iOS AdThief Malware Affects Some App Revenue
Thursday, August 21, 2014

|
Stuart Parkerson |
The Virus Bulletin has posted a new update on iOS/AdThief, a.k.a. Spad, which is a piece of malware that hijacks ad revenue in jailbroken devices and redirects them to the attacker.
The Virus Bulletin reports that the malware was first noticed in March 2014. The Bulletin is now publishing a report by Axelle Apvrille which describes the malware in detail.
The report shows the iOS/AdThief malware was able to hijack advertisements from 15 different ad networks. The malware is estimated to have infected 75,000 jailbroken devices and redirecting revenue from approximately 22 million ads.
Following is an excerpt from the report:
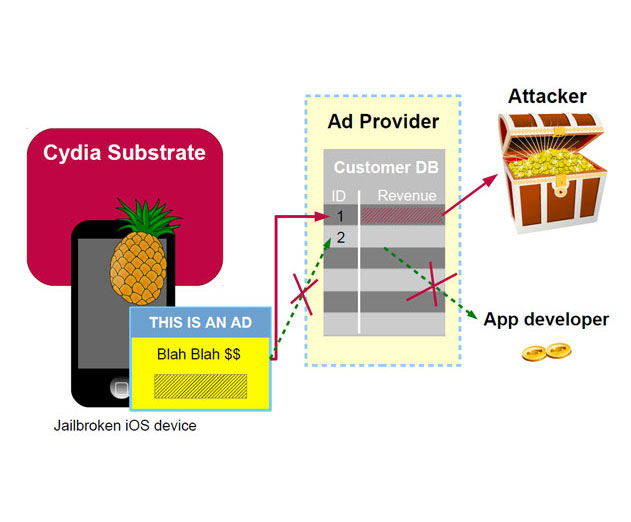
Each time an end-user views or clicks on a given advertisement, the corresponding application developer (or partner, or affiliate) receives a small payment.
This is what advertisement companies refer to as ‘cost per thousand impressions’ (CPM) or ‘click-through rate’ (CTR). To credit the right developer when ads are viewed or clicked, adkits identify developers (or partners etc.) with a developer ID.
iOS/AdThief modifies this developer ID, replacing it with an identifier owned by the attacker. Revenues are consequently hijacked, with all of the revenue generated when an ad is viewed or clicked being assigned to the attacker’s identifier.
To modify the developer ID, the malware author implements a hook for each of the adkits he wants to hijack, where he replaces the developer ID as he wishes. To do so, he takes advantage of an existing process-hooking platform, Substrate, which is available on jailbroken devices.
To modify the developer ID, the malware author implements a hook for each of the adkits he wants to hijack, where he replaces the developer ID as he wishes. To do so, he takes advantage of an existing process-hooking platform, Substrate, which is available on jailbroken devices. To implement a Substrate hook, one uses a function named ‘MSHookMessageEx’ with four arguments:
1. The class to hook.
2. A ‘selector’, i.e. the name of the function to hook.
3. The address of the replacement function, i.e. the hook.
4. A stub to call the old replaced function in case it is needed. (It may be left as NULL if not needed.)
The image shown here is from the report. The full report is available on the Virus Bulletin website.
Read more: https://www.virusbtn.com/virusbulletin/archive/201...

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here

_r2f0ox12.jpg&width=800)