AI integration challenges software developers
Wednesday, March 13, 2024 by Richard Harris
The promise and perils of Artificial Intelligence (AI) has been dominating the headlines with everyone from software developers to students working on ways to integrate it into their daily processes. This burgeoning interest in AI is borne out by the fifth annual Reveal 2024 Top Software Development Challenges survey, which found that the biggest software development ch...
AI app development assistant lands from NodeSource
Thursday, November 30, 2023 by Richard Harris
NodeSource, the Node.js observability, application management, monitoring, and security platform, announced the launch of the N|Solid Copilot, an AI assistant integrated into the Console of N|Solid Pro. Leveraging the N|Solid Pro platform to capture the most detailed telemetry for applications and paired with the company’s Node.js experts and OpenAI, the...
Detect hard coded secrets with new capabilities from Cycode
Thursday, August 10, 2023 by Freeman Lightner
Cycode announced the expansion of its hard-coded secrets detection in cloud-based workplaces, as well as a collaboration with Azure DevOps pipelines to ensure end-to-end supply chain integrity and a new IDE plug-in for seamless integration with VS Code.
Building upon its existing code-to-cloud coverage, Cycode now extends its secrets scanning capabilities to encompas...
SBOM mandate to improve cybersecurity in the US
Friday, March 17, 2023 by Freeman Lightner
The number of cyberattacks waged against government sectors worldwide increased by 95% in the second half of 2022 compared to the same time period in 2021. (1) The global cost of cyberattacks is expected to grow exponentially from $8.44 trillion in 2022 to $23.84 trillion by 2027. (2) To support the nation’s critical infrastructure and Federal Government networks,...
Open Bug Bounty has fixed 1 million vulnerabilities
Monday, November 7, 2022 by Brittany Hainzinger
Open Bug Bounty is an open, disintermediated, cost-free, and community-driven Bug Bounty platform for coordinated, responsible, and ISO 29147 compatible vulnerability disclosure. It passed the milestone on 27 October of fixing over 1,000,000 web security vulnerabilities.
The Open Bug Bounty project enables website owners to receive advice and support from&n...
Software company LeanIX celebrates 10th anniversary
Friday, February 4, 2022 by Richard Harris
LeanIX celebrates 10 years in business this month. An international success story, LeanIX has quickly earned the trust of 650 customers, including more than 10 percent of the Global 500, and serves 150,000 users worldwide. This 10th anniversary follows a year that saw LeanIX continue to grow at 60%, successfully complete a major acquisition (Cleanshelf), sign ...
Software cyberattack predictions for 2022
Tuesday, January 4, 2022 by Richard Harris
Nigel Thorpe hails from a software development background and moved to the IT security industry with Entrust Technologies during the early days of PKI. His knowledge has benefited a number of security companies in the UK, Canada, and the USA, and he now serves as Technical Director at SecureAge Technology. With a wide range of experience in different business environmen...
Oxeye closes a $5.3 Million seed financing round
Thursday, November 4, 2021 by Brittany Hainzinger
Oxeye announced the closing of a $5.3 Million seed financing round led by MoreVC, a seed-stage venture capital fund in Israel. The latest round includes support from i3 Equity Partners, and other cybersecurity focused investors as the company prepares to protect the world’s most popular Web applications with next-generation cloud-native Application Security Testin...
Promon partners with F5 to simplify mobile SDK integration
Wednesday, October 27, 2021 by Christian Hargrave
Promon, the Oslo-based app security company announced its partnership with F5, the multi-cloud application security and delivery company. This partnership now enables F5's customers to seamlessly implement the F5 Bot Defense Mobile SDK. The solution provides developers with the necessary tools to protect their applications from bot attacks utilizing Promon'...
Network visibility improves with Endace and Kemp Technologies
Tuesday, August 24, 2021 by Brittany Hainzinger
Endace and Kemp Technologies have announced a technology partnership to help security, network, and application teams dramatically reduce network investigation and incident response times while improving accuracy.
Network visibility improves, helping teams reduce incident response times
The enhanced network flow metadata generation and intelligent traffic mon...
2021 hackathon from NEAR
Friday, August 13, 2021 by Freeman Lightner
NEAR announced the first in a series of NEAR MetaBUIDL hackathons with $1 million in prizes until the end of the year. The first MetaBUIDL Hackathon runs from Aug 27 to Sep 12. Registration is open now.
Speakers and Activities at the 2021 hackathon from NEAR
They think it's a great opportunity for anyone interested in solving real-world problems that coul...
Kubernetes for the enterprise as Canonical sees it
Tuesday, August 10, 2021 by Richard Harris
Nearly five years ago, throngs of people in cities across America started roaming streets, parks, and other places to hunt down creatures on their cell phones. The launch of Pokémon GO on July 5, 2016, created a craze, peaking at 45 million daily users and smashing previous estimates of player traffic.
Behind the scenes, a new open-source technology played a p...
Faster customer integrations from HackerOne
Thursday, July 29, 2021 by Freeman Lightner
Tray.io has announced that HackerOne is using Tray Embedded to develop and deliver powerful customer integrations at scale. With Tray Embedded, HackerOne quadrupled its integration delivery speed to maximize developer efficiency and reduce the integration maintenance burden. Armed with seamless integrations, HackerOne customers can spend less time context-switching...
Not all security vulnerabilities are created equal
Tuesday, May 25, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function, value and, unfortunately, they also provide one of the easiest openings for cybercriminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the concept o...
5 mistakes businesses make in application development
Friday, October 23, 2020 by Mayur S Shah
5 Mistakes Businesses Make While Prioritizing Speed Over Security in Application Development
Earlier this year, the Democratic party in Iowa announced its plans to use a smartphone app to calculate and transmit their caucus results. One would think that by using technology to improve the speed of governance, what could possibly go wrong? A lot, apparently. The a...
GitLab acquires Peach Tech and Fuzzit
Friday, June 12, 2020 by Brittany Hainzinger
GitLab announced it has acquired Peach Tech and Fuzzit. These acquisitions will add fully-mature testing solutions including protocol fuzzing, API fuzzing, DAST API testing, and coverage-guided fuzz testing. This makes GitLab’s DevSecOps offering the first security solution to offer both coverage-guided and behavioral fuzz testing techniques as well as the fi...
Iowa caucus app woes from a developer perspective
Friday, February 21, 2020 by Richard Harris
Whether the issues behind the Iowa Democratic Caucus app debacle were specific to UX, connectivity, traffic, or just good ol’ fashioned reluctance to embrace the technology, the ramifications of this mess will be felt for a long time – the hanging chad of the new decade. So are apps out? Absolutely not, but things are going to have to change.
Applications...
Gitlab 12.0 released
Friday, June 28, 2019 by Christian Hargrave
GitLab is releasing 12.0 to help enterprises transform and accelerate DevOps adoption by bringing developers, operations professionals, and the security team together in the first single application for the entire DevSecOps lifecycle. With the 12.0 release, GitLab is building upon security features recently released - such as security dashboards, auto remediation and se...
Blockchain development with strong APIs
Monday, January 21, 2019 by Richard Harris
2018 was the year of blockchain “pilot” projects - where companies began to truly explore all of the possibilities of the technology. For example, in PwC’s 2018 survey of 600 executives, 84 percent said their organizations had at least some involvement with blockchain technology - but only 15 percent reported having gone live.
As we jump into 2019, ...
UN commission sets cyber security regulations for Europe
Wednesday, January 9, 2019 by Christian Hargrave
The United Nations Economic Commission for Europe (UNECE) has confirmed it will integrate the widely used ISA/IEC 62443 series of standards into its forthcoming Common Regulatory Framework on Cybersecurity (CRF). The CRF will serve as an official UN policy position statement for Europe.
At its recent annual meeting in Geneva, UNECE’s Working Party on Regulatory...
Gamification can transform your software security program
Tuesday, December 18, 2018 by Pieter Danhieux
No matter the organization, or indeed their individual circumstances, there is one problem I have identified time and time again over the course of my career: AppSec managers, CISOs, CIOs and cybersecurity experts all over the world are rarely able to positively engage their dev teams on security best practice and training. It’s a source of conflict between teams,...
IAST supports AppSec efficiencies while cutting costs and headaches
Monday, November 26, 2018 by Asma Zubair
It’s easy to feel passionate about interactive application security testing (IAST) in the world of application security. You see, IAST makes security testing almost invisible. It’s not something that requires a highly trained team to be brought in to carry out and analyze testing results. It doesn’t hold up other teams or processes from moving forward....
Single Page Application security help
Tuesday, October 23, 2018 by Richard Harris
Single-page applications, or SPAs, are web apps that load a single HTML page and dynamically update that page as the user interacts with the app. Their origins are unclear but the concept was discussed as early as 2003 according to the archives on Wiki. SPAs use AJAX and HTML5 to create fluid and responsive Web apps, without constant page reloads - that literally means,...
Open Source security comes to GitHub
Thursday, August 16, 2018 by Richard Harris
Sonatype announced Sonatype DepShield, a new GitHub application that enables developers to experience basic open source security governance, free of charge. Powered by Sonatype’s OSS Index, DepShield integrates directly into GitHub repositories and allows developers to easily identify and avoid using open source components with known vulnerabilities.
“The...
FTP vulnerabilities and what you can do
Thursday, May 24, 2018 by Richard Harris
File Transfer Protocol or (FTP) for short is old, and when I say old - I mean 1971 old when it was initially published as RFC 114. It defines a way clients can transfer files to a server. Typically gated with a password and either sent clear text, or over SSL/TLS/SFTP, it’s a rock solid way to get files sent to their destination and is widely supported. But in today’s w...
npm@6 package manager brings new security features
Wednesday, April 25, 2018 by Christian Hargrave
npm, Inc. has announced npm@6, a major update to its JavaScript software installer tool with new security features for developers who work with open source code. npm@6 will be included as part of the Node.js v10.x release line, and leverages the assets of the Node Security Platform, the definitive source of JavaScript vulnerabilities, recently acquired by npm, Inc.In an...
Sonatype expands firewall to stop dev vulnerabilities
Friday, March 9, 2018 by Christian Hargrave
Sonatype has announced that the Nexus Firewall is now available to support the more than 10 million developers currently using the open source version of Nexus Repository. Previously only available to commercial users of Nexus Repository Pro, the newest version of Nexus Firewall gives all Nexus Repo users the ability to automatically stop vulnerable open source componen...
Rethinking DevOps as DevSecOps
Thursday, October 12, 2017 by Akshay Aggarwal
If you’re not already thinking right now that your DevOps teams should be run like a DevSecOps team, you may already be in a world of hurt. Time to wake up! As the adoption of APIs continues to grow, so do the risks to organizations that don’t actively test the security of their solutions. Modern Agile development frameworks have changed the way engineering teams produc...
Kony introduces us to AppPlatform V8
Thursday, August 24, 2017 by Richard Harris
Businesses big and small are feeling the mounting pressure of increasing demand by their clients, employees and partners for mobile apps. Many of them struggle to meet this demand. Especially with limited budgets and lack of in-house developer skills, which seem to be the biggest hurdles.To help solve this mobile app dilemma, Kony recently launched its Kony AppPlatform ...
Veracode announced two new key integrations
Friday, August 11, 2017 by Christian Hargrave
Veracode, a software security company acquired by CA Technologies, has announced the Veracode HPE Application Lifecycle Manager (ALM) Flaw Synchronizer Plug-in, which empowers development and QA/release engineers to fix security vulnerabilities early in the Software Development Lifecycle (SDLC). The company also announced an enhanced integration to the Veracode Applicat...
Why runtime application selfprotection is critical for app security
Tuesday, June 20, 2017 by David Strom
Today most of us go about implementing security from the outside in. The common practice is to start by defining a perimeter and trying to defend it with various security tools. Even though perimeters have been porous for more than a decade, we still can’t give up this notion that if we build a better wall we can keep our enterprises safer.Certainly that is where most e...
The Netflix hack: A chat about securing your company
Wednesday, May 10, 2017 by Richard Harris
As the digital transformation progresses onwards, the unfortunate side effects are becoming blatantly obvious in the news. It seems like every other day that some new big box company, political party, or individual has their information compromised. But even though only the few biggest companies get the real media attention, hundreds of millions of hacking attempts are ...
Catching up with Red Hat Mobile to talk about low code in the enterprise
Tuesday, April 25, 2017 by Richard Harris
Low code is a movement that has emerged in the marketplace in recent times, not only for mobile but also for business process management (BPM) and other application development areas. What company can resist the pull of low-cost and relatively fast development times? Especially when it's as simple as a drag and drop gesture away. So it's not surprising that many big nam...
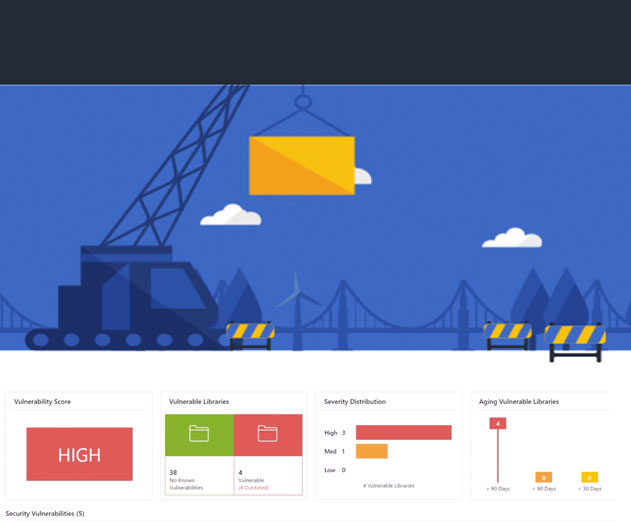
WhiteSource Bolt detects vulnerable open source components
Thursday, March 30, 2017 by Richard Harris
WhiteSource, a continuous open source security and compliance management company, has announced the launch of a new open source management tool integrated within the Microsoft Visual Studio Team Services (VSTS) and Team Foundation Server (TFS) platforms - the WhiteSource Bolt (Bolt).Bolt is fully immersed within the VSTS and TFS products, so users can detect vulnerable ...
The biggest delays in digital transformation initiatives
Tuesday, March 14, 2017 by Richard Harris
We recently caught up with Robert Reeves, co-founder and CTO of Datical, a provider of database release automation solutions, on the findings of a recent survey - conducted by IDG and commissioned by Datical - that reveal the biggest delays in digital transformation initiatives. ADM: When on the road to digital transformation, what causes the biggest speed bumps?Reeves:...