Programming
Your App is Compromised Thanks to Your Friendly Neighborhood App Hacker
Monday, August 4, 2014

|
Stuart Parkerson |

The advent of smart devices introduced a brave new world of opportunities for developers who hopped on the train and created mobile apps for iOS, Android and the other app markets.
It was and is a great opportunity for developers. Of course humans being human, where an opportunity to make money exists, the more nefarious want to get their hands in the pot. And so, mobile app hacking is now in vogue as it continuously becomes easier and faster to hack an app.
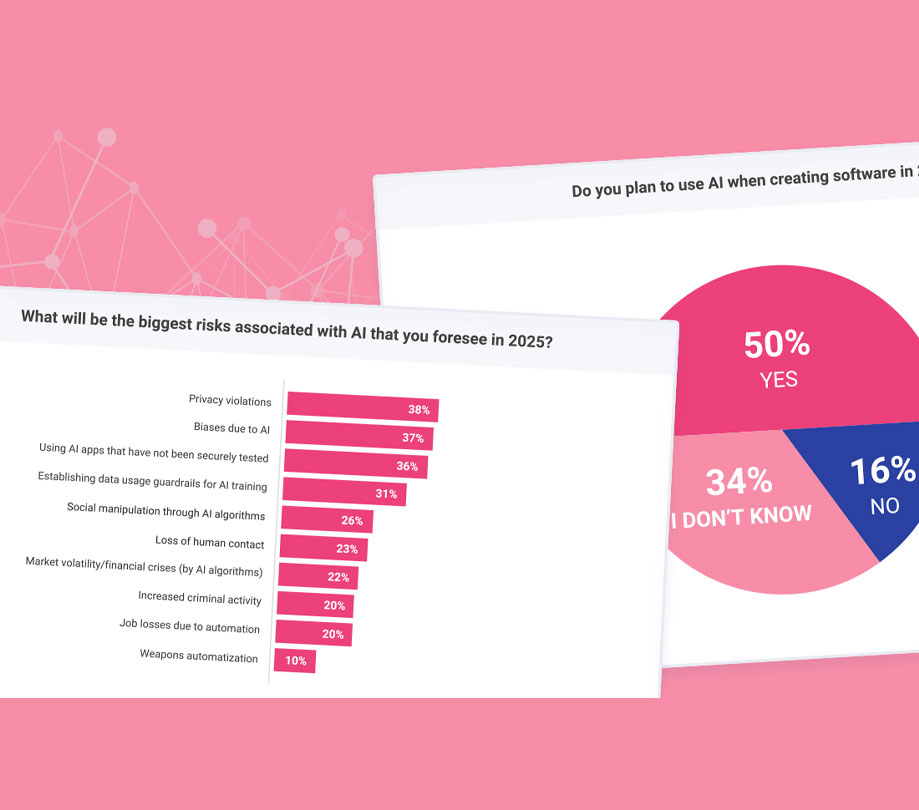
In a recent report by Arxan, the company laid out just how easy it is for app hackers to ply their trade.
Here are some reasons why:
- It’s Fast: Recent research found that in 84 percent of cases, the initial compromise took “just minutes” to complete.
- It’s Relatively Easy: There are automated tools readily available in the market to support hacking, and many of them are available for free.
- Mobile Apps are “Low-Hanging Fruit”: In contrast to centralized Web environments, mobile apps live “in the wild,” on a distributed, fragmented and unregulated mobile device ecosystem. Unprotected binary code in mobile apps can be directly accessed, examined, modified and exploited by attackers.
Arxan points out that hackers are increasingly aiming at binary code targets to launch attacks on high-value mobile applications across all platforms. Well-equipped hackers seek to exploit two categories of binary-based vulnerabilities to compromise apps:
Code Modification or Code Injection
This is the first category of binary-based vulnerability exploits, whereby hackers conduct unauthorized code modifications or insert malicious code into an application’s binaries.
Code modification or code injection threat scenarios can include:
- A hacker or hostile user, modifying the binary to change its behavior. For example, disabling security controls, bypassing business rules, licensing restrictions, purchasing requirements or ad displays in the mobile app - and potentially distributing it as a patch, crack or even as a new application.
- A hacker injecting malicious code into the binary, and then either repackaging the mobile app and publishing it as a new (supposedly legitimate) app, distributed under the guise of a patch or a crack, or surreptitiously (re)installing it on an unsuspecting user’s device.
- A rogue application performing a drive-by attack (via the run-time method known as swizzling, or function/API hooking) to compromise the target mobile app (in order to lift credentials, expose personal and/or corporate data, redirect traffic, etc.)
Reverse Engineering or Code Analysis
This is the second category of exploitable binary vulnerabilities, whereby mobile app binaries can be analyzed statically and dynamically. Using intelligence gathered from code analysis tools and activities, the binaries can be reverse-engineered and valuable code (including source code), sensitive data, or proprietary IP can be lifted out of the application and re-used or re-packaged.
Reverse engineering or code analysis threat scenarios may include:
- A hacker analyzing or reverse-engineering the binary, and identifying or exposing sensitive information (keys, credentials, data) or vulnerabilities and flaws for broader exploitation.
- A hacker lifting or exposing proprietary intellectual property out of the application binary to develop counterfeit applications.
- A hacker reusing and “copy-catting” an application, and submitting it to an app store under his or her own branding (as a nearly identical copy of the legitimate application).
There is much more to the Arxan report including 7 common techniques that hackers are using to exploit applications. Check it out.
Read more: http://appdevelopermagazine.com/partner/link/?ref=...

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here










Comments