it security
it security news search results
Developer news items we found relating to it security
35 results
Security trade-offs and Xs vulnerabilities
Friday, March 21, 2025 by Richard Harris
The latest cyberattack on X raises an important question: Was this an external attack or a result of internal instability? While hacktivist group Dark Storm has claimed responsibility for the distributed denial-of-service (DDoS) attack, it is just as crucial to examine X’s own security posture, particularly in light of the drastic staffing cuts that followed Elon ...

AI coding security discussion with JFrog
Wednesday, February 19, 2025 by Richard Harris
Eyal Dyment, Vice President of Security Products at JFrog, shares his insights in this Q&A on the crucial considerations for developers and businesses when selecting an AI platform. With AI’s transformative role in coding and software development, Eyal addresses key security risks, the growing reliance on AI-powered technologies, and the steps developers can t...

NetLib Security predictions 2025
Thursday, January 2, 2025 by Richard Harris
The leading prediction for 2025 will sound familiar: Generative AI directly affects your privacy rights. In many ways, this is a twist on the typical cybersecurity problem. Rather than a hacker or a bad actor breaking in to steal your data, we are being asked to hand our keys to the companies we often trust the most: Microsoft, Apple, Dropbox, and Google! NetLib Secu...

API Security Perspectives 2025 report from Kong Inc
Monday, December 30, 2024 by Richard Harris
Kong Inc. released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report which highlights today’s API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern a...

Software security in 2025 - Four encouraging trends
Thursday, December 26, 2024 by Freeman Lightner
The good news is that over the last few years software development organizations have embraced their role in ensuring the security of their applications in the face of ever-increasing threats to their organizations. The bad news is that they are struggling with how to protect code without overburdening developers, slowing down releases, and generally hindering innovatio...

Why your ChatGPT app will need a no-code rescue
Wednesday, December 18, 2024 by Josh Haas
Josh Haas explains how generative AI falls short in app development, leaving founders to face challenges like iteration, security, and usability. He highlights how pairing AI with no-code platforms enables faster, scalable, and secure app creation. Why your ChatGPT app will need a no-code rescue Every day, we see YouTube videos of people using AI to turn plain English...
_7xsmrrta.jpg)
Real time security software development from Symbiotic Security
Friday, November 22, 2024 by Richard Harris
Symbiotic Security launched a real-time security for software development that combines detection and remediation with just-in-time training – incorporating security testing and training directly into the development process without breaking developers’ workflows. Backed with $3 million of seed funding from investors including Lerer Hippeau, Axeleo C...

Off-the-shelf intelligent automation beats custom ECM monitoring
Monday, October 14, 2024 by Austin Harris
The accumulation of digital information is overwhelming, and the reliance on increasing access must be recognized. The danger in this climate is that storage capacity can be quickly consumed if structured and unstructured data are not adequately managed. More storage can lead to more costs and complexity - especially regarding compliance mandates. On top of that, more t...

Generative AI in Application Security report from Checkmarx
Monday, August 12, 2024 by Richard Harris
Checkmarx, the in-cloud-native application security provider, has published its Seven Steps to Safely Use Generative AI in Application Security report, which analyzes key concerns, usage patterns, and buying behaviors relating to the use of AI in enterprise application development. The global study exposed the tension between the need to empower both...

Veracode acquires Longbow Security
Thursday, April 18, 2024 by Freeman Lightner
Veracode announced the acquisition of Longbow Security, a security risk management platform for cloud-native environments. The acquisition marks the next exciting phase of Veracode, underscoring the company’s commitment to help organizations effectively manage and reduce application risk across the growing attack surface. The integration of Longbow in...

IT security predictions for 2024 from HYCU
Tuesday, February 13, 2024 by Richard Harris
Subbiah Sundaram shares his 2024 IT predictions, plus why organizations need to make sure they have a way to protect and recover SaaS application data, the impacts LLMs and AI will have on IT security, the rise of ransomware attacks, the frequency of attacks predicted to be at every two seconds by 2030, and that the focus of organizations will shift ...

Software delivery lifecycle security predictions from OpsMx
Wednesday, December 20, 2023 by Richard Harris
Heading into 2024, enterprises face mounting security concerns related to data breaches, evolving privacy regulations, and their increasing reliance on the cloud and software service providers. As such, they are under increasing pressure to secure the software delivery lifecycle and better understand where the threats are coming from and what their vulnerabilities are. ...

AI cybersecurity impacts according to NetLib Security
Monday, December 18, 2023 by Richard Harris
This is an easy call to make: NetLib Security predicts that Artificial Intelligence - Generative AI - will continue to heavily impact the world of cybersecurity, upping the game for defensive players, while giving cybercriminals more tools on the offensive side. 2023 was a year in which AI seemed suddenly to be everywhere. Although AI is not a new field, ChatGPT and ...

Digital trust and security predictions from DigiCert
Tuesday, December 12, 2023 by Richard Harris
Mike Nelson, along with a team of experts at DigiCert looks back at the past year's security developments and makes some bold predictions of technology, identity, and digital trust. Here are DigiCert's top predictions: Prediction 1: Senior executives will become more knowledgeable about post-quantum cryptography, and companies will accelerate their investment...

API security risks report exposes Netflix and Wordpress
Monday, November 27, 2023 by Richard Harris
Wallarm, the end-to-end API and app security company, announced the release of its Q3-2023 Wallarm API ThreatStats report. The quarterly report details the surge in threats centered around APIs and uncovers critical vulnerabilities, like injections and API data leaks, that have recently impacted leading firms, including Netflix, VMware, and SAP. The new report i...

App security threat report results from Digital Ai
Thursday, October 19, 2023 by Richard Harris
Digital.ai announced the results of its 1st annual Application Security Threat Report, illuminating and quantifying the risks to applications in the wild. The results reveal that 57% of all monitored apps are under attack, with gaming (63%) and FinServ (62%) the most likely to be attacked. The study found no correlation between an app’s popularity and likelihood o...

Web3 ID to boost online security from Concordium
Wednesday, September 13, 2023 by Brittany Hainzinger
Concordium has announced the release of Web3 ID, a blockchain-native identity platform with programmable privacy for individuals and organizations. Web3 ID allows digital identity holders to issue Zero-Knowledge-Proofs to dApps while allowing dApps to seamlessly request proof of user identity. This empowers individuals and businesses with complete control over thei...

App security training enhancements by Security Journey
Wednesday, July 19, 2023 by Freeman Lightner
Security Journey announced an acceleration of its secure coding training platform enhancements. Since combining HackEDU and Security Journey training offerings into one Platform, the company has added or refreshed almost 200 lessons and 25 languages, frameworks, and technologies; giving customers even more new training content to improve secure coding knowledge gain of ...

AppSec 2023 predictions from Oxeye Security
Wednesday, February 8, 2023 by Freeman Lightner
Oxeye, the provider of award-winning cloud-native application security, announced five predictions expected to shape enterprise security spending in 2023. The predictions follow industry-wide research which shows the industry is shifting away from legacy software infrastructure and standardizing on cloud-native applications resulting in the need for new and more ef...

Security practices of apps in the Google Play Store
Monday, September 26, 2022 by Brittany Hainzinger
Data removal company Incogni analyzed the top 1,000 paid and unpaid apps available on the Google Play Store to discover the apps’ privacy and security practices. Key privacy findings: 1 in 2 apps (55.2%) share your data with third parties. Free apps share, on average, seven times more data points than paid apps. The worst categ...

ImmuniWeb Neuron web security scanning
Friday, June 10, 2022 by Richard Harris
ImmuniWeb has announced the launch of ImmuniWeb Neuron, a web application and API web security scanning solution that is based on the award-winning ImmuniWeb AI Platform available. ImmuniWeb Neuron is designed to rapidly scan tens, hundreds, or even thousands of web applications and APIs for vulnerabilities, weaknesses, and misconfigurations. It c...
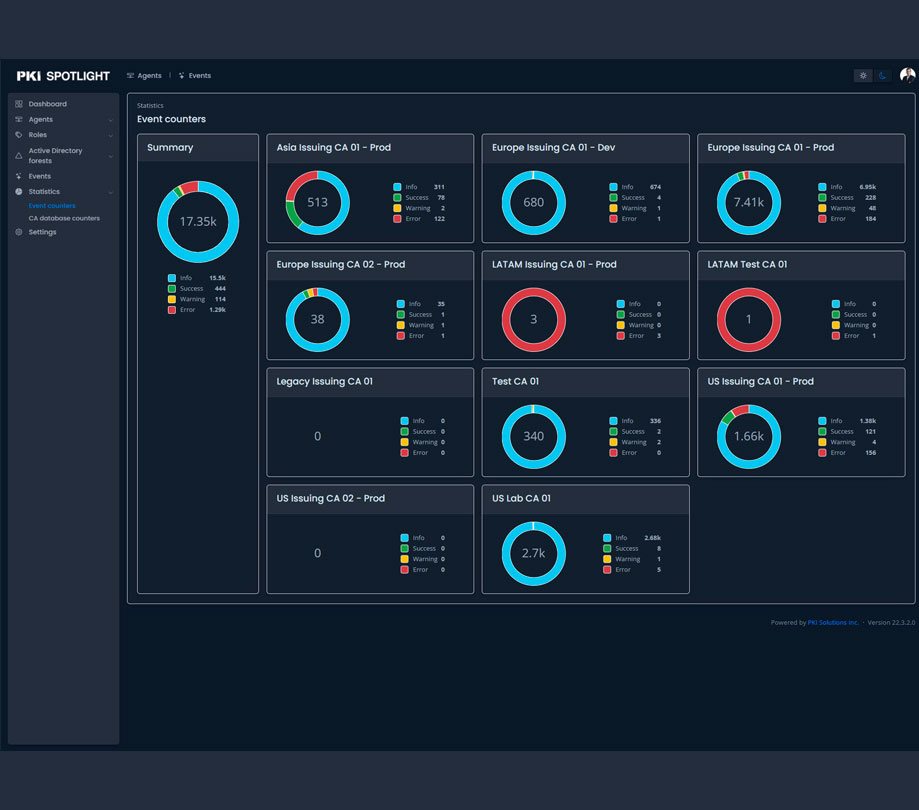
PKI Spotlight security solution launches
Wednesday, April 6, 2022 by Freeman Lightner
PKI Solutions announced the introduction of PKI Spotlight, an industry solution that provides real-time monitoring and alerting of the availability, configuration, and security of all organizations' PKI environments, all consolidated into one easy-to-use dashboard. PKI is a foundational technology for almost every identity and data encryption solution...

Why developers need security
Friday, February 18, 2022 by Ariel Shadkhan
They say that everything is personal. Well, so is code development. Since childhood, I was surrounded by developers my father was a developer, my uncle was a developer, and that was all I knew growing up. When people asked me what I wanted to do when I got older, the only answer was, well, to become a developer. Code development was very different back then, we lea...

Security compliance predictions for 2022
Tuesday, January 18, 2022 by Freeman Lightner
Edward Tuorinsky is the Managing Principal of DTS, a Service-Disabled Veteran-Owned Small Business, that provides information technology and management consulting services in the areas of program management, governance, strategic planning, organization advancement, business process efficiency, software development, system integration, and learning enhancement solutions....

Security analytics platform selects Pulumi Cloud
Monday, January 3, 2022 by Freeman Lightner
Pulumi announced Panther Labs, a security analytics platform company that helps teams detect and respond to breaches at cloud scale, has selected the Pulumi Cloud Engineering Platform to manage and scale its cloud infrastructure. With Pulumi, Panther has been able to speed its deployments by up to 10X, reduce the size of its legacy infrastructure codebase by more than 5...

App security testing platform lands from Oxeye
Monday, January 3, 2022 by Freeman Lightner
Oxeye announced the company’s Cloud-Native Application Security Testing Platform (CNAST). The new platform identifies code vulnerabilities, open-source vulnerabilities, and secrets to highlight the most critical issues in the software development lifecycle, delivering clear guidance for fast and accurate remediation. App security testing platform CNAST Accor...

Improving cloud security practices for DevOps teams
Thursday, August 26, 2021 by Richard Harris
Technology integration allows customers to securely leverage existing keys, secrets, tokens, and certificates into declarative CI/CD pipelines and ease the management of HashiCorp Vault infrastructure and security practices. Opsera and HashiCorp partner with plans on improving cloud security practices for DevOps teams Opsera, the Continuous Orchestration platform ...

Not all security vulnerabilities are created equal
Tuesday, May 25, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function, value and, unfortunately, they also provide one of the easiest openings for cybercriminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the concept o...

Six areas of focus for continuous security
Friday, April 16, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function and value and, unfortunately, they also provide one of the easiest openings for cyber criminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the conce...

Improving security posture with static application security testing
Friday, February 12, 2021 by Tim Jarrett
Amid the worldwide pursuit of digital transformation, the software has seen a meteoric rise, and application security has become paramount. As more companies become software-centric, they publish more applications, increasing the risk vulnerable code will be released. To help reduce this risk, static application security testing (SAST) can help dev teams find and fix we...

Security and reliability become one for APIs in 2021
Tuesday, January 19, 2021 by Freeman Lightner
Reliability -- especially for APIs -- is growing because our reliance on APIs is growing, while at the same time how we develop software has changed. Modern software stacks are written as a collection of microservices, with each service written in a type-safe language that better guards against low-hanging vulnerabilities. However, it also makes reasoning about how...

Security concerns will be front and center in 2021
Saturday, January 9, 2021 by Brittany Hainzinger
Security concerns, especially when it comes to cloud native applications, will be even more front and center in 2021 than they have been recently, said Linux Foundation SVP & General Manager of Training & Certification Clyde Seepersad. Recent research by The Linux Foundation and Harvard found that open source developers are not prioritizing security issu...

RPA security challenges in 2021
Thursday, January 7, 2021 by Freeman Lightner
What many security professionals have failed to realize is that the user identities created for RPA technologies to connect to a company network in order to execute a task are just as vulnerable as their human counterparts. 2021 will be the birth of digital identities for the digital workforce. RPA security challenges in 2021 Throughout 2021, identity and security...

API sprawl security concern predictions of 2021 from Volterra
Wednesday, January 6, 2021 by Freeman Lightner
As organizations continue to digitally transform business processes, they are increasingly transitioning from legacy applications to modern, cloud-native apps. These intricate modern apps feature far more APIs than their predecessors including API sprawl. Since these apps are built with extensive microservices, many of these APIs are deeply embedded and hidden. Th...

Zero trust security will prevail in 2021
Wednesday, January 6, 2021 by Brittany Hainzinger
Zero-trust security (when organizations stop trusting their people and services in an IT environment) will become the prevailing model for organizations in 2021. With more companies moving to distributed architectures, technology teams need a scalable way to make security foolproof while managing a growing number of microservices and greater complexity. Companies s...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp