernetes operations platform gets $25M in funding Rafay Systems, the platform for Kubernetes Operations, has announced a $25 million Series B funding round led by ForgePoint Capital, with participation from ...

Zero trust framework no longer optional 2021 predictions
Tuesday, January 12, 2021 by Brittany Hainzinger
There’s no doubt that COVID-19 and the shift to remote work have accelerated Zero Trust adoption in the enterprise. In 2021 and the following years, implementing a Zero Trust approach will become essential to protecting every enterprise, regardless of industry. This is due to the increasing volume of cyberthreats that organizations and individuals face on a regula...

Zero trust security will prevail in 2021
Wednesday, January 6, 2021 by Brittany Hainzinger
Zero-trust security (when organizations stop trusting their people and services in an IT environment) will become the prevailing model for organizations in 2021. With more companies moving to distributed architectures, technology teams need a scalable way to make security foolproof while managing a growing number of microservices and greater complexity. Companies s...

GitLab acquires Peach Tech and Fuzzit
Friday, June 12, 2020 by Brittany Hainzinger
GitLab announced it has acquired Peach Tech and Fuzzit. These acquisitions will add fully-mature testing solutions including protocol fuzzing, API fuzzing, DAST API testing, and coverage-guided fuzz testing. This makes GitLab’s DevSecOps offering the first security solution to offer both coverage-guided and behavioral fuzz testing techniques as well as the fi...

Best Practices for Kubernetes deployments from Portshift
Monday, January 27, 2020 by Richard Harris
Portshift presents five security best practices for DevOps and development professionals managing Kubernetes deployments. Integrating these security measures into the CI/CD pipeline will assist organizations in the detection and remediation of security issues earlier in the development process, allowing faster and shorter cycles while assuring safe and secure deployment...

Volterra emerges from Stealth
Friday, November 22, 2019 by Austin Harris
Volterra announced it has launched from two years of stealth operations with over $50 million in funding to date. Investors include top-tier venture capital firms Khosla Ventures, Mayfield and M12 (Microsoft’s venture fund), as well as a growing set of strategic investors/partners including Itochu Technology Ventures and Samsung NEXT. Volterra’s launch come...

Zero Trust platform from Pulse Secure is enhanced
Tuesday, October 29, 2019 by Richard Harris
Pulse Secure announced that it has introduced new Secure Access management and threat mitigation capabilities within its Zero Trust Network Access platform. Through these enhancements, Pulse Secure enables enterprise and service provider organizations to progress Zero Trust security and mitigate hybrid IT risks while simplifying access to multi-cloud and data center res...

The rise of microservices with Anypoint Service Mesh
Wednesday, October 16, 2019 by Freeman Lightner
MuleSoft has announced Anypoint Service Mesh, a new solution that dramatically simplifies how companies can discover, manage and secure microservices. Anypoint Service Mesh brings security and reliability to any microservices-based application, regardless of language or deployment model, freeing developers from custom code. Customers can also now publish and discov...

Data security platform from Virtru is here
Tuesday, August 13, 2019 by Austin Harris
Virtru, a data protection platform provider that stands at the intersection of security and privacy, announced the Virtru Developer Hub, a single development portal to integrate data protection capabilities and ensure the privacy of sensitive data. Now, developers can embed platform-agnostic protection into their applications or connected devices in just a few line...

One click microsegmentation platform from Edgewise
Thursday, June 20, 2019 by Brittany Hainzinger
Edgewise Networks launched its new platform that radically simplifies the creation and management of zero trust environments with one-click microsegmentation. In seconds, companies can stop internal network attacks that have bypassed perimeter defenses. The benefits include a significantly reduced network attack surface, operational efficiency for policy creation and ma...

PCE Supercluster now offered by Illumio
Tuesday, January 8, 2019 by Austin Harris
Illumio, a cybersecurity company delivering micro-segmentation, announced full availability of PCE Supercluster designed for enterprise-scale real-time application dependency mapping and micro-segmentation deployments. PCE Supercluster, which is currently in use by some of the largest organizations in the world, makes Illumio the first company to offer a micro-segmentat...

Industrial IoT platform gets updates from Pulse Secure
Monday, December 17, 2018 by Richard Harris
Pulse Secure, a provider of Secure Access solutions to both enterprises and service providers, announced the release of Pulse Policy Secure (PPS) 9.0R3 to extend its Zero Trust Security model to IIoT devices and smart factories. The new version enables factories to streamline machinery repairs and diminish costly production downtime through IT-managed secure access...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|