Security
IT Governance of Sensitive Files on Corporate and BYOD Mobile Devices
Monday, June 20, 2016

|
Jeff Steuart |

Mobile content has brought new agility and efficiency to just about every enterprise. "Mobile communication and collaboration is accelerating and improving enterprise productivity and growth like no other universal technology since the dawn of the Web 25 years ago,” says Josh Bohls, Founder, Inkscreen.
But these advantages come at a cost.
Says Bohls, “Ask any organization’s IT manager, compliance officer or C-level executive what keeps them up at night, and loss of market confidence, competitiveness and compliance resulting from a mobile data breach is near the top of the list."
Managing scanned documents and captured images and audio is important for most businesses. Mobile has made it challenging for management and IT departments to enforce policies on the use of mobile data, such as whether/what content can be shared by end users and their mobile devices.
Virtually every smartphone and tablet has apps that can easily scan images, capture PDFs, take photos, and record video and audio, all of which accelerate and advance business processes. In our case as commercial real estate developers, this means sending construction site photos to architects, developers and the trades to quickly resolve issues and questions before delays and costs can mount.
But mobile sharing can also increase the risks of accidental misuse, inappropriate sharing and unapproved access due to situations such as a successful cyber-attack on a recipient’s company, for example. Confidential or sensitive business data could be exposed to loss, theft and misuse, so governing and protecting mobile data is clearly crucial.
Yet it’s also it's important – and especially in BYOD situations – to give IT departments ways to do their job protecting company assets, without over-reach that impacts the individual employee’s personal content or device or that introduces usability complexities, that might drive a user to a “shadow IT” mindset.
For mobile content on both corporate-issued and BYOD mobile devices, businesses need the ability to:
- Block files from going to unauthorized cloud repositories, third-party applications and other un-managed devices.
- Comply with data protection and privacy regulations and their industry’s standards for data governance.
- Secure at-rest data, whether on mobile devices or in the data center.
- Secure data in transit.
- Establish and enforce policies to promote productivity while protecting against data leakage.
- Balance business and personal considerations to avoid over-restricting employees, a key driver of Shadow IT.
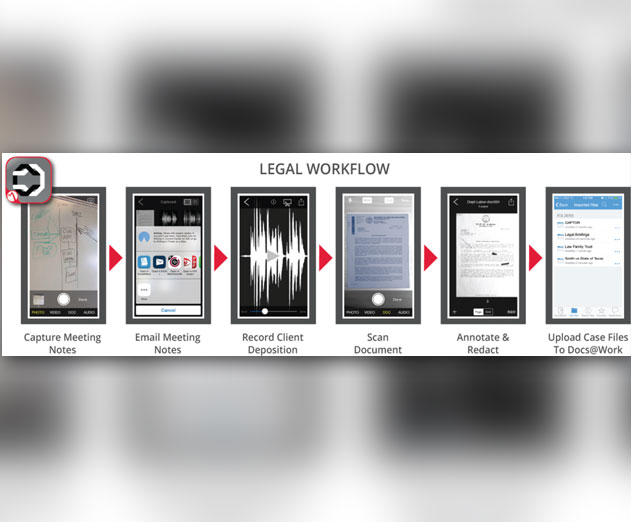
That security and balance have so far been elusive - an array of vendors have approached various solutions. The latest is Inkscreen, whose CAPTOR app is geared to providing IT with new mobile data policy enforcement and governance capabilities.
It promises to centralize control over the capture, security and governance of sensitive business content, including pictures, videos audio recordings, and scanned documents. It lets IT define sharing privileges with other apps and users, and back content up to a secure corporate database for archiving and ongoing enterprise content management. CAPTOR works whether the organization is using enterprise mobility management (EMM) solutions such as Mobile Iron or Good Technology, or not.
Inkscreen’s objective is seamless, containerized IT-driven security and management of mobile business content throughout its entire life cycle: capture, storage, collaboration, exchange, archiving - accomplished without affecting the employee’s personal devices or content.
The app is designed for any organization with mobile assets, and is believed to be especially well suited to security-driven and regulated environments such as healthcare, insurance, finance, construction/engineering, manufacturing, etc. It promises to help close some of mobile's most gaping security holes.
Read more: http://appdevelopermagazine.com/partner/link/?ref=
This content is made possible by a guest author, or sponsor; it is not written by and does not necessarily reflect the views of App Developer Magazine's editorial staff.

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here









Comments