New Trustonic Platform Provides Mobile and IoT Developers with Device Security
Tuesday, February 9, 2016

|
Richard Harris |
Trustonic has released its "Trustonic Hybrid Protection" (THP) which offers built-in device security providing mobile and IoT developers with an adaptable security solution bringing together software and hardware secured solutions into one hybrid product.
Trustonic combines advanced hardware enabled security solutions found in over 500 million devices with software protection technologies licensed from whiteCryption. The Trustonic Hybrid Protection defaults to use Trustonic TEE Hardware Protection whenever the hardware is available, bringing the service provider the highest level of security the device can provide.
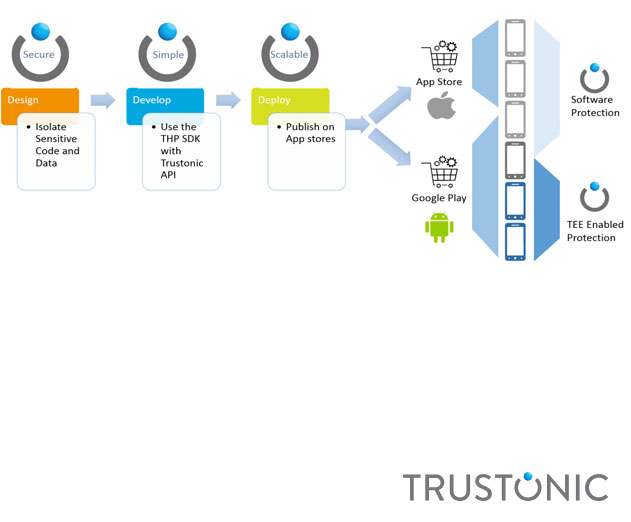
THP unifies a number of technologies under one API to simplify code development into a single source. THP uses a combination of protection technologies including:
- Unique hardware roots of trust
- Hardware based Trusted Execution Environment (TEE)
- Software code protection
- Whitebox software based cryptography
The platform provides the ability for developers to use the same source code to protect the application across all platforms. Developers only have to use a single API to protect their applications and Trustonic Hybrid Protection will select the appropriate security technique depending on the device capabilities.
Developers identify the sensitive parts of their code they would like to protect via the Trustonic API. The Trustonic Hybrid Protection SDK compiles the Trusted Application and creates different binaries for each platform. The developer then packages the Trusted Application and publishes the application on the app stores as usual.
As an additional layer of perimeter security, app developers can choose to utilize the code protection and whitebox cryptography technologies to protect the “normal” world code base. Trustonic Hybrid Protection makes it easy to protect and deploy security-demanding applications using a single tool and single API and is initially available for Android and iOS based devices.
Another aspect of THP is the simplicity of deploying “trust enhanced” apps. THP utilizes asymmetric-based cryptography combined with installation and authorization protocols familiar to any mainstream app developer. As a result service providers have both control over where their services are deployed and visibility as to the security capabilities protecting those services across their install base.
Read more: https://www.trustonic.com/products/trustonic-hybri...

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here