App security threat report results from Digital Ai
Thursday, October 19, 2023 by Richard Harris
Digital.ai announced the results of its 1st annual Application Security Threat Report, illuminating and quantifying the risks to applications in the wild. The results reveal that 57% of all monitored apps are under attack, with gaming (63%) and FinServ (62%) the most likely to be attacked. The study found no correlation between an app’s popularity and likelihood o...
Ransomware prevention platform ProLion sees large increase in revenue
Monday, October 24, 2022 by Freeman Lightner
ProLion has recorded an 80 percent increase in revenue for FY2022, driven by the addition of over 250 new customers worldwide. The uplift has been driven by demand for its ransomware protection solution CryptoSpike, which has soared as a result of the rise in ransomware and ransomware-as-a-service attacks.
The company also reported a renewal rate of 89...
IP blocking warning when preventing click fraud
Friday, July 29, 2022 by Freeman Lightner
Click fraud is a massive problem, stealing tens of billions of dollars from advertisers every year. The fraudsters responsible for this crime include technically savvy website owners, transnational organized crime gangs, and even Nasdaq-listed multinationals.
The scam works like this: criminals create websites, and contact advertising networks like Microsoft Ads to r...
Triller calls on US gov to ban TikTok
Tuesday, July 19, 2022 by Freeman Lightner
Triller calls on CFIUS, President Joe Biden, Congress the Department Of Defense to ban TikTok calling it the largest security threat to America today in an open letter by CEO and Chairman of Triller Mahi De Silva.
As the CEO of a global company whose mission is to help creators take control of their destiny in the creator economy, leveraging transformative adaptive t...
Hacking phones worry us the most
Thursday, July 14, 2022 by Freeman Lightner
Search results for 'smart appliances' have increased by 300% as people are becoming reliant on devices that promise to make their life easier.
Alarmingly, a recent report by Which revealed that a home with smart gadgets could be vulnerable to 12,000 hacking attacks in a single week.
Intrigued by this, BespokeSoftwareSolutions utilized the online analy...
Quantum computing learning platform launches
Monday, April 18, 2022 by Brittany Hainzinger
Q-CTRL announced the release of Black Opal Pro, an upgraded and expanded version of its world-first interactive quantum computing learning platform. Black Opal Pro adds new modules and features to the basic version announced in November 2021, which already has 3,000 registered users.
The announcement arrives on World Quantum Day, an international initiative dedi...
Protecting source code
Wednesday, October 6, 2021 by Nigel Thorpe
Earlier this year, EA (Electronic Arts), reported a cyberattack and the theft of some 780GB of source code for games such as FIFA 21 and the proprietary Frostbite game engine used for many other high-profile games such as Battlefield. The threat actors responsible for the EA data breach put the stolen data up for sale on an underground hacking forum for $28 million, pro...
Quantum computing company receives over $9M in funding
Thursday, August 26, 2021 by Richard Harris
Quantum Brilliance, a venture-backed Australian-German full-stack quantum accelerator startup, has announced closing a USD$9.7 million seed investment co-led by the QxBranch founders’ and Main Sequence investment consortium.
Quantum Brilliance harnesses synthetic diamonds to build quantum accelerators that do not require near absolute zero temperature or comple...
Six areas of focus for continuous security
Friday, April 16, 2021 by Jack Mannino
Applications are the heart of employee and user productivity. There are billions of applications each with a specific function and value and, unfortunately, they also provide one of the easiest openings for cyber criminals and hackers to gain access to critical IT infrastructure and information assets. While most IT security professionals implicitly understand the conce...
Low power cellular IoT chipset launched by Sony
Thursday, February 25, 2021 by Brittany Hainzinger
Sony Semiconductor Israel (Sony) announced the launch of the Altair ALT1255, a new low-power NB2 chipset. The ALT1255 is 5G ready, designed with an integrated SIM (iSIM), user MCU, rich application layer, and GSM/GPRS fallback modem.
The ALT1255 chipset empowers device manufacturers to develop low-power, cost-sensitive connected devices at a global scale to mo...
DevSecOps will go mainstream this year
Tuesday, January 26, 2021 by Richard Harris
Cybercriminals love Shadow Code exploits because hacking a commonly used library or service can place the malicious code on hundreds or thousands of websites. For example, the widely used jQuery JavaScript library has been breached multiple times, leading to digital skimming attacks broadly across the e-commerce sector. Adding jQuery to an application without ...
To encrypt or not encrypt legacy devices no longer a choice
Thursday, March 19, 2020 by Freeman Lightner
Encryption forms a strong layer of protection for our data and a last line of defense against cybercrime. By deploying encryption, users can render their data unreadable if it is compromised. Whether that means hackers intruding into the network, or an employee unwittingly exposing sensitive information, the data will be useless to any unauthorized agents who happe...
Linux Foundation open sources Project OWL
Tuesday, March 10, 2020 by Richard Harris
The Linux Foundation announced Project OWL’s IoT device firmware effort will be hosted at the Foundation and is inviting developers worldwide to build mesh network nodes for global emergency communications networks. Project OWL, the winner of Call for Code 2018, is a cloud-based analytics tool that helps facilitate organization, whereabouts, and logistics for disa...
Ushur Managed Package launched on Salesforce AppExchange
Thursday, February 20, 2020 by Brittany Hainzinger
Ushur announced it has launched the Ushur Managed Package on Salesforce AppExchange, empowering enterprises to add customer engagement automation capabilities to their Salesforce platform. Ushur’s artificial intelligence (AI) platform enables enterprises to instantly and intelligently automate interactions with their customers, integrating directly into Sale...
Adjust to launch Control Center as part of Automate Suite
Tuesday, February 18, 2020 by Freeman Lightner
Adjust announced the launch of its pioneering new product, Control Center, which will be part of the Adjust Automate suite. With its release, Adjust aims to dramatically simplify the process of mobile advertising management for today’s marketers.
Mobile has become the new undisputed king of digital, and eMarketer predicts marketers are poised to invest a record...
Dangers of quantum hacking
Tuesday, February 11, 2020 by Richard Harris
Active Cypher has built a password-hacking quantum computer to demonstrate the dangers of quantum hacking.
Using $600 worth of hardware parts easily purchased online or at a local electronics store, Active Cypher’s founder and CTO, Dan Gleason, created a portable quantum computer dubbed QUBY (named after qubits, the basic unit of quantum information). QUBY runs...
Post-quantum computing security
Wednesday, November 6, 2019 by Richard Harris
There is a brewing fear about Quantum computing because of the power behind moving quantum bits around in such blinding speeds that some say, will instantly break every encryption algorithm on the Internet today. DigiCert Inc. has released the results of a new survey titled, "Quantum's Peril & Promise" that highlights the ...
Two strategic advisors join Findora
Friday, August 16, 2019 by Richard Harris
Findora, the cryptographically transparent public blockchain for building decentralized financial applications, has two new strategic advisors; Balaji Srinivasan, former CTO of Coinbase, and Professor Dan Boneh, Head of Stanford Cryptography.
Prior to joining Coinbase, Srinivasan was General Partner at Andreessen Horowitz, and co-founder of Earn.com,&...
Warnings for aircraft cybersecurity
Thursday, August 1, 2019 by Brittany Hainzinger
The Department of Homeland Security issued a security alert for small planes, warning that modern flight systems are vulnerable to hacking if someone manages to gain physical access to the aircraft. Engine readings, compass data, altitude and other readings “could all be manipulated to provide false measurements to the pilot,” according to the DHS alert.&nbs...
API security testing just got easier with 42Crunch's new scanner
Thursday, March 21, 2019 by Richard Harris
42Crunch officially released the 42Crunch API Platform, an API security cloud platform to discover vulnerabilities in APIs and protect them from attack. The 42Crunch Platform can protect SaaS, Web, or IoT APIs, as well as microservices.
This follows the launch of the free API Contract Security Audit tool at APISecurity.io earlier this month. The tool helps API d...
Data science and the currency of the future
Wednesday, February 6, 2019 by Richard Harris
A recent study performed by IDC and Seagate forecasted that by 2025, global data will grow to 163 zettabytes. For scale, that’s approximately 1 trillion gigabytes per zettabyte. As the amount of available data grows, businesses are clamoring for larger and larger pieces of the pie. However, when it comes to leveraging data, success doesn’t rest on the quanti...
Wireless Gecko portfolio cuts WiFi power consumption in half
Monday, January 28, 2019 by Richard Harris
Silicon Labs expands its groundbreaking Wi-Fi portfolio of modules and transceivers, enabling developers to create end node products with best-in-class power efficiency, superior RF blocking performance and advanced security. Designed for the specific needs of IoT applications, the Wireless Gecko portfolio cuts Wi-Fi power consumption in half compared to competitive off...
Gamification can transform your software security program
Tuesday, December 18, 2018 by Pieter Danhieux
No matter the organization, or indeed their individual circumstances, there is one problem I have identified time and time again over the course of my career: AppSec managers, CISOs, CIOs and cybersecurity experts all over the world are rarely able to positively engage their dev teams on security best practice and training. It’s a source of conflict between teams,...
ALM data strategies that mimic the principles of blockchain
Friday, November 2, 2018 by Christopher Pola
All too often, I hear from customers about a very common pain point: they do not have the data to run their business. It’s not that they lack data, but they lack trust in their data. While solving data issues can be a riddle at times, I believe this dilemma is symptomatic of antiquated and/or misappropriated application lifecycle management (ALM) systems requiring...
Machine learning, crowdsourced data, and the birth of Gengo.ai
Wednesday, October 31, 2018 by Richard Harris
The glue that holds machine learning and artificial intelligence together is data. Without the data to create complex learning algorithms from, and to create those life-like AI experiences - neither of them are worth a brass farthing.
Charly Walther, the VP of product and growth at Gengo.ai, joined Gengo from Uber, where he was a product manager in Uber’s Advan...
DuckDuckGo vs. Google vs. Privacy
Friday, October 19, 2018 by Richard Harris
Online privacy is becoming harder to find - Facebook gathers users’ data to sell to third parties, Google tracks everyone’s searches, ISPs in many countries gather communication data, and governments are increasingly demanding backdoor access to encrypted devices. In the latest news, Google exposed the data of 500,000 Google+ users and didn’t...
Blockchain IoT can work to your advantage
Friday, October 5, 2018 by Richard Harris
Why do the words Blockchain and IoT still sound terrifying to some businesses? Maybe it's because Blockchain terminology was made mainstream by Bitcoin, or perhaps it's that IoT sounds immediate security alarms.
According to IBM, using Blockchain in asset management, customs declarations, supply chain networks, commercial property leasing, and countless more ...
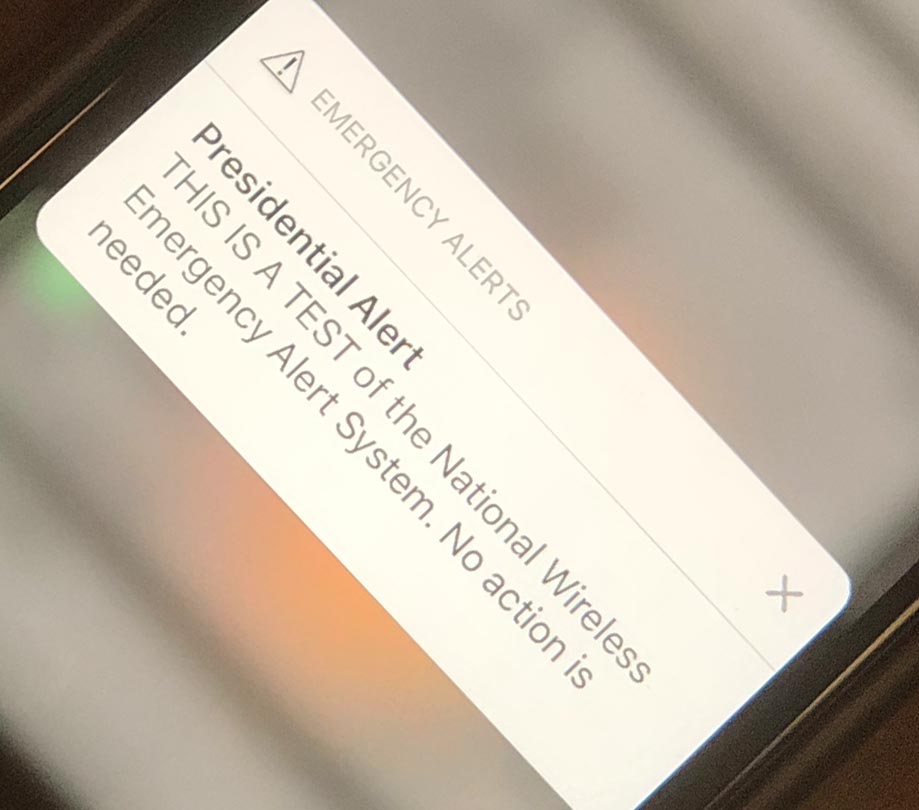
Presidential Alerts and the future of mobile communication
Thursday, October 4, 2018 by Richard Harris
FEMA has sent their first emergency test message to all of the mobile devices throughout the United States. They reported every American who owns a smartphone - which is about 75% of the population, should have received the test alert. In total the message went out to a total of 225 million devices right around 1:18 PM CST reading "Presiden...
Top ten ICO scams that swindled over $687M
Friday, September 28, 2018 by Richard Harris
Initial Coin Offerings are one of the most tempting investment options for those hoping to profit from the ever-evolving world of cryptocurrency. However, the lack of regulation has allowed ICO investors to become targets of sneaky schemes.
Though ICOs have snowballed, with more than 750 being invested in during 2018 alone, the number of scams has also steadily risen...
Decentralized application development boosted with Lisk Core 1.0
Thursday, August 30, 2018 by Richard Harris
Lisk commenced the official release of Lisk Core 1.0 to its Mainnet following a period of rigorous testing and development. By utilizing sidechain technology written in JavaScript, Lisk’s Sidechain Development Kit (SDK) will enable developers to build scalable decentralized applications on blockchain, including deploying their own custom tokens.
Commenting...
Merged mining partnership between Bitmain and Elastos
Tuesday, August 28, 2018 by Christian Hargrave
Elastos (ELA) announced a merged mining partnership with Bitmain Technologies. The merged mining partnership means that for miners and future users of the smart web platform, it guarantees the security of the Bitcoin network by sharing its hashpower. Merged mining allows Bitcoin (BTC) and the ELA coin to be mined simultaneously and more efficiently, and conserves energy...
A quantum blockchain can stop quantum computing from hacking it
Monday, August 13, 2018 by John Wu
We have yet to see the full promise of Blockchain play out but companies and scientists are already close to launching a technology that could theoretically break it: quantum computers.
Such machines can compute data exponentially faster than traditional computers. Earlier this year, Google began testing Bristlecone, a quantum computer chip that its creators think wi...
Questioning the future of privacy and the safety of personal identity
Thursday, June 28, 2018 by Richard Harris
While consumers and businesses expand their use of social media and electronic services to record levels, many of America’s most knowledgeable security professionals don’t believe that individuals will be able to protect their privacy and online identity, even with precautionary measures and new regulations such as GDPR.
These findings and more are outlin...
New partnership emerges to simply IoT security
Wednesday, May 16, 2018 by Richard Harris
In an attempt to simplify IoT security when developing, Mocana Corporation has announced that it is partnering with Verizon to integrate Mocana’s endpoint security software solution, Mocana TrustPoint, with Verizon’s ThingSpace. Mocana TrustPoint, the company’s flagship IoT endpoint security solution, provides compliant security that protects more than 100 million ...
CEO Roundtable participants announced for Telecom Exchange NYC 2018
Wednesday, May 9, 2018 by Christian Hargrave
Jaymie Scotto & Associates (JSA), founder and host of the C-Level networking event series, the Telecom Exchange (TEX), announced its CEO Roundtable participants and topics for its 2018 TEX NYC event, taking place June 19-20 in Hoboken, NJ. The event will feature four CEO Roundtables, providing a major platform for tech, telecom and content thought leaders to deliber...