device security
device security news search results
Developer news items we found relating to device security
19 results
Service mesh for all
Thursday, September 12, 2019 by Richard Harris
Kong Inc. announced the release of an open-source project called Kuma. Based on the popular open-source Envoy proxy, Kuma is a universal control plane that addresses limitations of first-generation service mesh technologies by enabling seamless management of any service on the network. Kuma runs on any platform – including Kubernetes, containers, virtual machines,...

GlobalPlatform brings trust to the IoT ecosystem
Thursday, August 29, 2019 by Richard Harris
Given the increasing need for the internet of things (IoT) device security and trust, GlobalPlatform, the standard for secure digital services and devices, has appointed a Strategic Director with significant expertise in IoT development and deployment. Chris Steck, Head of Standardization, IoT & Industries at Cisco, a full member of GlobalPlatform, will work...

Industrial IoT platform gets updates from Pulse Secure
Monday, December 17, 2018 by Richard Harris
Pulse Secure, a provider of Secure Access solutions to both enterprises and service providers, announced the release of Pulse Policy Secure (PPS) 9.0R3 to extend its Zero Trust Security model to IIoT devices and smart factories. The new version enables factories to streamline machinery repairs and diminish costly production downtime through IT-managed secure access...

New partnership emerges to simply IoT security
Wednesday, May 16, 2018 by Richard Harris
In an attempt to simplify IoT security when developing, Mocana Corporation has announced that it is partnering with Verizon to integrate Mocana’s endpoint security software solution, Mocana TrustPoint, with Verizon’s ThingSpace. Mocana TrustPoint, the company’s flagship IoT endpoint security solution, provides compliant security that protects more than 100 million ...
Overcoming IoT security threats to achieve better ROI
Monday, January 8, 2018 by Richard Harris
With B2B IoT segments expected to generate more than $300B annually by 2020, it’s no surprise that companies are rushing to build out their IoT businesses and cash in on the modern day gold-rush. However, many manufacturers are struggling to achieve long term profitability for their IoT projects beyond initial hardware sales.The key to ensuring an organization’s IoT inv...

IoT security gets tighter thanks to SDC Edge
Tuesday, December 5, 2017 by Austin Harris
StreamSets Inc. has debuted StreamSets Data Collector Edge (SDC Edge), an end-to-end data ingestion solution for resource and connectivity constrained systems such as Internet of Things (IoT) devices and the network infrastructure and personal devices that inform cybersecurity applications.SDC Edge packs the core functionality of the widely adopted StreamSets Data Colle...

Prey expands mobile device management capabilities for iOS
Wednesday, November 29, 2017 by Austin Harris
Prey Software has announced Apple Push Certification for Prey software. Organizations now have a simple path to mobile device security and management using its connection with Apple iOS for full remote control and access to Apple laptops, iPhones, and smart devices.Mobile Device Management for iOS requires the use of various digital certificates for its operation, and A...
Enterprise BYOD post holiday woes
Tuesday, January 24, 2017 by Mitch Black
Bring Your Own Device (BYOD) programs are a constant enterprise challenge. For unprepared organizations, the holidays can be especially difficult.Christmas to New Year’s Day is typically a peak time to purchase and/or download apps, so how can your enterprise effectively enroll an influx of new users and devices without compromising program security? While the recent ho...

The impact of fake retail apps hitting the Apple App Store this year
Tuesday, November 8, 2016 by Austin Harris
Holiday retail woes have hit a little early this year, with hundreds of fake retail and product apps appearing in Apple’s App Store recently. The New York Times reports counterfeiters have disguised apps as retail chains like Dollar Tree and Foot Locker, department stores like Nordstrom and even luxury brands like Jimmy Choo. With Apple known to have a st...

The Impact of BYOD on Developers
Friday, July 1, 2016 by Mitch Black
From Security Research Labs breaking into a phone within seconds on 60 Minutes earlier this year to the Apple/FBI debacle, it’s increasingly clear that enterprises have varying levels of device security protocols in place. Surprisingly, the responsibility of ensuring vital data remains secure, especially as BYOD policies and a mobile-first workforce become the norm...

Department of Homeland Security Creates Mobile Application Playbook
Tuesday, April 26, 2016 by Richard Harris
The U.S. Department of Homeland Security (DHS), Office of the Chief Technology Officer (OCTO), has created The Mobile Application Playbook (MAP), a DHS sponsored reference guide to assist federal agencies with the planning, management, and execution of mobile application projects.The MAP publication provides a roadmap for creating mobile applications and is designed to ...
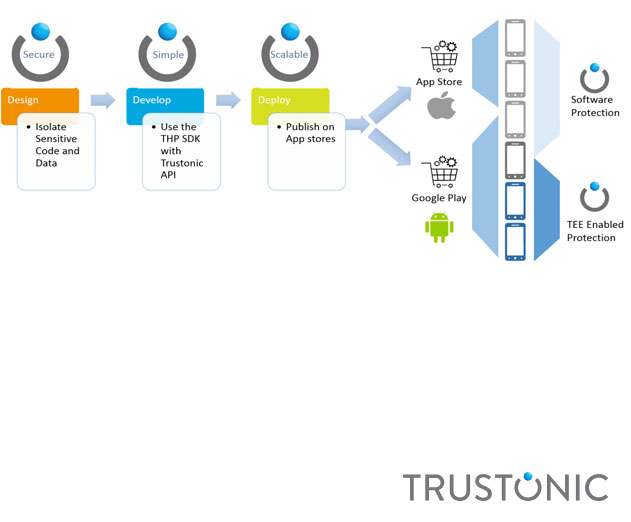
New Trustonic Platform Provides Mobile and IoT Developers with Device Security
Tuesday, February 9, 2016 by Richard Harris
Trustonic has released its "Trustonic Hybrid Protection" (THP) which offers built-in device security providing mobile and IoT developers with an adaptable security solution bringing together software and hardware secured solutions into one hybrid product. Trustonic combines advanced hardware enabled security solutions found in over 500 million devices with software...

Silicon Labs Gecko MCU Platforms Focusing on IoT Security and Energy
Tuesday, January 5, 2016 by Richard Harris
Silicon Labs has introduced two new EFM32 Gecko microcontroller (MCU) platforms that focus on security and energy management for IoT-connected devices. The new Jade Gecko and Pearl Gecko MCUs combine a hardware cryptography engine, low-energy modes, an on-chip dc-dc converter and scalable memory options. The EFM32 Jade and Pearl Gecko MCUs microcontrollers target e...

Qualcomm to Offer Malware Detection Inside Snapdragon 820 Processor
Wednesday, September 9, 2015 by Richard Harris
Qualcomm has announced the upcoming availability of Snapdragon Smart Protect which will first made available through the Qualcomm Snapdragon 820 processor. Snapdragon Smart Protect uses cognitive computing to provide real-time, on-device machine learning designed to support accurate and effective detection of zero-day malware threats for improved personal privacy and de...

New Study Finds That Risky Mobile Behavior Is Conducted By Employees
Thursday, December 4, 2014 by Richard Harris
Ponemon Institute and Accellion, Inc. have conducted new mobile research and have found that employees are participating in risky mobile behavior, with nearly 90 percent being able to access confidential information on mobile devices. The new workplace of today requires solutions which will allow employees mobile workflows that are able to introduce the security risks.&...
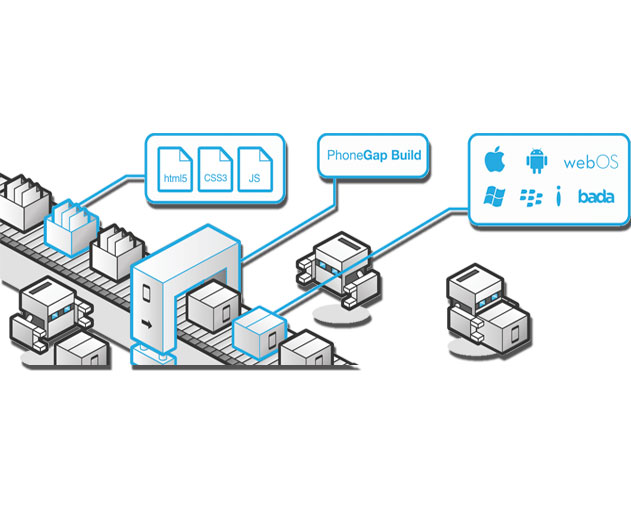
Cordova Announces Cordova 2.9, WebOS, Symbian, Blackberry and Windows Phone 7 Deprecations for PhoneGap
Tuesday, October 21, 2014 by Richard Harris
Cordova has deprecated WebOS, Symbian, Blackberry and Winphone 7, as well as for all Cordova versions below 3.0, as of October 15, 2014. The Cordova teams says that it has stopped active development on these platforms because they realized continuing support for these platforms on PhoneGap Build would mean less available resources to focus on adding new platforms o...

Five Things to Consider Before Integrating e Signatures into Mobile Applications
Thursday, October 16, 2014 by Sherry Ghafarpour
Today’s consumers can do almost anything from their mobile devices, and they expect to be able to sign documents from those devices.According to Forrester Research, customers who are comfortable with web and mobile technologies are now driving e-signature adoption. By 2020 the majority of e-signature transactions will be launched from mobile devices. This will ensure se...
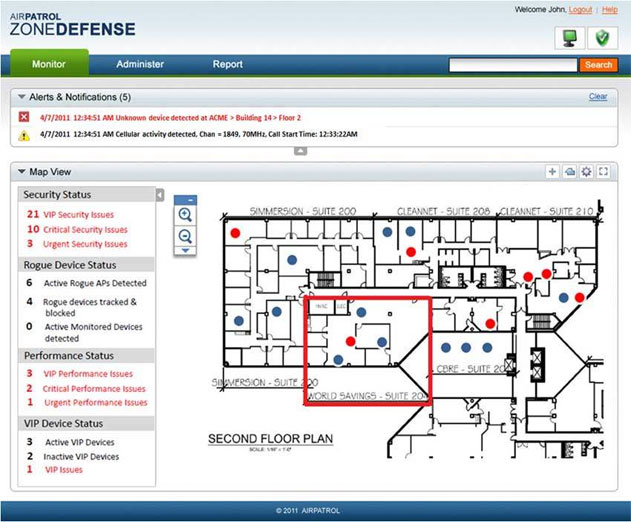
AirPatrol ZoneDefense 5 Allows Automatic Changes for Mobile Device Security Based on Location
Thursday, August 14, 2014 by Richard Harris
AirPatrol is offering a new add-in for its ZoneDefense 5 mobile device security platform that will allow organizations using the Enterprise Mobility Management suite from VMware’s AirWatch to automatically switch security policies of smartphones and tablets based on the device’s owner and location. ZoneDefense 5 allows systems administrators to create “ho...

LG Launches New webOS TV SDK Developer Site
Monday, July 14, 2014 by Stuart Parkerson
LG has launched a new webOS TV Developer Site to provide a one-stop resource center for all developer requirements for webOS TV applications. Developers can learn how to plan, design, develop and publish webOS application for the LG Smart+ TV.About the New WebsiteDevelopers can download and install the webOS TV SDK and set up the development environment. The S...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp