Valhalla blockchain game lands from Floki
Friday, July 4, 2025 by Richard Harris
Floki has announced the mainnet release of its long-awaited metaverse game, Valhalla, a blockchain-based massively multiplayer online role-playing game (MMORPG). The launch, which follows more than three years of development, marks a major step in the company’s move beyond its origins as a meme token.
Floki launches Valhalla blockchain game with multi million i...
EU says Apple breached DMA regulations
Wednesday, July 10, 2024 by Richard Harris
The AP is among outlets reporting that Apple becomes first target of EU’s new digital competition rules aimed at big tech, reporting: “European Union regulators leveled their first charges under the bloc’s new digital competition rulebook, accusing Apple of preventing app makers from pointing users to cheaper options outside its App Store. The European...
Network exposure platform from Nokia
Tuesday, June 18, 2024 by Austin Harris
Nokia announced Network Exposure Platform, a new software offering that will expand and simplify the number of APIs available to operators, their partners, and customer channels to enable the creation of network powered applications for consumer, enterprise, and industrial customers.
Nokia Network Exposure Platform (NEP) is the first implementation of the&...
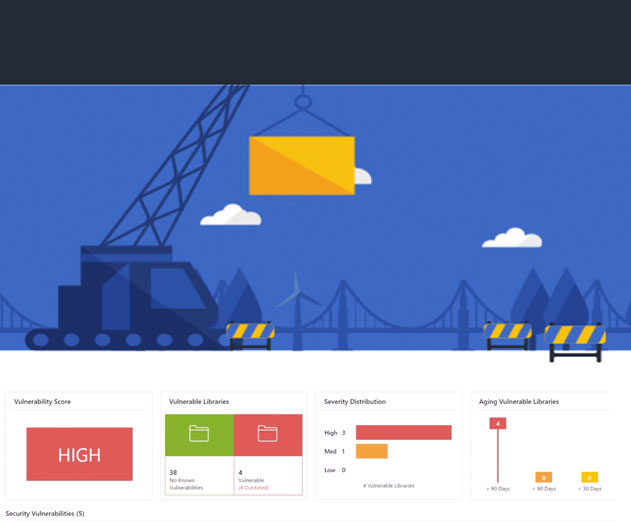
Veracode acquires Longbow Security
Thursday, April 18, 2024 by Austin Harris
Veracode announced the acquisition of Longbow Security, a security risk management platform for cloud-native environments. The acquisition marks the next exciting phase of Veracode, underscoring the company’s commitment to help organizations effectively manage and reduce application risk across the growing attack surface.
The integration of Longbow in...
Sensor network data integrity gets help from a new blockchain solution
Wednesday, November 21, 2018 by Austin Harris
Sixgill, LLC unveiled its new breakthrough blockchain or distributed ledger-based solution for sensor network data integrity. Sixgill Integrity is a ledger-agnostic solution and is designed from the ground up to solve the fundamental need for an end-to-end, real-time sensor data authenticity system. With Integrity, organizations are assured that their emitted data, tran...
Key takeaways from CA Technologies Built to Change Summit 2018
Friday, June 8, 2018 by Austin Harris
The CA Technologies’ 2nd annual Built to Change Summit(BTC) lead to the release of a whole bunch of exciting new technology and research projects pertaining to DevOps, GDPR regulations, Agile project management, and more. The overall theme of the event being to make their development platforms “frictionless” for their users, allowing them to create and...
Built to Change Summit hosted by CA happening tomorrow
Monday, June 4, 2018 by Richard Harris
CA Technologies’ (CA) will host its second annual Built to Change Summit on Tuesday, June 5th - and we'll be there! Held at its innovation and engineering hub in Santa Clara, the event brings together influential technology media and analysts from around the world with the company’s executive team and customers to discuss how organizations can win in the next wave of in...
Why developers run away from security updates
Monday, April 16, 2018 by Richard Harris
Veracode, Inc. has released new data that shines a light on the discrepancy between component security and hygiene. According to the research conducted with Vanson Bourne, only 52 percent of developers using commercial or open source components in their applications update those components when a new security vulnerability is announced. This highlights organizations’ la...
Veracode announced two new key integrations
Friday, August 11, 2017 by Austin Harris
Veracode, a software security company acquired by CA Technologies, has announced the Veracode HPE Application Lifecycle Manager (ALM) Flaw Synchronizer Plug-in, which empowers development and QA/release engineers to fix security vulnerabilities early in the Software Development Lifecycle (SDLC). The company also announced an enhanced integration to the Veracode Applicat...
DevSecOps will help security and developers play nice
Thursday, June 15, 2017 by Richard Harris
Veracode, a security software company acquired by CA Technologies, has announced the results of a study examining the relationships between application developers and security teams.The study, conducted in conjunction with Enterprise Strategy Group (ESG), shows that despite the pervasive belief that security and development teams have conflicting priorities, initiatives...
WhiteSource Bolt detects vulnerable open source components
Thursday, March 30, 2017 by Richard Harris
WhiteSource, a continuous open source security and compliance management company, has announced the launch of a new open source management tool integrated within the Microsoft Visual Studio Team Services (VSTS) and Team Foundation Server (TFS) platforms - the WhiteSource Bolt (Bolt).Bolt is fully immersed within the VSTS and TFS products, so users can detect vulnerable ...
Veracode sells to CA Technologies for $614M
Wednesday, March 8, 2017 by Austin Harris
CA Technologies announced it has signed a definitive agreement to acquire Veracode, a company that is securing web, mobile and third-party applications across the software development lifecycle, for approximately $614 million in cash. The transaction is expected to close in the first quarter of fiscal year 2018, and is subject to customary closing conditions, including ...
Three enterprise app providers that are leveraging social media
Friday, October 28, 2016 by Natalie Lambert
Let’s face it. Social media has become an integral part of everyday life, enabling near-instant communication and updates with friends located around the globe. The ease at which people can quickly pick up and learn social media apps like Facebook, Snapchat, and Twitter has not gone unnoticed by the enterprise software community, and businesses have discovered that repl...
PayStand customers can now certify and notarize payments on the blockchain
Wednesday, October 26, 2016 by Richard Harris
PayStand customers now have the option to certify and notarize payments (from request to receipt) on the blockchain to ensure that the history of payments is secure, independently verifiable, and free of tampering.Typically, certifying payment records are the domain of third party notaries or auditors. The blockchain, however, enables an independent, dec...
The use of vulnerable open source components putting more software at risk
Tuesday, October 18, 2016 by Richard Harris
Veracode has released the findings in its annual State of Software Security Report (SoSS). The seventh edition of the report presents metrics drawn from code-level analysis of billions of lines of code across 300,000 assessments performed over the last 18 months. The report revealed that the continued and persistent use of components in software development is creating ...
Catching Mobile Encryption Flaws
Tuesday, December 15, 2015 by Craig Young
More than 80-percent of mobile devices contain encryption flaws and applications written in PHP, ColdFusion and Classic ASP are most likely to have serious flaws according to a report by Veracode. These flaws in mobile apps present a grave risk for those who use them on untrusted wireless networks. The Source of the Encryption FlawsI believe that a common source of...
86 Percent of PHP Based Applications Contain at Least One CrossSite Scripting Vulnerability
Tuesday, December 8, 2015 by Stuart Parkerson
Veracode is reporting that its analytics show 86 percent of PHP-based applications contain at least one Cross-Site Scripting (XSS) vulnerability and 56 percent have at least one SQL injection (SQLi) when initially assessed by Veracode. The analysis is part of a supplement to Veracode’s “2015 State of Software Security: Focus on Application Development”, which is a repor...
IoT Provider myDevices Launches New Platform
Monday, October 12, 2015 by Richard Harris
IoT Provider myDevices develops middleware platforms and application solutions for the Internet of Things and as part of its product offering has launched a new IoT Platform as a Service. The platform combines a consumer-facing front end with data collection, analysis, and engagement tools at the back end. The customizable IoT platform is combined with professiona...