spoofing
spoofing news search results
Developer news items we found relating to spoofing
17 results
Vulnerabilities in Apple products alert
Monday, September 30, 2024 by Richard Harris
CERT-In has recently issued Advisory CIAD-2024-0046, highlighting multiple high-severity vulnerabilities in Apple products. The vulnerabilities affect a wide range of Apple software, including iOS versions prior to 18, iPadOS versions prior to 18, macOS Sonoma versions prior to 14.7, macOS Ventura versions prior to 13.7, and the upcoming macOS Sequoia versions prior to ...

Geo-Fraud Detection mobile app by Appdome
Friday, August 2, 2024 by Freeman Lightner
Appdome announced it has enhanced its Geo-Fraud Detection service to include two new defenses: Geo-Location Fencing and Geo DeSync Attack Detection. Combined with other Geo-Compliance features available on the Appdome platform, mobile app developers and enterprises can eliminate location-based fraud, ensure geo-compliance and deliver location relevant use...

3D geolocation capabilities for Widow Games apps
Thursday, April 28, 2022 by Richard Harris
NextNav has partnered with Widow Games, a gaming development company closing the gap between the physical and the digital worlds. Through the partnership, Widow Games will bring NextNav's 3D geolocation capabilities to their applications, enabling more immersive virtual experiences tied to the real environments of users, and leveraging location verification to valid...
Crypto APIs launch MPC Wallet as a Service
Wednesday, November 17, 2021 by Brittany Hainzinger
The Bulgarian-based Software-as-a-Service startup Crypto APIs has launched an improved Wallet as a Service (WaaS) to provide small and medium businesses, enterprises, and institutions with a more secure and reliable multi-currency digital wallet. Crypto APIs launch MPC Wallet as a Service The service utilizes an advanced Multi-Party Computation (MPC) cryptographic...

Breakthrough in voice biometric optimization comes with IDVoice 2.11
Monday, January 27, 2020 by Freeman Lightner
ID R&D announced the newest release of its voice biometric solution, IDVoiceTM version 2.11. This release delivers a breakthrough in voice biometric optimization with an AI-based SDK of under 1MB, enabling voice biometrics to be implemented on the edge - from chips to IoT devices - for a new era of security and personalization in the voice-enabled UX. IDVoice, ID...

Mobile marketing 2019 landscape unmasked via Adjust Benchmarks
Tuesday, September 10, 2019 by Richard Harris
Adjust’s Global Benchmarks 2.0 is designed to empower marketers and publishers to better understand the mobile marketing landscape, the tool is the first of its kind to make specific KPIs, such as retention and fraud data, publicly available. The insights are based on Adjust’s aggregated database and analyze a combination of over 7,000 apps. The tool can ...

Videoselfie authentication tool launches
Tuesday, February 19, 2019 by Richard Harris
Jumio announced the launch of Jumio Authentication, a new video-selfie authentication that uses biometrics for user authentication, that could be ideal for account logins and high-risk scenarios (e.g., logging in from a foreign IP address or authorizing high-risk transactions such as wire transfers and online purchases). Secure selfie authentication can also be use...
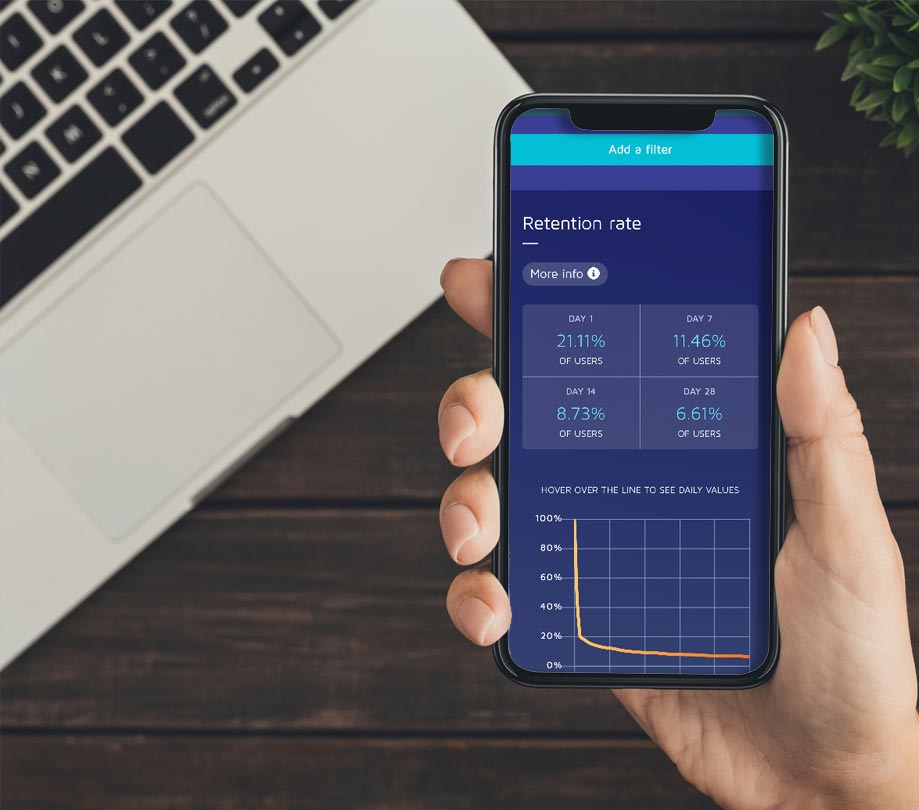
Key insights into app performance and competition from Adjust
Wednesday, December 5, 2018 by Richard Harris
Adjust recently launched the second iteration of its Global Benchmarks tool - offering an overview of the mobile marketing landscape and bringing more transparency to the industry. Based on the company’s aggregated database, Adjust’s Global Benchmarks 2.0 analyzes data from over 7,000 apps and billions of installs. It allows mobile marketers to see t...

Mobile marketing benchmark tool by Adjust brings light to marketers
Monday, November 26, 2018 by Austin Harris
Adjust announced the second version of its free mobile benchmarking tool - updated with even more sophisticated metrics and a wider range of data than before. Designed to empower marketers and publishers to better understand the mobile marketing landscape, the tool is the first of its kind to make specific KPIs, such as session data, publicly available. With time spent ...

Enterprise security report says mobile workers put data at risk
Wednesday, October 10, 2018 by Austin Harris
According to a new study titled Greatest Mobile Security Threats in the Enterprise, a significant lack of visibility into devices and networks is putting businesses at risk for data leakage and phishing attacks. The study, conducted by Enterprise Mobility Exchange and commissioned by NetMotion Software, showed that nearly 50 percent of mobile workers spend the majority ...

IDVoice biometric security update has been released
Friday, June 22, 2018 by Richard Harris
ID R&D released the newest version of its most advanced voice biometric security solution, IDVoice. Additionally, ID R&D is announcing that both IDVoice and its behavioral biometric security solution, IDBehave, are now available on the Samsung SDS Digital Identify Platform. IDVoice is a mobile-optimized voice biometric solution that authenticates users by eva...

FTP vulnerabilities and what you can do
Thursday, May 24, 2018 by Richard Harris
File Transfer Protocol or (FTP) for short is old, and when I say old - I mean 1971 old when it was initially published as RFC 114. It defines a way clients can transfer files to a server. Typically gated with a password and either sent clear text, or over SSL/TLS/SFTP, it’s a rock solid way to get files sent to their destination and is widely supported. But in today’s w...

Using common short codes for mobile app marketing
Friday, February 16, 2018 by Richard Harris
App developers know well the difficulties in marketing their apps. But a highly compelling way to advertise their apps in the context to the real world is being overlooked.Common Short Codes provide an easy way for app developers and brands to get consumers to download an app in context with their current, real-world surroundings. Common Short Codes bring integrity and ...

How to protect IP communications from telecom fraud
Thursday, December 28, 2017 by William King
Software-based IP communications continue to grow in popularity because of the added reliability, reach and control they allow businesses to have over their telecom resources. However, as more developers continue to transfer enterprise communications from legacy telcos to cloud-based service providers, the threat of telecom fraud and cyber-attacks also rise. Accord...

With TrulySecure 2.0 Developers Can Move Beyond Thumbprint Recognition
Wednesday, November 18, 2015 by Stuart Parkerson
Sensory has released TrulySecure 2.0, the next generation of the company’s FIDO Certified multimodal biometric authentication technology. This latest release builds on Sensory’s two decades of implementing platforms which enhance user experience and security for consumer electronics by incorporating state-of-the-art neural networks and machine learning principles in spe...

AGNITiO’s KIVOX Mobile SDK Combats Spoofing Through Voice Biometrics
Thursday, November 27, 2014 by Richard Harris
AGNITiO is a voice biometrics company that has developed KIVOX Mobile, a software development kit (SDK) which enables on-device secure speaker verification for the user. Users can authenticate themselves by using their voice -- authorizing any app powered by KIVOX to use a voiceprint. Users have the ability to select a passphrase which is predefined or choose...

KeyLemon Launches Cloud based Face and Speaker Recognition APIs for Development
Tuesday, October 21, 2014 by Stuart Parkerson
KeyLemon, a creator of biometric ID and motion analysis technologies, has released access to its security recognition via a web service. KeyLemon’s biometric ID provides an alternative to passcodes, key fobs or secret information to facilitate authentication and access control for online assets. Through its Okta Application Network (OAN), Okta provides the ability for u...
Featured Stories
Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp








