Security
Stop the menace of Android rooting malware attacks with RASP
Monday, September 25, 2017

|
Frederik Mennes |
How Runtime Application Self-Protection is a key security measure for Android to make sure your application doesn't become compromised.
One of the key security issues facing organizations that support Android devices is the risk of rooting malware. A number of malware families on the Android mobile OS attempt to obtain root access once installed because the elevated privileges gained come in handy to perform malicious activities.
What you need to know about Tordow v2.0 and Pegasus
The Tordow v2.0 malware family, first discovered in late 2016, is a type of Android banking Trojan that attempts to steal money from the user of the infected device by stealing banking credentials, transferring money by SMS, and using its ransomware capabilities.
Recognized as the first mobile banking Trojan for the Android operating system that attempts to gain root privileges on infected devices, Tordow 2.0 typically spreads via hijacked social media and gaming applications. It collects data about the device hardware and software, operating system, manufacturer, ISP and user location. It also searches Android and Google Chrome browsers for stored sensitive information.
On the other hand, Pegasus for Android is a stealth spyware designed to monitor targets of surveillance and it is believed to have been developed by lawful intercept vendor NSO Group. The spyware reportedly uses three separate iOS vulnerabilities (or Trident) to allow an attacker to remotely jailbreak a target’s iPhone and install spyware capable of tracking every action on the device.
As a result, Pegasus can be used to remotely control a device via SMS, to exfiltrate data from commonly used communication and social media apps, to capture audio and images using the device’s microphone and camera, and to capture screenshots and other content. This spyware is so stealthy that samples of it could only be found and analysed by a joint effort of security teams at Lookout and Google.
Using Framaroot to obtain root access
Both malware families have the capability to root the device they infect, allowing users of devices and/or apps to attain privileged control or root access over Android subsystems. As Android uses the Linux kernel, rooting an Android device gives similar access to administrative (superuser) permissions as on Linux or any other Unix-like operating system. Administrative rights allow the malware samples to perform a much wider range of nefarious actions, such as accessing other apps’ data, recording key strokes, or reading SMS messages.
Reverse-engineering of some samples of these malware families shows that they rely on the exploits packaged in Framaroot to try to gain root. Framaroot, which describes itself as a one-click app to root some devices, does exactly what it claims and works for a wide range of devices running Android 2 to 4. In practice, Framaroot is used by most malware families to perform rooting.
Indeed, some Tordow v2.0 samples contain the actual Framaroot framework:
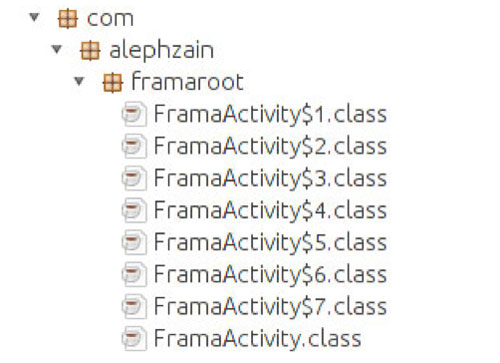
Protecting against Android rooting malware using RASP
Pegasus also uses Framaroot, as it comes with the sucopier file, the publicly available Framaroot exploit binary.
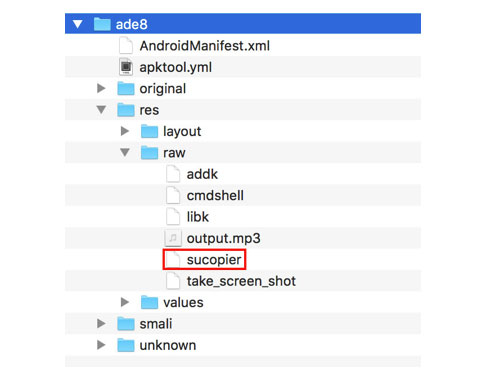
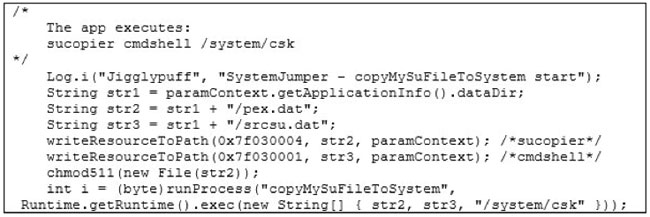
Now, what happens after one of the exploits of Framaroot was successfully run on a device? In order to ease subsequent root accesses by the malware, an su binary is written to a directory, from where it can later on be executed. In our context, an su binary, sometimes described as super user, is used to execute commands with the super user privileges.
In the case of Pegasus, the su binary (the cmdshell file in the apk) is located at /system/csk on the file system. This unusual location grants the malware the exclusivity of root access and supposedly guarantees that it remains hidden.
There is, however, a way to detect rooting and protect your organization and mobile application users from malicious attacks - Runtime Application Self-Protection (RASP).
To protect mobile devices against rooting malware, organizations should focus on the application layer. A key way of doing so is with Runtime Application Self-Protection (RASP), which protects apps as they run by providing security mechanisms such as integrity protection, debugging prevention, root detection, and more. RASP offers advanced root detection to detect the presence of binaries like those in Tordow v2.0 and Pegasus.
From its position inside the application, RASP understands the data flows and working logic of the app, and continuously monitors and analyzes application execution in the background. That means that RASP also knows when the application is under threat.
If a user runs an app that is protected with RASP on a device that is not rooted at first but becomes rooted through infection by malware, RASP will take action to protect the app and user. For instance, RASP could inform the user via a warning message, alert the information security team of the organization, or terminate the app.
Malware attacks against Android devices highlight the need for technology like RASP that provides one-stop protection against rooting malware. It’s important that the root detection and prevention features of RASP technology are continuously updated by testing it against root, root cloaking, and malware applications. This is instrumental to ensure RASP stays ahead of the most advanced rooting malware. To find out more about RASP, download a whitepaper on why RASP is critical for mobile app security.
This content is made possible by a guest author, or sponsor; it is not written by and does not necessarily reflect the views of App Developer Magazine's editorial staff.

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here









