misconfiguration
misconfiguration news search results
Developer news items we found relating to misconfiguration
17 results
iOS sleep app leaked sensitive user information
Tuesday, May 27, 2025 by Freeman Lightner
An iPhone app designed to combat insomnia, Sleep Journey: Insomnia Helper, exposed tens of thousands of users, revealing their names, alcohol habits, and other private data. Stress is hardly a cure for insomnia. Meanwhile, an iOS app meant to help users fall asleep could become a headache instead. The Cybernews research team discovered that Sleep Journey: Insomnia He...

API Security Perspectives 2025 report from Kong Inc
Monday, December 30, 2024 by Richard Harris
Kong Inc. released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report which highlights today’s API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern a...

AI fraud prevention solution launched
Tuesday, December 10, 2024 by Richard Harris
AppsFlyer announced the launch of an industry-leading AI enhancement layer on top of its Protect360 fraud prevention solution. Designed to address the growing challenges posed by increasingly sophisticated fraud tactics, the new AI layer leverages multiple machine learning models to deliver unmatched fraud detection and deterrence capabilities – offering customers...

Microsoft misconfigurations expose millions of records globally
Monday, November 18, 2024 by Freeman Lightner
In September 2024, significant data exposure was discovered within Microsoft Power Pages, a low-code SaaS platform, due to misconfigured access controls. The exposure, which potentially affected millions of individuals, highlights the risks associated with excessive permissions granted to the platform's "Anonymous" and "Authenticated" user roles....

ImmuniWeb Neuron web security scanning
Friday, June 10, 2022 by Richard Harris
ImmuniWeb has announced the launch of ImmuniWeb Neuron, a web application and API web security scanning solution that is based on the award-winning ImmuniWeb AI Platform available. ImmuniWeb Neuron is designed to rapidly scan tens, hundreds, or even thousands of web applications and APIs for vulnerabilities, weaknesses, and misconfigurations. It c...

Infrastructure as code announced by env0
Monday, March 15, 2021 by Brittany Hainzinger
env0 announced the company’s enterprise-grade Infrastructure as Code (IaC) automation platform featuring self-hosted agents, SAML (Security Assertion Mark-up Language) authentication support and SOC2 Type 2 certification. The enhanced platform delivers production proven remote-run workflow management and a new security framework to empower user deployments and dir...

Cloud and the future of work
Saturday, January 9, 2021 by Brittany Hainzinger
Transformation is inevitable. CDOs who can build a factory of data products and bring value in digital transformation to their shifting businesses will be heroes. They will be the people who extend an olive branch to technical audiences because data products cannot be built without technical support. The CDO will have a dual role in their company, fostering a good relat...

5 mistakes businesses make in application development
Friday, October 23, 2020 by Mayur S Shah
5 Mistakes Businesses Make While Prioritizing Speed Over Security in Application Development Earlier this year, the Democratic party in Iowa announced its plans to use a smartphone app to calculate and transmit their caucus results. One would think that by using technology to improve the speed of governance, what could possibly go wrong? A lot, apparently. The a...

2020 Cloud Misconfigurations Report released by DivvyCloud
Wednesday, February 19, 2020 by Brittany Hainzinger
DivvyCloud released its 2020 Cloud Misconfigurations Report, which substantiates the growing trend of data breaches caused by cloud misconfigurations and quantifies their impact on companies and consumers around the world. DivvyCloud research found that nearly 33.4 billion records were exposed in breaches due to cloud misconfigurations in 2018 and 2019, amounting to nea...

Best Practices for Kubernetes deployments from Portshift
Monday, January 27, 2020 by Richard Harris
Portshift presents five security best practices for DevOps and development professionals managing Kubernetes deployments. Integrating these security measures into the CI/CD pipeline will assist organizations in the detection and remediation of security issues earlier in the development process, allowing faster and shorter cycles while assuring safe and secure deployment...

PCE Supercluster now offered by Illumio
Tuesday, January 8, 2019 by Austin Harris
Illumio, a cybersecurity company delivering micro-segmentation, announced full availability of PCE Supercluster designed for enterprise-scale real-time application dependency mapping and micro-segmentation deployments. PCE Supercluster, which is currently in use by some of the largest organizations in the world, makes Illumio the first company to offer a micro-segmentat...

AIOps and why IT should care
Thursday, November 29, 2018 by Bhanu Singh
For years, industry leaders have rightfully evangelized the massive benefits of digital transformation. Abandoning outdated legacy systems and processes in favor of cloud-enabled ones helps produce greater insights, lowers operating costs, and streamlines operations for faster time-to-market of new products or services and a better overall customer experience. Already, ...

Detect eavesdropping in your mobile app with TrustKit
Wednesday, July 11, 2018 by Austin Harris
Data Theorem, Inc. announced the availability of TrustKit Analytics, a new service for the TrustKit community that delivers advanced security insights. In addition, the company announced that since TrustKit’s release in 2015, it has identified more than 100 million eavesdropping attempts on iOS and Android applications, where apps in active mode have blocked 100 p...

CloudPassage debuts Project Cielo
Monday, May 7, 2018 by Richard Harris
CloudPassage announced the beta release of its newest product built on the Halo platform, (code-name: Project Cielo), which offers complete visibility and insights into the resources in use across all cloud service providers (CSP) accounts and services within a single interface.Currently, CloudPassage's Halo platform, which includes Container Secure and Server Secure, i...

80 percent of web apps have security flaws
Tuesday, February 14, 2017 by Richard Harris
Data collected by Contrast Labs has revealed that sensitive data exposures, which include missing and weak encryption, are the top vulnerability plaguing 69 percent of web applications and accounting for 26 percent of all vulnerabilities. Their research has also found that 80 percent of tested software applications had at least one vulnerability, with an average of 45 v...

A Discussion on Container Security with Twistlock CEO Ben Bernstein
Thursday, December 3, 2015 by Richard Harris
We recently visited with Twistlock CEO Ben Bernstein to talk about his company’s Twistlock Container Security Suite and the recent announcement of its relationship with Google through the Twistlock for Google Cloud Platform integration with Google Container Engine and Container Registry.Twistlock came out of stealth earlier this year and on November 10 the company annou...
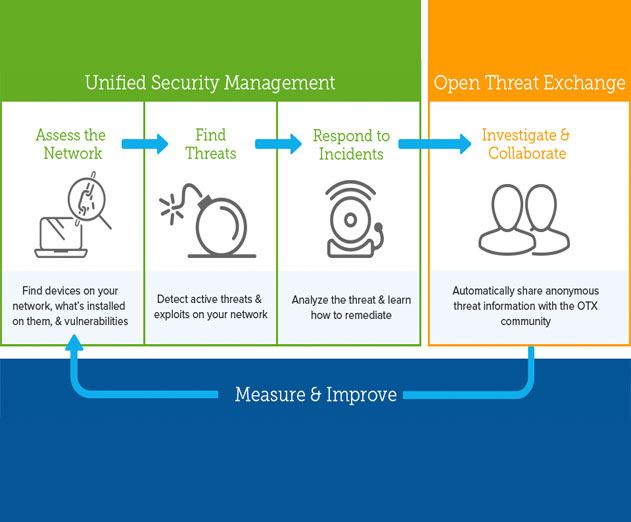
AlienVault Releases Native Solution for AWS Cloud Security and Threat Intelligence
Saturday, April 11, 2015 by Richard Harris
AlienVault has announced the general availability of AlienVault Unified Security Management (USM) for Amazon Web Services (AWS). AlienVault USM for AWS is an AWS-native solution that delivers built-in security controls and threat intelligence for IT and security teams to accelerate and simplify threat detection and incident response. USM for AWS is available on AWS Mark...
Featured Stories

Stay Updated
Sign up for our newsletter for the headlines delivered to youSuccessFull SignUp

|